Observed Exploitation Attempts of Struts 2 S2-066 Vulnerability (CVE-2023-50164)

Introduction
Apache Struts is a powerful open source web application framework that is used by companies and organizations around the world. Apache Struts has been a prime target for hackers because of its popularity. When a critical remote code execution (RCE) vulnerability is announced, security and IT teams must take immediate action to protect their systems.
On December 7, 2023, CVE-2023-50164 was published. The vulnerability allows an attacker to manipulate file upload parameters to enable path traversal and upload a malicious file. This can result in the attacker gaining complete control of the system.
On December 11, the first proof-of-concept (PoC) exploits were published and made widely available. Exploitation attempts followed shortly thereafter, on December 12 (Figure 1).
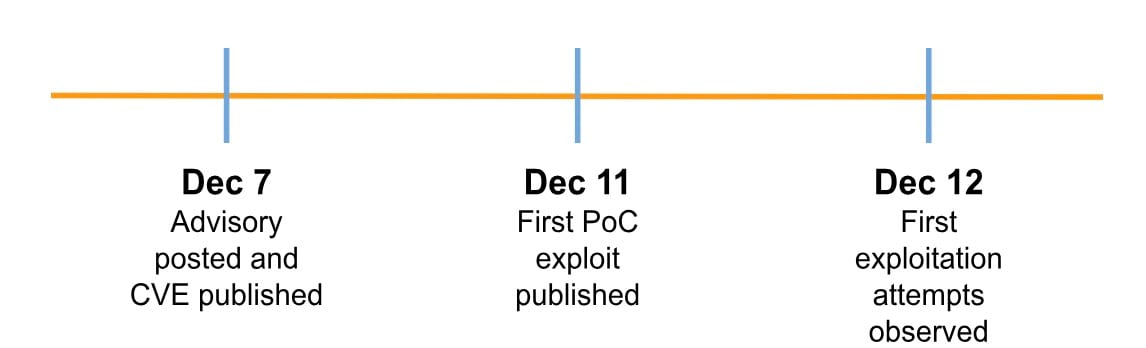 Fig. 1: Struts 2 S2-066 vulnerability timeline of events
Fig. 1: Struts 2 S2-066 vulnerability timeline of events
About the CVE
CVE-2023-50164 represents a critical vulnerability discovered within Apache Struts 2, which is an open source framework that is widely used for developing and building Java EE web applications. Apache Struts, renowned for its robustness and flexibility, plays an important role in the architecture of numerous commercial and open source web projects. This makes the vulnerability a matter of significant concern across various sectors, including key industries such as finance, healthcare, and government services.
The core issue of CVE-2023-50164 lies in its potential for RCE through a path traversal flaw. Specifically, it exploits the way Apache Struts framework handles file uploads. By manipulating the file upload parameters, an attacker can effectively traverse the web server's directory structure without authorization.
This traversal allows the placement of malicious files, typically Java Server Page (JSP)–based web shells, into directories or locations that are not originally intended for, nor accessible to, user uploaded file content. The exploit depends on the ability to bypass server-side security mechanisms in a way that was not anticipated by the application developers.
The attack process
The attack process is as follows:
1. The attacker performs reconnaissance first and identifies a website or web application that uses a vulnerable version of Apache Struts and the file upload URL path.
2. The attacker prepares a malicious file, usually a JSP file or web shell.
3. The attacker then crafts a special request to upload the file. This request includes manipulated data, such as the file's name and path, thereby manipulating the file upload parameters.
4. In the upload request mentioned in step 3, the attacker includes system commands that exploit the path traversal vulnerability. These commands instruct the server to place the file outside the normal upload directory. This is the path traversal stage.
5. The attacker sends the upload request to the server running the vulnerable versions of Apache Struts. If this is successful, the server saves the malicious file or web shell in a location or directory where it can be executed.
6. The attacker then accesses the uploaded malicious file through a web browser or an automated script. Accessing this file triggers the execution of the malicious code or web shell on the web server.
7. Once the code is executed in step 6, the attacker can perform additional actions on the server. These could range from stealing sensitive data, modifying website content, to taking full control of the web server.
8. Depending on the attacker's intentions or motivations, they might maintain covert access for future exploitation or to use the compromised server to launch further attacks.
The implications
The implications of CVE-2023-50164 are far-reaching. RCE vulnerabilities are among the most severe and critical threats in web applications, as they allow attackers to execute arbitrary commands on an affected server. This could lead to unauthorized access, data theft, and, potentially, a full system compromise.
The widespread integration of Apache Struts amplifies these risks, making CVE-2023-50164 a high-priority issue for organizations worldwide.
Observed exploitation attempts
On December 12, one day after the PoC exploit became widely available, we started to see exploitation attempts similar to the published PoC exploit (Figure 2). Although these attack attempts are real, it is not likely they would succeed. For the attack to be successful, the targeted endpoint must possess file upload functionality.
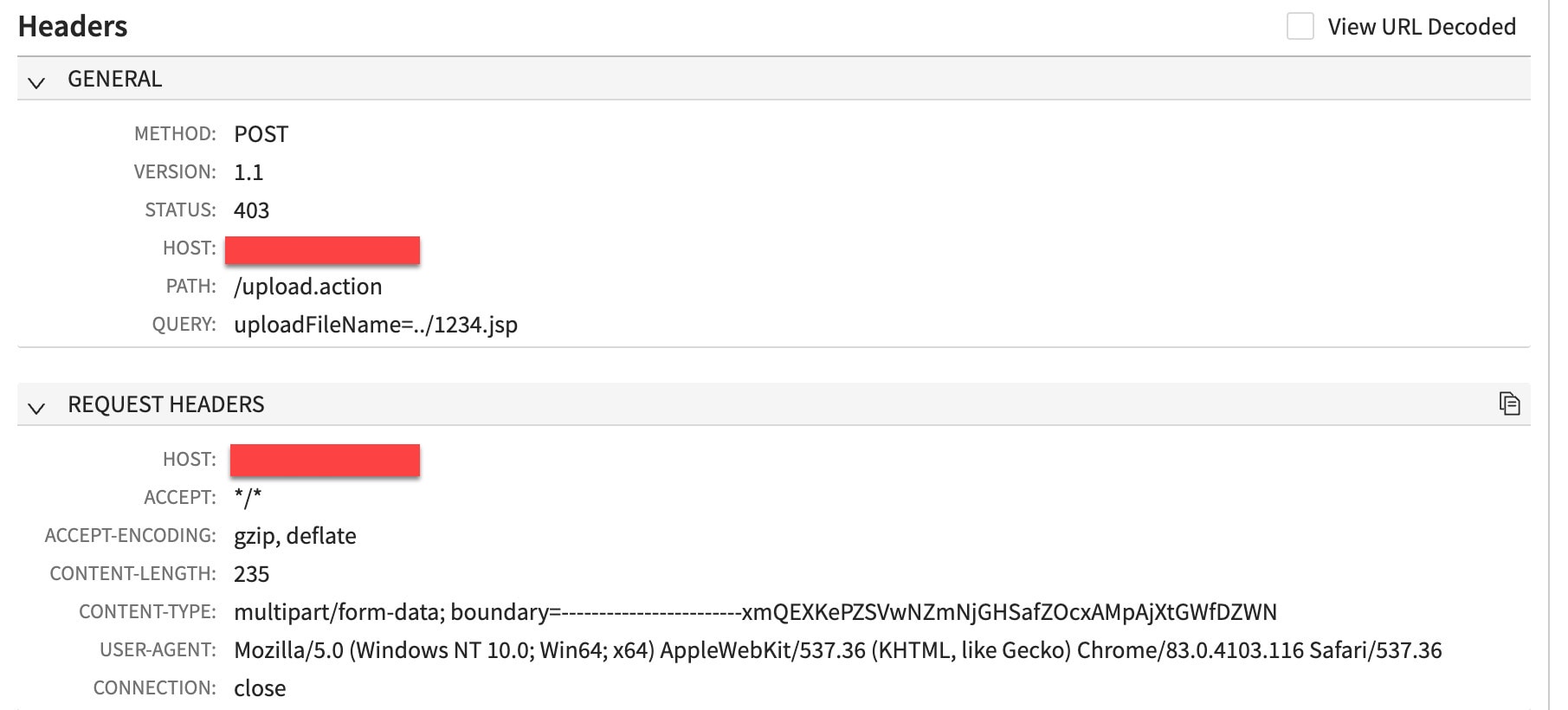 Fig. 2: Exploit variant 1, which resembles the published PoC exploit
Fig. 2: Exploit variant 1, which resembles the published PoC exploit
In addition to the expected PoC scanning, we have started to see requests that seek to exploit this vulnerability which do not match the published PoC. This variant is targeting the path /s2/upload.action rather than the original /login.action (Figure 2). Interestingly, the parameter name “fileFileName” is being used to include the path traversal which differs from the original “uploadFileName”.
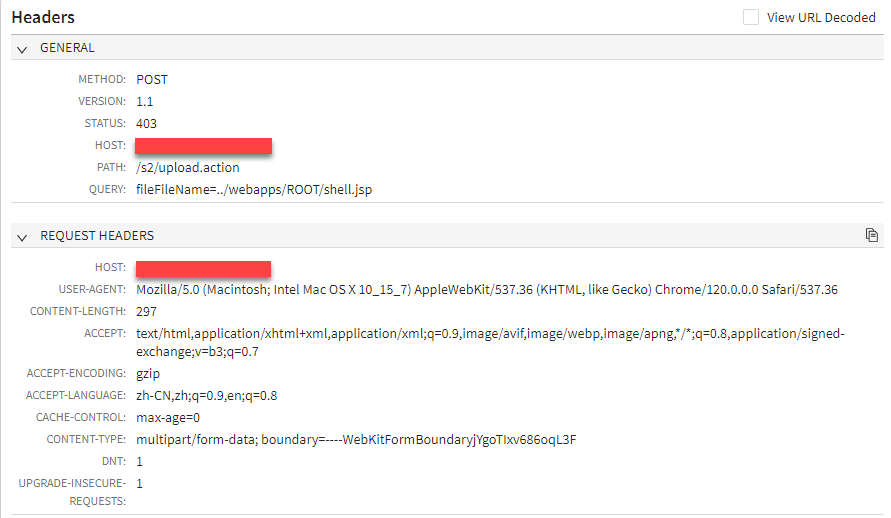 Fig: 3: Exploit variant 2
Fig: 3: Exploit variant 2
It is not clear whether these endpoints have file upload functionality. We are seeing the same variant 2 exploitation attempts from a group of IPs targeting many different customers.
The Akamai Security Intelligence Group will continue to analyze our web application firewall (WAF) logs for new variants and will update this section of the blog with any new information.
Mitigating with App & API Protector
Customers who are using Akamai Adaptive Security Engine in automatic mode and have the “Web Platform Attack” group in Deny mode are automatically protected against these attacks. Customers who are using Adaptive Security Engine in manual mode should validate that they have the “Web Platform Attack” group or the following individual rule in Deny mode (Figure 4):
3000929- Apache Struts Path Traversal and File Upload Attack Detected (CVE-2023-50164)
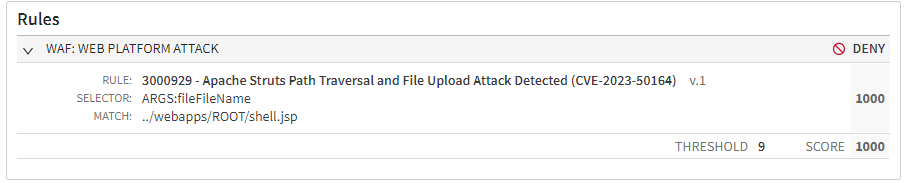 Fig. 4: Exploit attempt denied by Adaptive Security Engine rule
Fig. 4: Exploit attempt denied by Adaptive Security Engine rule
Summary
Akamai App & API Protector has been successfully mitigating these attack attempts against our security customers. Additionally, we haven't been able to conclusively determine if the targeted endpoints actually possess file upload functionality; therefore, we haven't observed any subsequent post exploitation actions that attackers might undertake following a successful attack.
Although the most effective defense is to promptly update the source code, we recognize the immense effort it requires for security teams to swiftly identify and safely update vulnerable components. This challenge is compounded by the ever-increasing number of applications, and the dynamic nature of these environments.
The adage “security is in layers” may seem cliché, but it's crucial to consider additional complementary methods to enhance overall security. Attackers are rapidly adapting to new public PoCs, often within 24 hours, which significantly increases the challenge for defenders.
Implementing a WAF, like Akamai App & API Protector, can serve as an additional layer of defense, which can protect against newly discovered CVEs and provide an extra buffer of security.









