A datagram is a unit of data sent over a packet-switched network. An IP packet is a type of datagram, as both contain data that has information needed to be routed from its source to a destination. However, some datagrams are derived via UDP (User Datagram Protocol).
What are packets and how are they delivered?
We’re now going to look at the Internet Protocol, IP. We’ll first look at IP packets. Then we’ll look at how packets are addressed, and then finally we’ll look at naming, which is the mechanism by which names are converted into addresses. I am assuming that you have already viewed the presentations on the Web Protocol.
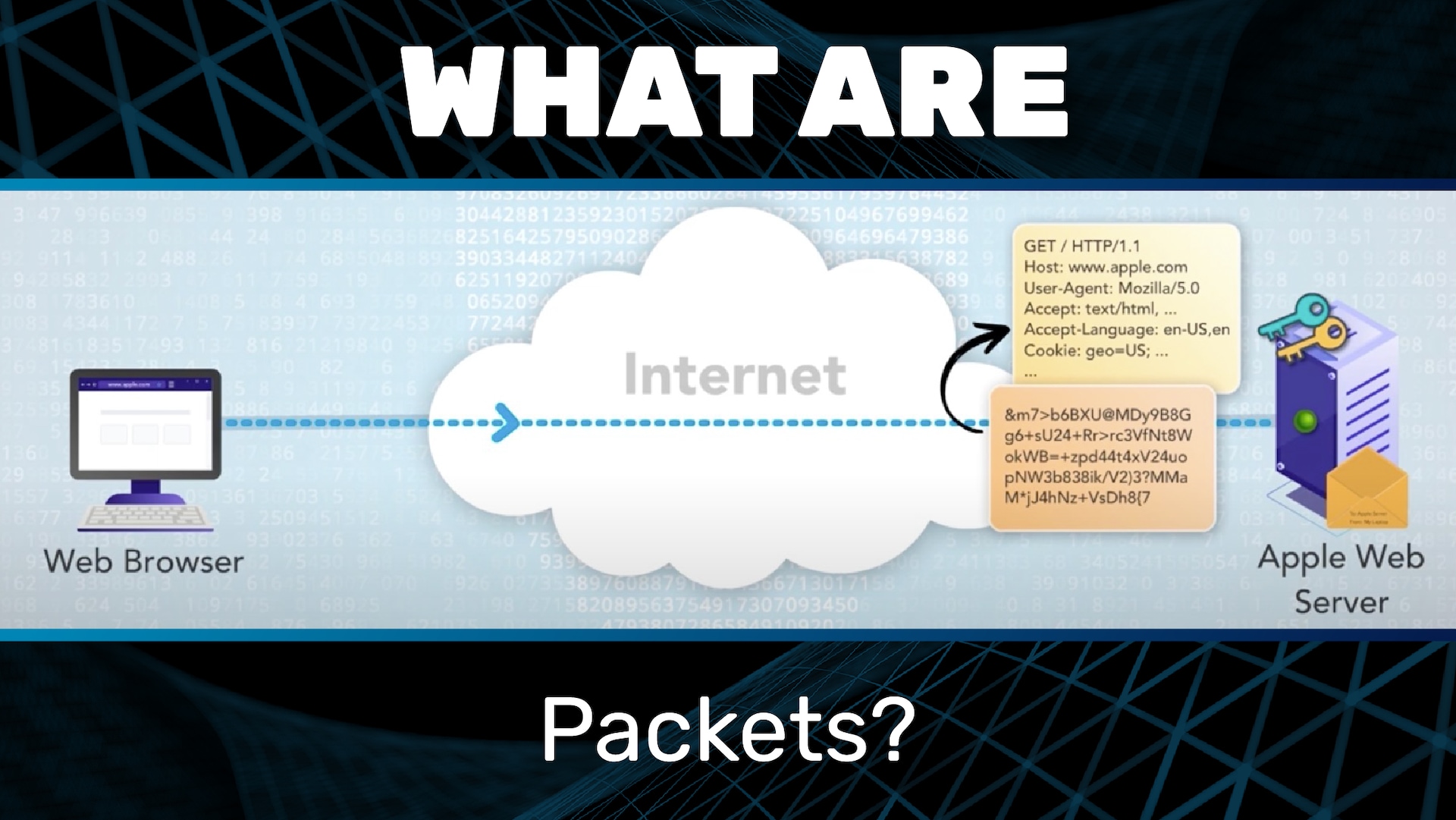
Recall that when we looked earlier at the Web Protocol, HTTP and HTTPS, and we saw that the Web Protocol involves request and response messages. In order for those messages to traverse the Internet, they have to be put into envelopes and those envelopes have to be addressed. This process is analogous to the postal mail that we’re all familiar with. If I want to send a letter to my sister, I can’t just write “To Joanna” at the top of the letter and hand it to the post office. Instead I have to put the letter into an envelope, and I have to address that envelope in the proper way. When it comes to the Internet, these envelopes are called packets. Soon we will look at how packets are addressed. Note also that packets have a fixed maximum size, so long messages have to be broken into multiple packets.
To see how this works, let’s revisit our example. Recall that we started by entering the address in the address bar or clicking on a link, and then the browser sends an encrypted request message to the web server. Let’s now look more closely at this step: sending the encrypted request message.
First, we have to create a new packet and address it. In this case, it is going to the Apple web server, and it is coming from my laptop. Of course, real Internet addresses don’t look quite like this, but we’ll get to that. Now, we can place the encrypted request message into the packet. Then we can send the packet to its destination: the Apple web server.
Upon receiving the packet, the Apple web server can then remove the message from the packet and then continue on with decrypting it and reading it.
The exact same process is followed for the encrypted response. In this example, the encrypted response is too big to fit into one packet, so it is broken into two.
A key point is that IP is what’s called a network layer protocol. It’s job is to move data in packets through the Internet from source to destination.
- IP specifies how the packets are addressed.
- IP specifies the maximum packet size.
- But IP does not specify or restrict what goes inside the packet. This is a key point.
Things you find inside an IP packet include:
Web request and response messages
- Voice over IP (VoIP)
- Real-Time Streaming
- Email messages
- Domain Name System (DNS) request and response messages
All of these are examples of application layer protocols.
Layering is a critical concept in communication protocols. Application endpoints speak and understand their application protocols. For example:
- Web browsers and servers speak and understand HTTP and HTTPS, and
- Email readers and servers speak and understand the email transport protocol which is called Simple Mail Transport Protocol, SMTP.
But network elements such as routers don’t have to speak or understand any of these protocols! They only need to speak and understand the Internet Protocol. Applications look inside the packets whereas network elements look at the outside. Compare this again to postal mail. I could write a letter to my sister using a secret language that only we know, but so long as I put that letter into an envelope that is addressed in the proper way, then the postal service can deliver that letter no problem. My sister and I look inside the envelope, but the postal service only looks at the outside.
This separation of layers has fueled tremendous innovation. At this point there are thousands of application layer protocols, and there are many link-layer protocols. Think of the link layer as the physical connection, such as Ethernet, WiFi, and cellular. But there is only one network layer protocol, and that is IP.
New applications can easily be layered on top of IP. Anyone can invent a new application protocol, and so long as the messages can be put into IP packets, it will work on the Internet. No changes to any network elements, such as routers, is needed. The WWW is a great example. When IP and the Internet were first created, the WWW didn’t even exist. Then, when Tim Berners-Lee created the WWW, he just had to put his newly invented request and response messages into IP packets. No changes to IP or the Internet were needed. The whole thing just worked.
Likewise, new link technologies can be layered below. Anyone can invent a new link technology, and so long as it can carry IP packets, it can be part of the Internet and carry any applications. Examples are WiFi and IPoAC.
You haven’t heard of IPoAC? Well, it stands for IP Over Avian Carrier. This was a real proposal, and despite the notable dating of this proposal, it actually makes an important point. If you can get pigeons to carry IP packets, then you could run WWW applications with pigeons. Slow, for sure, but it would work.
The internet used to be known as the “information superhighway.” This name described how computers could communicate with each other at super-fast speed across the distributed computer network. This communication was, and still is, based on specially formatted messages used for various tasks. The messages are “packets of data,” each containing the information required to perform a task, for example, display a web page.
The internet is a “packet switching network.” This term is used to describe how networking equipment processes data packets. The packets used to communicate across network connections are typically split into smaller parts, as there is a limit on the amount of data that can be transferred. Each packet is transmitted using IP or Internet Protocol — the only network-layer protocol. The job of the Internet Protocol is to move data in packets through the internet from source to destination. The packets that use the Internet Protocol are known as IP packets. To give you an idea of an IP packet’s size, a packet’s minimum size is 21 bytes, and the maximum size is 65,535 bytes. IP packets can take different paths to the same destination to help optimize routing.
What does IP specify?
The Internet Protocol (IP) is a network layer used to specify the following concerning IP packets:
- How the packets are addressed
- The maximum size of a packet
However, it is important to note that IP does not specify or restrict what goes inside the packet.
What is inside an IP packet?
IP packets can be compared to a physical letter. For example, if you want to send a letter to a friend, you place the letter in an envelope, then address the envelope so the letter can be routed to the correct person. Included within an IP packet as it is routed to the website are the following elements:
- Web request and response messages
- Voice over Internet Protocol (VoIP)
- Real-time streaming
- Email messages
- Domain Name System (DNS) request and response messages
All of the above are application-layer protocols, whereas the IP is a network layer.
IP packet communication
In our related glossary page on HTTPS (the secure version of the web protocol HTTP), we described how the request-response flow of the HTTPS protocol allowed information to be transmitted between a client (browser) and a web server. The IP packet enters during steps 2 and 3 of the HTTPS flow.
Follow the full request-response flow of HTTPS
Step 2 of HTTPS flow
Starting at step 2 of the HTTPS request-response flow, the following process occurs:
The browser sends a request to the web server. This request is first encrypted, and an IP packet is created; the encrypted message is then placed into the IP packet.
This packet is then sent to its destination (web server).
Step 3 of HTTPS flow
The IP packet from the client reaches the web server; the message it contains is decrypted and read. A response message is generated and encrypted before being placed into an IP packet and returned to the client. If the encrypted response is too big to fit into one packet, it is broken into smaller packets.
What is in an IP packet?
An IP packet comprises a header and a payload.
- The payload: This is the actual data that the packet or packets contain, e.g., text, image, etc. This is the equivalent of a physical letter you’d send to a friend.
- The header: This is equivalent to the envelope that contains the letter. The packet header or IP header is at the beginning of the packet. It contains the source IP address of the person sending the packet, its destination IP address, and other identifiers such as the browser, encryption information, packet length, etc.
- The trailer: IP packets end with a “trailer” that alerts the device that the packet has been completed. A CRC (cyclic redundancy check) ensures the device receives all the split packets.
The network layer protocol and application-layer protocols
Layering is an essential concept in communication protocols. Application endpoints speak and understand application protocols. For example, web browsers and servers communicate using HTTP and HTTPS, and email readers and servers communicate using the email transfer protocol (Simple Mail Transfer Protocol, SMTP).
However, there is only one network protocol — the Internet Protocol (IP). The thousands of application-layer protocols and many link-layer protocols — such as Ethernet, Wi-Fi, and cellular — communicate over this single network protocol. This separation of layers, with a standardized IP backbone, has fueled innovation. Having a single network-layer facilitates the development of applications that can be easily layered on top of IP; if the application supports messages that can be placed in IP packets, it will work on the internet — the whole system working symbiotically. No changes to any network elements, such as routers, are needed.
The World Wide Web (WWW) is an example of this innovation. When IP and the internet were first created, the WWW didn’t exist. Tim Berners-Lee used this layer separation to build the WWW, as the request and response messages could be placed in IP packets. No IP or internet changes were needed: The whole thing just worked.
Akamai, packets, and cloud computing
Akamai’s authority in cybersecurity was built upon a deep understanding of how protocols such as IP, HTTP, and HTTPS work. As well as security, Akamai optimizes cloud computing with our suite of cloud computing solutions; provides security, scalability, and visibility; and is agnostic to the cloud service provider. Our cloud computing product suite includes the Download Delivery product line that optimizes large HTTP file downloads flawlessly, every time, at a global scale.
Akamai’s internet attack protection
Cloud-based cyberattacks are ubiquitous. Akamai is dedicated to eradicating internet-borne web exploits. IP packet loss can be caused by distributed denial-of-service (DDoS) attacks against a web server. Our dedicated infrastructure provides DDoS prevention to stop attacks in the cloud before they reach applications, data centers, and internet-facing infrastructure — public or private. Akamai’s unique architecture segments DNS resources across dedicated, non-overlapping clouds. More than 225 frontline SOCC responders back Akamai; our fully managed solution filters out attack traffic and stops even the most significant attacks, freeing your defenders to focus on high-priority security programs. Akamai protects the modern enterprise from vulnerabilities introduced by the cloud and a distributed workforce.
Frequently Asked Questions (FAQ)
IP packets carry data between computers, across networks using the Internet Protocol (IP). An IP packet contains a payload and a header. The payload contains information such as text, image, video, etc. This includes the sender and destination addresses and the size of the packet. A packet may be split into more than one unit to transfer data, as IP packets are limited in size.
Yes, packet loss is the interruption of IP packets during their transmission. Packet loss can happen due to network congestion, DDoS attacks, software vulnerabilities, and other factors such as misconfiguration.
Why customers choose Akamai
Akamai powers and protects life online. Leading companies worldwide choose Akamai to build, deliver, and secure their digital experiences — helping billions of people live, work, and play every day. Akamai Connected Cloud, a massively distributed edge and cloud platform, puts apps and experiences closer to users and keeps threats farther away.