To download the Infection Monkey, please submit the form at right. We will provide you with the files and an installation guide.

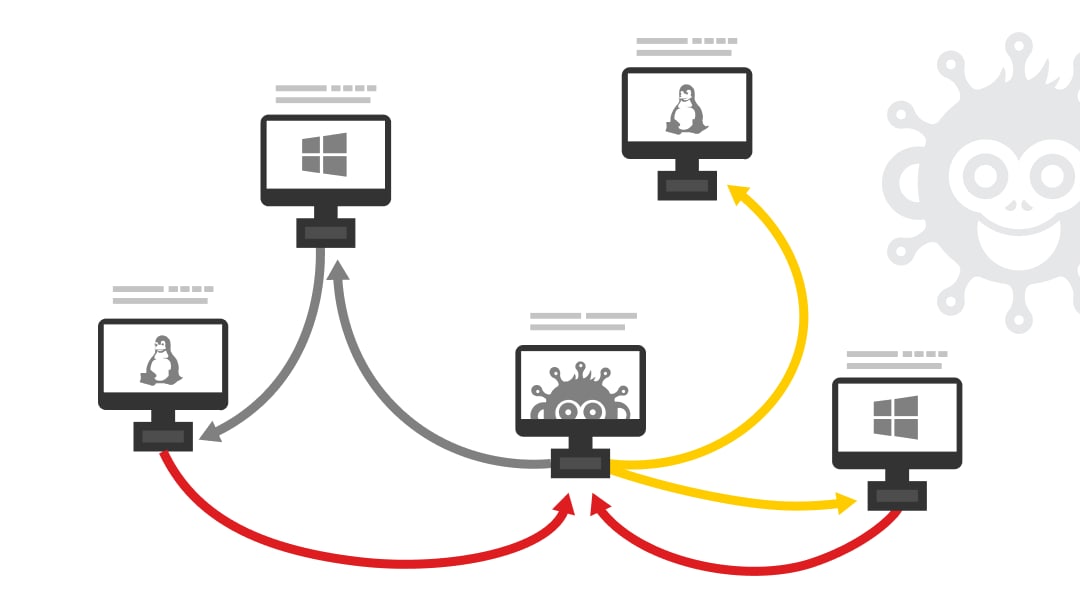
Simulate a ransomware attack on your network to identify propagation paths and test your organization’s response.
• Encrypt user-specified files
• Leave a ransom note
• Highly configurable behaviors
• Safe for production environments
The Infection Monkey encrypts user-specified files using a fully reversible algorithm, leaving a ransom note behind.





To download the Infection Monkey, please submit the form at right. We will provide you with the files and an installation guide.