To download the Infection Monkey, please submit the form at right. We will provide you with the files and an installation guide.

Unleash the Infection Monkey in your network and discover security flaws in no time.
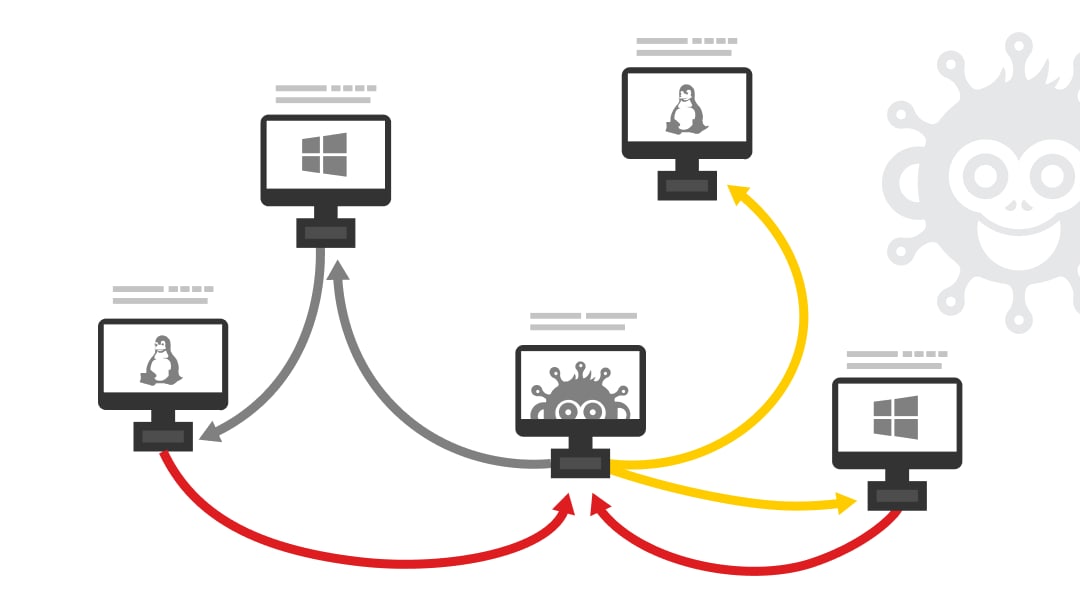
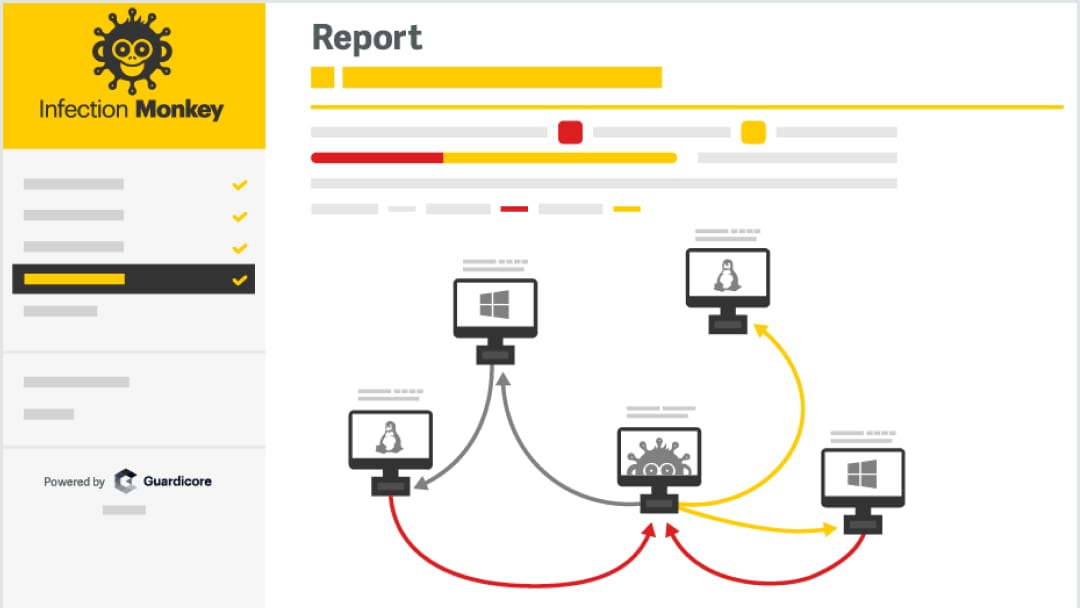
• Overview of immediate security threats and potential issues
• A map of your network with a breakdown of breached machines
• Open services uncovered to reduce attack surface
• Per-machine mitigation, e.g., segmentation, password configuration





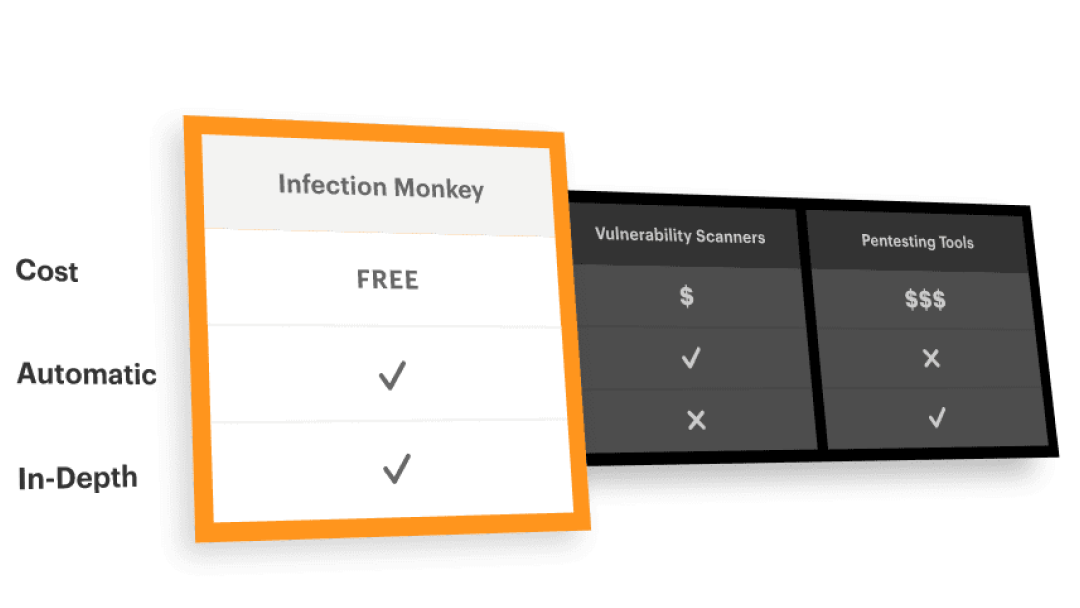
To download the Infection Monkey, please submit the form at right. We will provide you with the files and an installation guide.