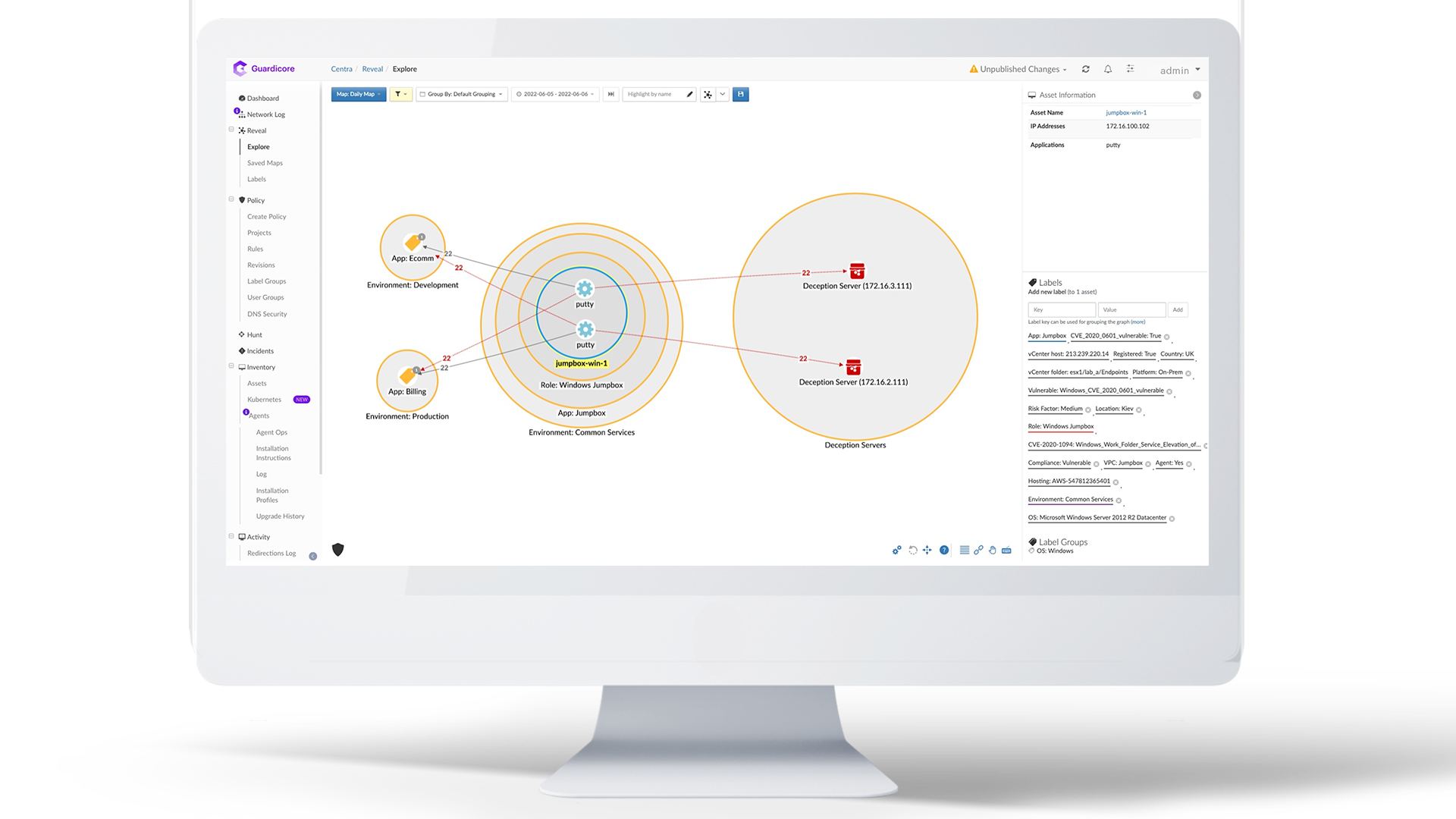
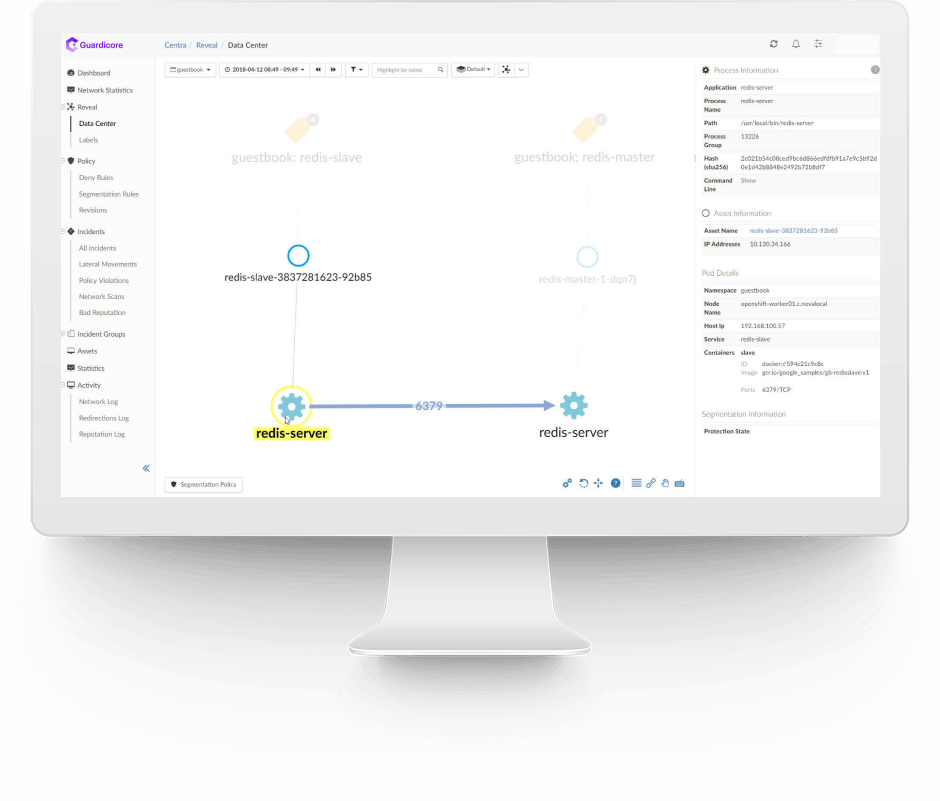
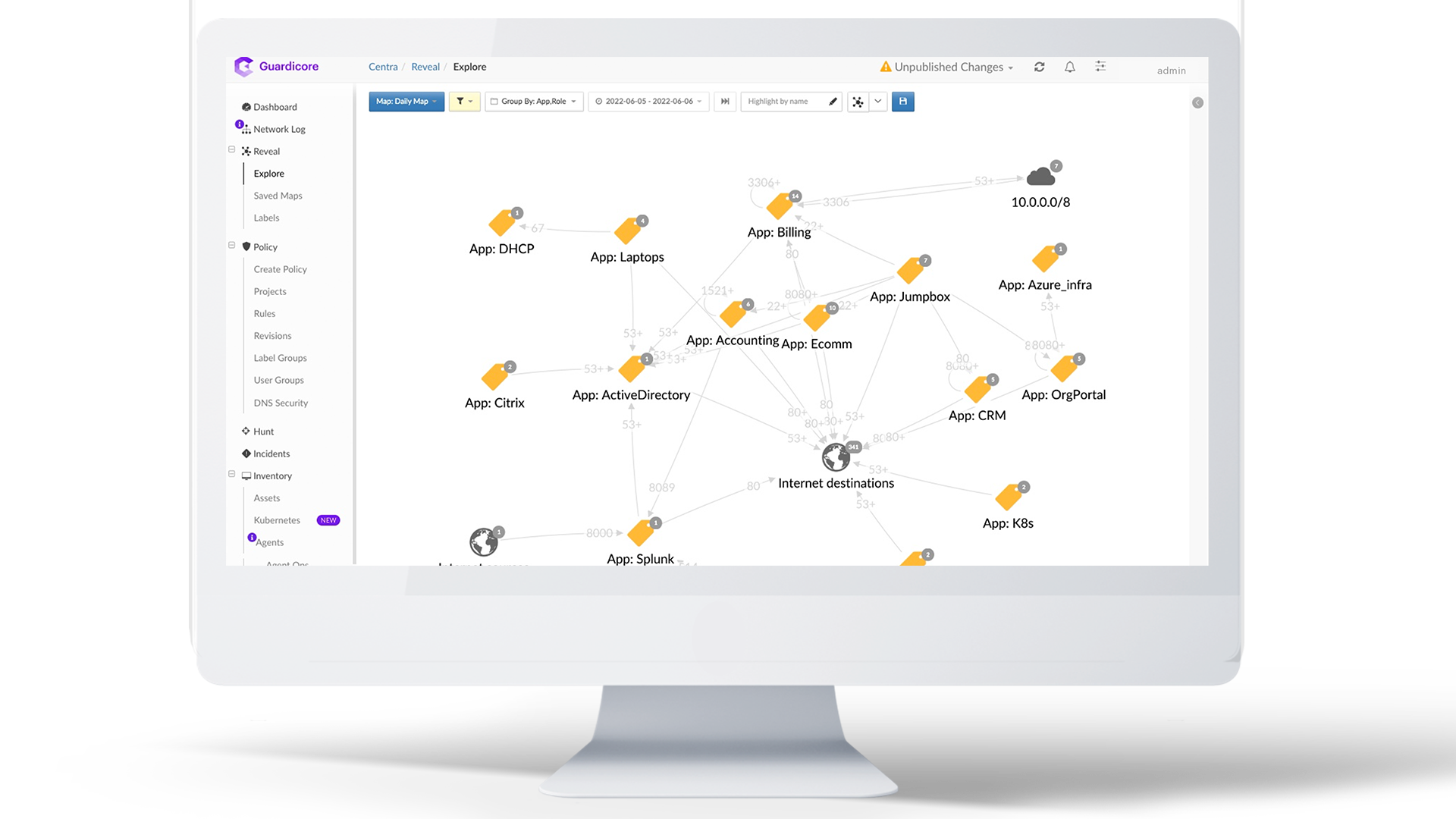
Akamai is an Advanced Technology Partner for AWS microsegmentation, with security competency. As a powerful third-party tool, Akamai Guardicore Segmentation uses deep visibility to map your entire IT infrastructure and its communication and dependencies in an intuitive way. This map supports a multi- and hybrid cloud infrastructure, helps teams to ensure that their security posture is maintained, and confirms that they understand how their applications and environments interact and depend on each other. It also provides the basis for building a smart, flexible, and tight microsegmentation security policy. Altogether, Akamai makes the shared responsibility model of the AWS cloud simple to manage and maintain.