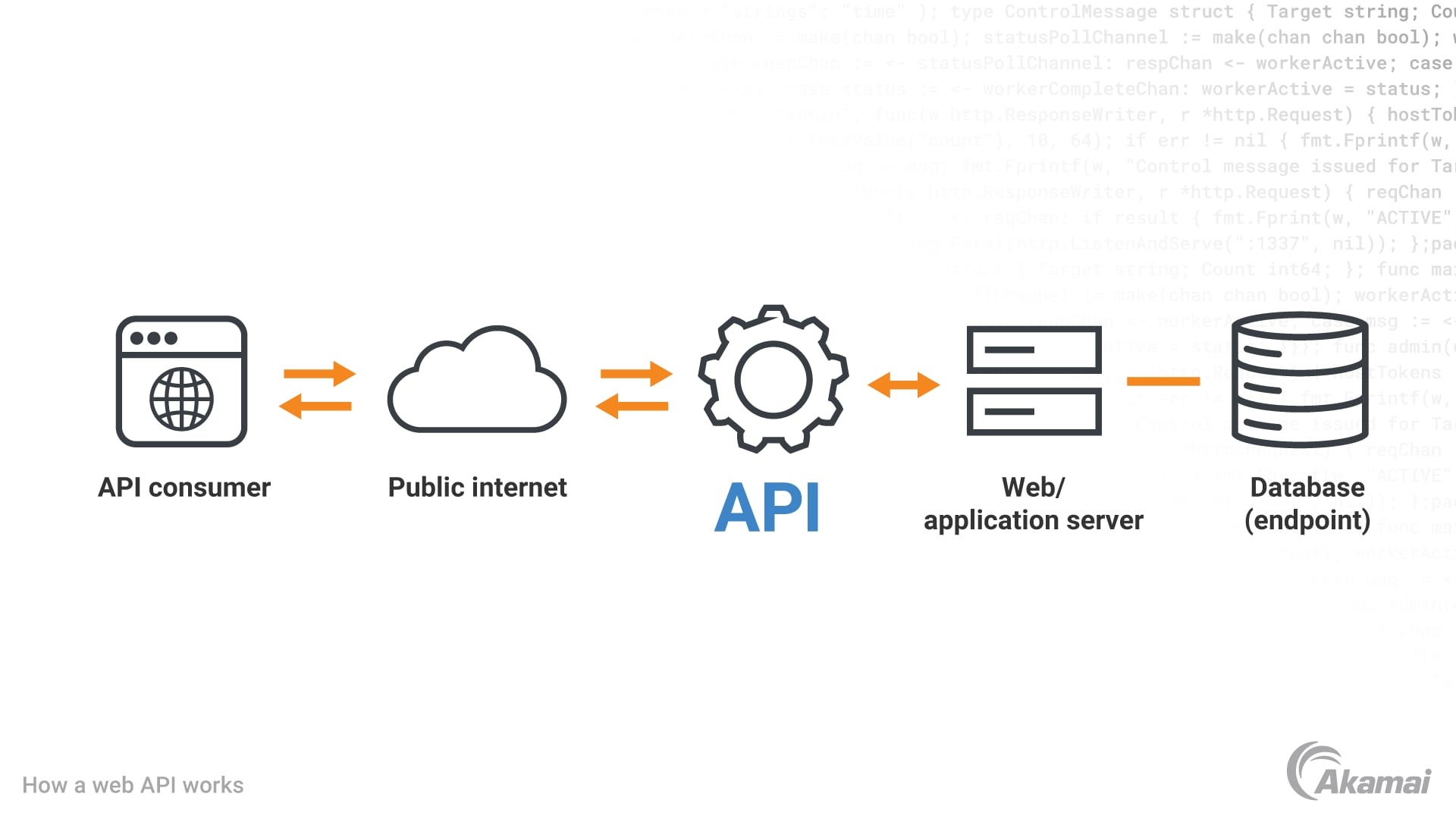
API security is a critical concern for businesses and organizations that rely on APIs to provide access to their services and data. APIs can be vulnerable to a wide range of security risks, which can lead to data breaches, unauthorized access, and other forms of abuse.
Why hackers love APIs: Hackers love APIs because they often hold the keys to a lot of valuable information. If not properly secured, APIs can potentially expose sensitive data.
Exploiting security oversights: Hackers look for APIs built and deployed without sufficient security measures, which offer an easy point of entry. Legacy APIs, if not regularly updated, also become targets for threat actors because there are often multiple entry points overlooked or forgotten about.
Exploiting complexity: APIs facilitate a large amount of interaction types, especially in microservices and distributed architectures. The intricate interactions of APIs can challenge organizations’ ability to keep their API security standards ahead of threat actors. Hackers know this, and use complexity to exploit the API.
Exponential effects of API attacks: APIs are also attractive to hackers because of their potential use in larger data loss. By targeting API endpoints in a distributed denial-of-service (DDoS) attack, a hacker could significantly disrupt a system’s operations.
Types of API security threats: APIs face numerous security threats, ranging from deliberate attacks to inadvertent data leaks. Unauthorized users may exploit vulnerabilities in an API to gain access to sensitive data, disrupt services, or hijack the system for their use. Some common threats include injection attacks, machine-in-the-middle (MITM) attacks, and DDoS attacks aimed at overwhelming an API with traffic.
The need for API security measures: The increasing dependence on APIs underscores the necessity for API security. Protecting APIs can be a challenging task that goes beyond access restrictions. It involves rigorous authentication protocols, authorization controls, data encryption, and regular security audits. The goal is to create a security envelope around APIs that can resist attempts at intrusion or misuse.
Implementing best practices in API security: Implementing best practices in API security can significantly reduce the risks. Access restriction (or least privilege) ensures that a user is given the minimum levels of access necessary to perform their job functions.
Another security measure is the Zero Trust model, which operates on the assumption that no request should be trusted by default, regardless of where it originates.
API security as a business imperative: Organizations need to invest time, resources, and ongoing strategy to protect their APIs against the many security risks faced. Protection against data breaches, compliance with regulatory requirements, preservation of brand reputation, and the trust of customers and partners who interact with your APIs are results of an effective API security strategy.