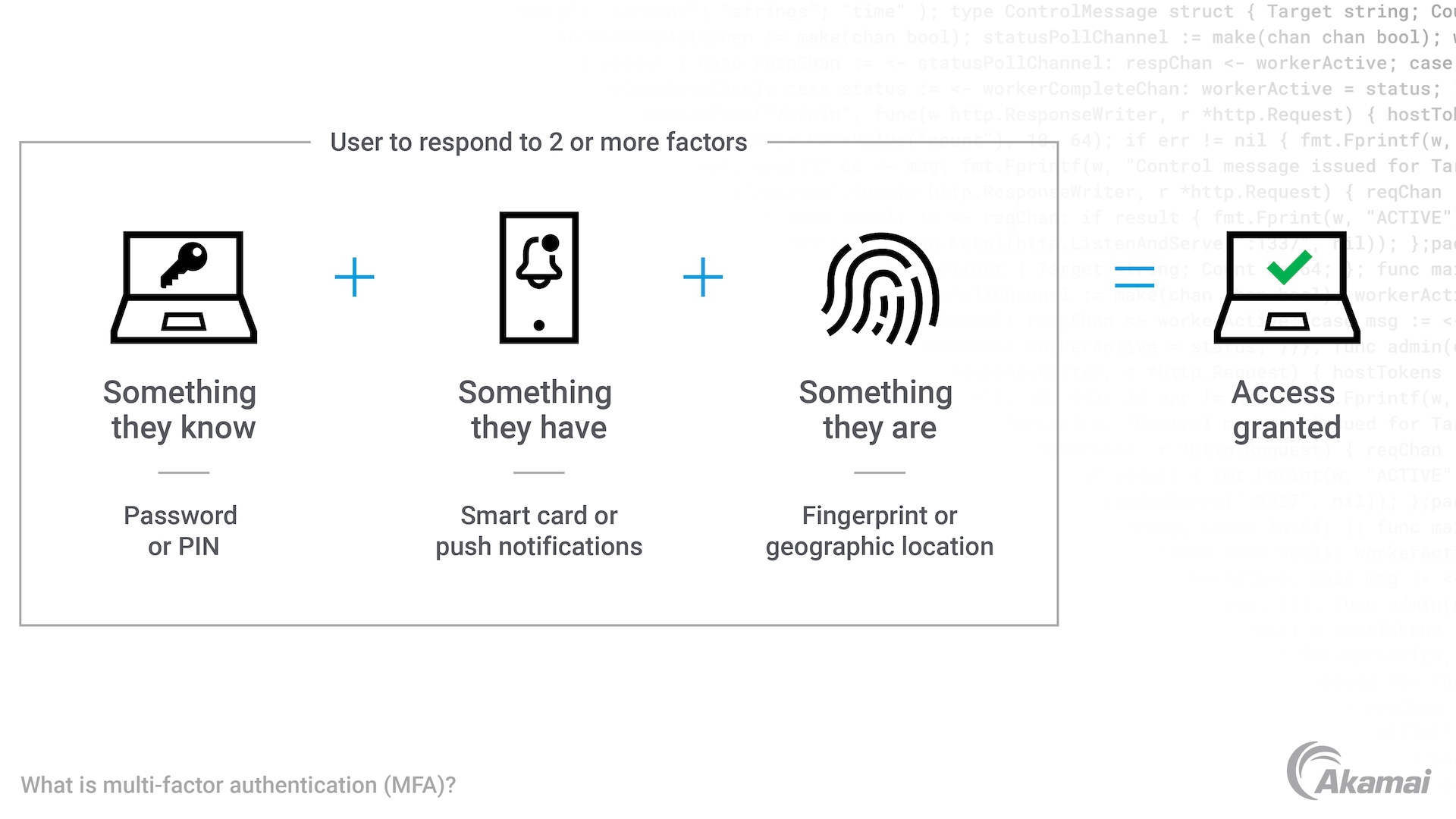
Multi-factor authentication (MFA), also called two-factor authentication, is a security technology that requires a user to present a combination of two or more credentials, or factors, to verify their identity for login. Factors must include something the user knows, such as a PIN, password, or answer to a security question; something the user is, which can be satisfied by a fingerprint or facial recognition scan; and something the user has, such as a key fob, smart card, one-time password, or push notification to a mobile phone.
MFA services deliver stronger security
From ransomware and advanced persistent threats to malware and spear-phishing attacks, devastating cyberattacks are plaguing companies of all sizes as they struggle to defend their business-critical data and systems. These efforts are complicated by a perpetual shortage in security talent as well as the new complexities of BYOD and remote work security.
Because many of these breaches begin with stolen credentials, savvy organizations are turning to multi-factor authentication, or MFA, services, to add an additional layer of security. MFA solutions use a two-factor authentication protocol, where users must authenticate with additional information such as a one-time password (OTP), push notification, fingerprint scan, or voice recognition to gain secure access to applications or services.
While MFA services are a significant improvement over login protocols that require only usernames and passcodes, traditional MFA is not foolproof. MFA services that use the FIDO2 standard are more impervious to being hacked, but they are more complex to use and manage as well. That’s why Akamai offers MFA services that deliver superior security while providing a frictionless user experience.
Risk levels for authentication models
Eighty percent of hacking-related data breaches involve stolen user credentials or poor password hygiene, making superior authentication technology essential to enterprise security. The standard approaches to authentication come with significantly different levels of risk, and it’s critical to understand the differences before investing in authentication solutions.
High risk: username and password authentication
When organizations rely solely on single-factor usernames and passwords to verify user identities, they are highly vulnerable to attack. Login details can easily be stolen, guessed, or harvested. Malicious actors can easily bypass this level of security through direct access if they have the employee credentials, or through credential stuffing if they know the usernames. To compound the problem, many employees use the same passwords for their personal accounts. If these personal credentials are compromised, attackers will use the stolen passwords to target corporate accounts.
Medium to high risk: standard MFA services
MFA functionality improves enterprise security by requiring a second level of authentication to verify a user. The second factor may be something a user knows like a PIN, something they have like a device or one-time password, or something they are. This last factor may rely on biometric data such as facial ID or a fingerprint. While MFA technology greatly reduces the risk of a breach, hackers may still successfully gain access to systems through phishing, social engineering, transparent proxies, SIM swapping, and other techniques.
Low risk: FIDO2-based MFA services
The most effective authentication security is provided by MFA services that are built on FIDO2, the strongest standards-based authentication method available. This technology uses cryptographic login credentials to authenticate users and supports the eventual evolution to fully passwordless authentication. By protecting login credentials from phishing or social engineering attacks, FIDO2-based solutions solve the security vulnerabilities of traditional MFA services.
The downside of FIDO2 MFA technology is that it requires physical FIDO2 security keys for every user, adding considerable cost and complexity to the authentication process. That’s why Akamai has engineered a next-generation MFA offering that reduces cost and complexity while also minimizing risk.
MFA services from Akamai
Akamai MFA is a workforce multi-factor authentication solution that provides strong secondary authentication to cloud, web-based, on-premises, SaaS, and IaaS applications. Akamai simplifies the FIDO2 authentication process by replacing physical hardware tokens with push notifications on a smartphone app. End-to-end cryptography and a sealed challenge/response flow provide superior security, making the authentication process unsusceptible to phishing and social engineering attacks.
With MFA services from Akamai, you can:
- Quickly deploy a superior MFA solution. Users can download the Akamai MFA app onto existing smartphones, eliminating the delays associated with distributing physical security keys or issuing compatible hardware.
- Provide users with a frictionless experience that leverages their own smartphone and uses familiar push notifications.
- Minimize the risk of breach by deploying a FIDO2-based solution that eliminates the impact of phishing and social engineering attacks.
- Reduce the total cost of ownership by avoiding the need to purchase, replace, and maintain additional hardware.
- Enable Zero Trust networking by deploying the strongest available authentication and authorization protocols.
- Future-proof investments in MFA services with a FIDO2-based, cloud MFA solution that’s designed to evolve to support future use cases.
MFA services from Akamai
Akamai MFA works with a primary identity provider (IdP) such as Microsoft Azure AD or Okta to deliver stronger authentication security. When a user provides the correct username and password at login, the IdP connects to Akamai MFA to request that the sector factor request is generated. Akamai MFA renders a page that allows users to select a second factor, and then sends a challenge — a phish-proof push, for example — to an app on the user’s smartphone. When the user acknowledges the request, Akamai MFA passes control back to the IdP, which then allows the user to access the requested application or service.
Additional features of Akamai MFA include:
- Configurable options that allow organizations to choose authentication factors for specific use cases, including phish-proof push, standard push, time-based one-time password (TOTP), and Short Message Service (SMS).
- Automated user provisioning workflows using SCIM (System for Cross-domain Identity Management) to keep administrators informed of authentication events.
- Self-service user enrollment with multiple low-friction methods to simplify enrollment and device registration and reduce the burden on administrators.
- Integration with IdP solutions such as Microsoft Azure, Okta, and Akamai IdP.
Frequently Asked Questions (FAQ)
By requiring an additional layer of security to successfully authenticate users requesting access to an application or service, MFA security solutions are an essential part of Zero Trust networking and remote work security. Companies that deploy the additional security of an MFA solution are far less likely to be the victim of a security breach than companies that do not.
An identity provider (IdP) is a company that specializes in providing authentication and authorization services to its customers. They provide services such as identity verification, user authentication, single sign-on, access control, and more. The purpose of an IdP is to ensure the security of user data and credentials, providing the necessary protection to ensure that users’ identities are kept safe and secure.
FIDO (Fast IDentity Online) is an open industry association that seeks to reduce the world’s overreliance on passwords through the development and promotion of open standards for strong authentication. The FIDO Alliance is working to provide a secure, interoperable standard for authentication and authorization that is designed to replace passwords and reduce the burden of fraud and identity theft. FIDO authentication is based on public key cryptography and enables users to authenticate to online services using a variety of credentials such as USB security keys, biometrics, or mobile phones.
Why customers choose Akamai
Akamai powers and protects life online. Leading companies worldwide choose Akamai to build, deliver, and secure their digital experiences — helping billions of people live, work, and play every day. Akamai Connected Cloud, a massively distributed edge and cloud platform, puts apps and experiences closer to users and keeps threats farther away.