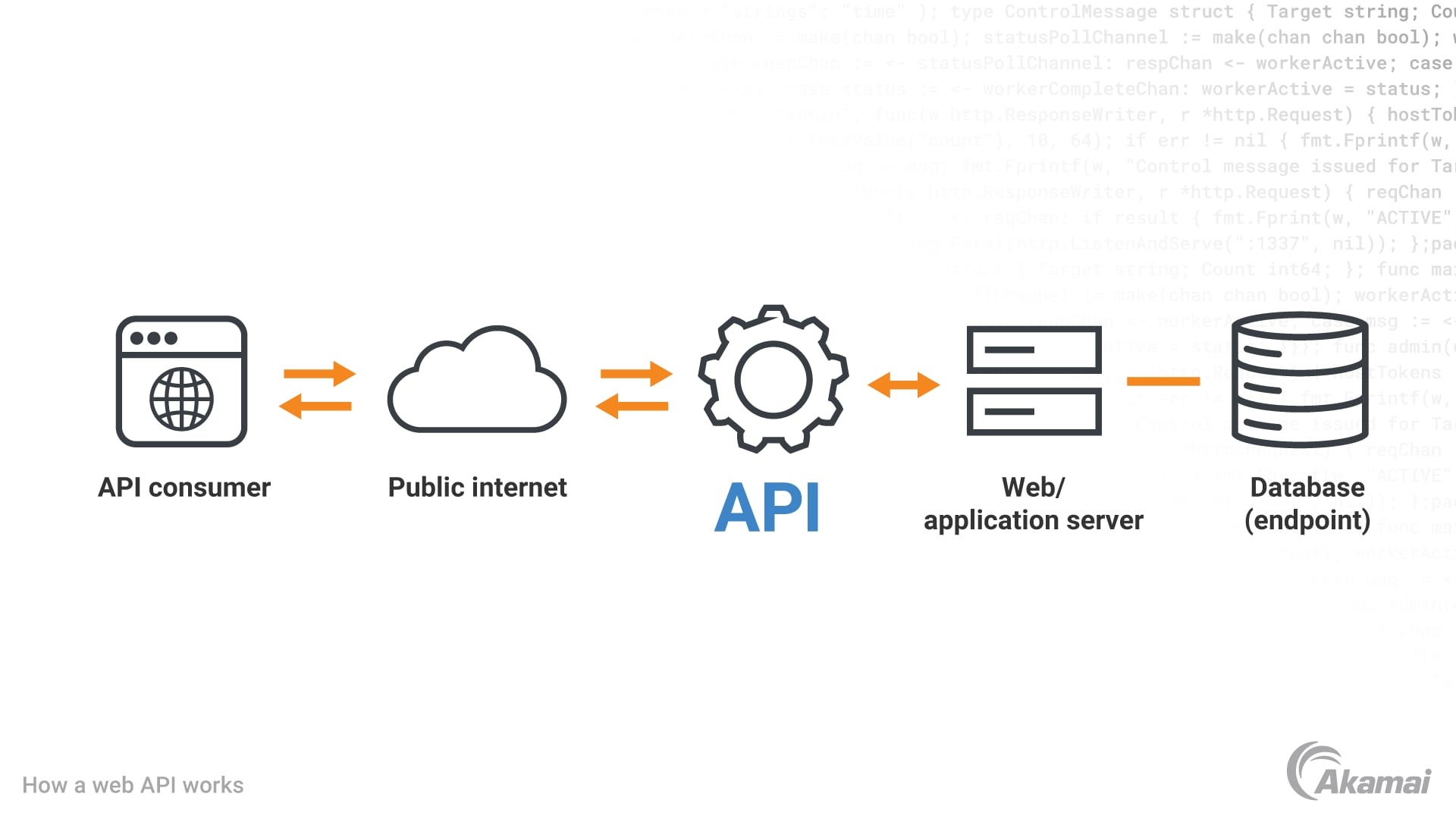
A detailed assessment of API security should consider several key factors:
Authentication and authorization: APIs should implement robust mechanisms, such as OAuth or JWT, to ensure that only legitimate and authorized users or services can access the API.
Encryption: All data transmitted over APIs should be encrypted using secure protocols like HTTPS to guard against eavesdropping and machine-in-the-middle attacks.
Error handling: Proper error handling is crucial to avoid potential information leakage through error messages.
Rate limiting: Implementing rate limiting helps mitigate API abuse by restricting the number of requests a user or service can make within a given time frame.
Input validation: All inputs should be validated and sanitized to prevent common injection attacks.
To have complete API security, regular vulnerability assessments and penetration testing are needed. These tests allow businesses to identify and address potential security issues proactively, ensuring that the API stays secure, efficient, and reliable.