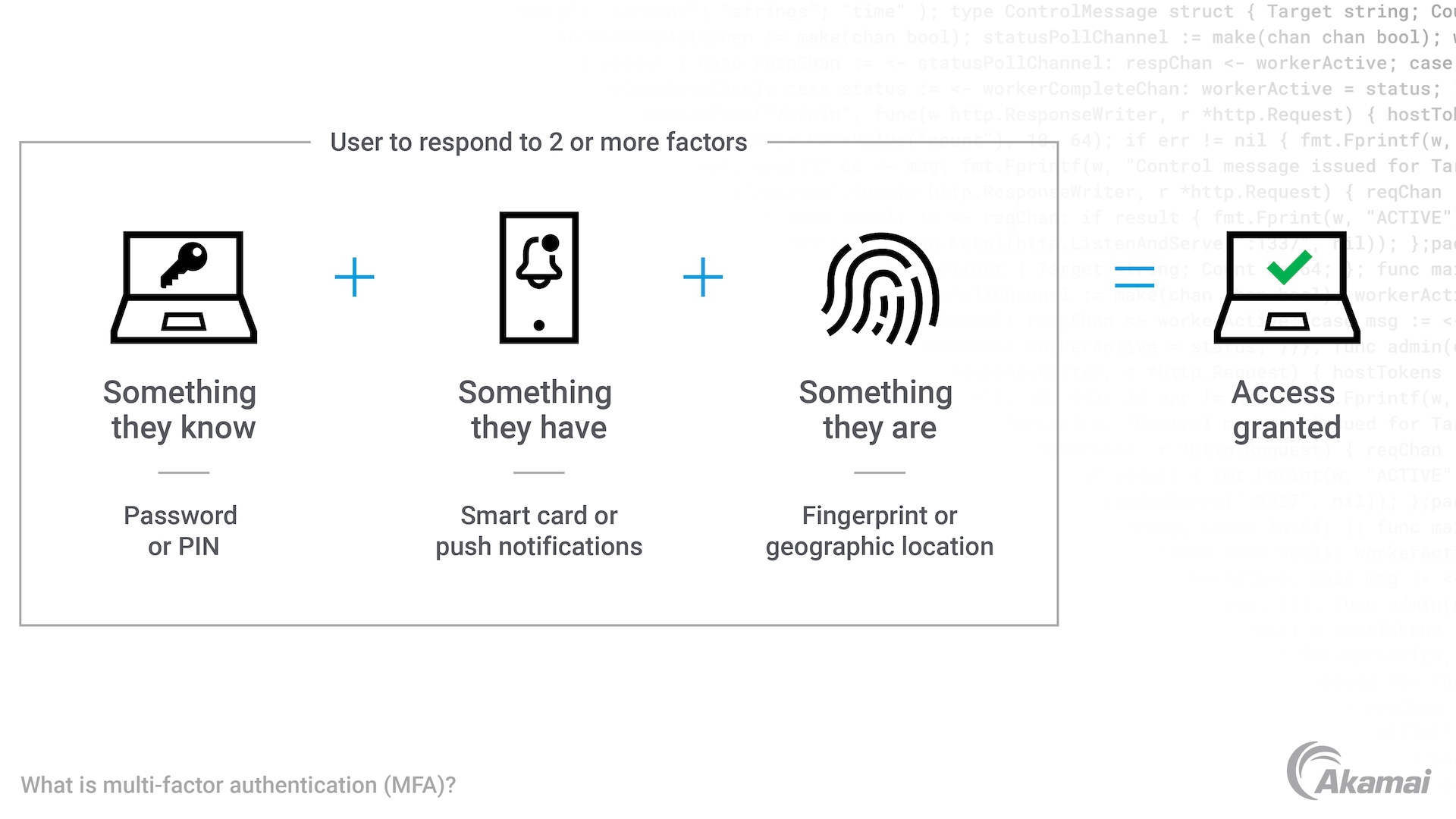
Multi-factor authentication (MFA) solutions, also known as two-factor authentication solutions, require a user to satisfy two or more conditions before receiving permission to access applications or services online. For a successful authentication process, users must present something they know such as a passcode, something they have such as a push notification, and/or something they are, such as a fingerprint or facial recognition scan.
MFA solutions enable secure network access
Authenticating the identity of users is a critical step in securing an organization’s network, data, and systems from attack. Approximately 80% of data breaches today involve stolen or compromised credentials, and increasingly sophisticated attacks can cost organizations millions of dollars in damages, not to mention loss of opportunity, loss of reputation, and loss of business continuity.
Multi-factor authentication (MFA) solutions offer a significant improvement over traditional password-only authentication methods. By requiring two types of proof that a user is legitimate, MFA solutions can help to significantly reduce the likelihood of a breach. Yet MFA isn’t perfect. Traditional MFA solutions can be easily bypassed by clever hackers. MFA services built on the FIDO2 standard offer greater protection, but they are much harder to manage for both users and administrators.
Akamai MFA solves the challenges of multi-factor authentication solutions with technology that combines FIDO2 security standards with a frictionless user experience and an easy-to-manage platform that minimizes the burden on IT administrators.
The benefits of MFA solutions
MFA technology protects networks, data, and users by requiring more than one source of validation when granting a user access to applications and services. With MFA solutions, users must successfully present at least two types of authentication credentials from different categories:
- Something they know. This type of authentication is based on knowledge and could be a password or a PIN.
- Something they are. This category of authentication is contextual or biometric. MFA solutions may authenticate a user via a fingerprint scan, facial recognition, a voice or speech pattern, or through contexts such as signing in from a certain location or at a certain time.
- Something they have. This token-based form of authentication could be a one-time password (OTP), a push notification to a mobile app, a smart card, or key fob.
The benefits of MFA services are significant. Organizations that use MFA are significantly less likely to be compromised than those that do not. MFA streamlines secure access to all environments, including cloud, SaaS, on-premises, web-based, and IaaS applications. And MFA technology is an essential component for migrating enterprise cybersecurity to frameworks such as Zero Trust and SSE.
However, while traditional MFA solutions offer significantly greater protection against breaches, they can nevertheless be bypassed by attackers. Cybercriminals have developed relatively simple yet highly effective social engineering and phishing techniques that take advantage of critical security weaknesses in standard MFA solutions. To defend against these attacks, organizations can implement MFA solutions based on the FIDO2 standard, which detects illegitimate MFA challenges and uses end-to-end cryptography to ensure that only a legitimate user can trigger a second-factor challenge.
MFA solutions from Akamai
The Akamai MFA service enables organizations to take advantage of the secure functionalities of FIDO2, while eliminating the challenges of using this highly secure standard. Most MFA solutions built on the FIDO2 standard require the use of physical FIDO2 security keys, which are both costly and cumbersome. In the past, to get the best FIDO2-based security, IT teams had to purchase physical hardware tokens for every employee, and manage the distribution and operation of all keys. Users were faced with a less-than-ideal MFA experience that required them to use and keep track of another piece of hardware.
Akamai MFA provides highly secure, phish-proof MFA technology without the need for physical security keys. Akamai’s solution digitizes the security of FIDO2 using a smartphone app and a web browser, and combines it with the easy-to-use, familiar experience of a push notification that can be used across any platform as a roaming authenticator.
With Akamai MFA, businesses can:
- Reduce risk by deploying an MFA solution that can’t be subverted by phishing and social engineering attacks
- Deploy MFA solutions rapidly on existing smartphones, avoiding the delays typically caused when needing to distribute physical security keys or issuing compatible hardware
- Provide users with a frictionless authentication experience that leverages their smartphones and uses familiar push notifications
- Reduce total cost of ownership (TCO) by using an existing smartphone and web browser to digitize FIDO2 security, avoiding the need to purchase, replace, and maintain additional hardware
- Support Zero Trust security by implementing the strongest possible authentication and authorization protocols
- Future-proof investments in MFA security with a cloud MFA solution built to evolve to support future use cases
How Akamai MFA works
Akamai MFA offers unrivaled security via frictionless push notification. With Akamai’s configurable authentication factors, IT teams can select the forms of authentication needed for specific use cases, including phish-proof push, standard push, TOTP (time-based one-time password), and SMS (Short Message Service). Akamai also integrates easily with market-leading IdP (identity provider) solutions, and provides a rich set of reporting features to keep the administrative team informed of authentication events. To reduce the burden on admins, Akamai offers various low-friction self-service methods that enable users to easily enroll and register their devices.
The Akamai MFA solution authenticates users via an easy, six-step process.
- The user provides a username and password to a primary authenticator such as Microsoft Azure AD.
- After validating the credentials, the primary authenticator connects to Akamai MFA to generate a second factor.
- Akamai renders a page where the user can select an authentication factor.
- Akamai MFA sends a challenge such as a phish-proof push to the user’s smartphone.
- Once the user responds, Akamai passes control back to the primary authenticator.
- The primary authenticator allows the user to access the requested service or application.
Frequently Asked Questions (FAQ)
By making it harder for unauthorized users to gain access to enterprise networks, MFA technology dramatically improves enterprise security. MFA solutions are also an integral part of security frameworks such as Zero Trust and SASE.
TOTP stands for time-based one-time password. It is an authentication mechanism that generates a unique six-digit code every 30 seconds. The code is based on a shared secret key between the user and the authentication system. It is typically used as a two-factor authentication method, where the user is required to enter the code in addition to their username and password.
SMS stands for Short Message Service, and is a type of text message that is sent from one mobile device to another. SMS messages are limited in length, typically up to 160 characters.
FIDO2 is an open authentication standard developed by the FIDO Alliance that enables users to securely authenticate to websites and applications with biometrics or a security key instead of a password. FIDO2 provides strong two-factor authentication and is designed to be more secure and easier to use than traditional password-based authentication methods.
Why customers choose Akamai
Akamai powers and protects life online. Leading companies worldwide choose Akamai to build, deliver, and secure their digital experiences — helping billions of people live, work, and play every day. Akamai Connected Cloud, a massively distributed edge and cloud platform, puts apps and experiences closer to users and keeps threats farther away.