Bad bots perform malicious activities such as illegally scraping content, hoarding inventory, or buying and scalping tickets. Traffic bots artificially drive up traffic metrics on websites and social media accounts, while download bots repeatedly download software to boost download metrics.
A bot network, or botnet, is a group of thousands or millions of machines, computers, and Internet of Things (IoT) devices that are directed to perform types of attacks like large-scale, distributed denial-of-service (DDoS) campaigns or credential stuffing attacks.
How to defend against a bot network
It’s not hard to understand why bot networks, or botnets, are a favorite tool of cybercriminals. By controlling thousands or millions of hijacked computers or infected devices known as bots, a hacker or “bot herder” can use a bot network to carry out distributed denial-of-service (DDoS) attacks, mine for cryptocurrency, or send spam messages with malicious software (malware).
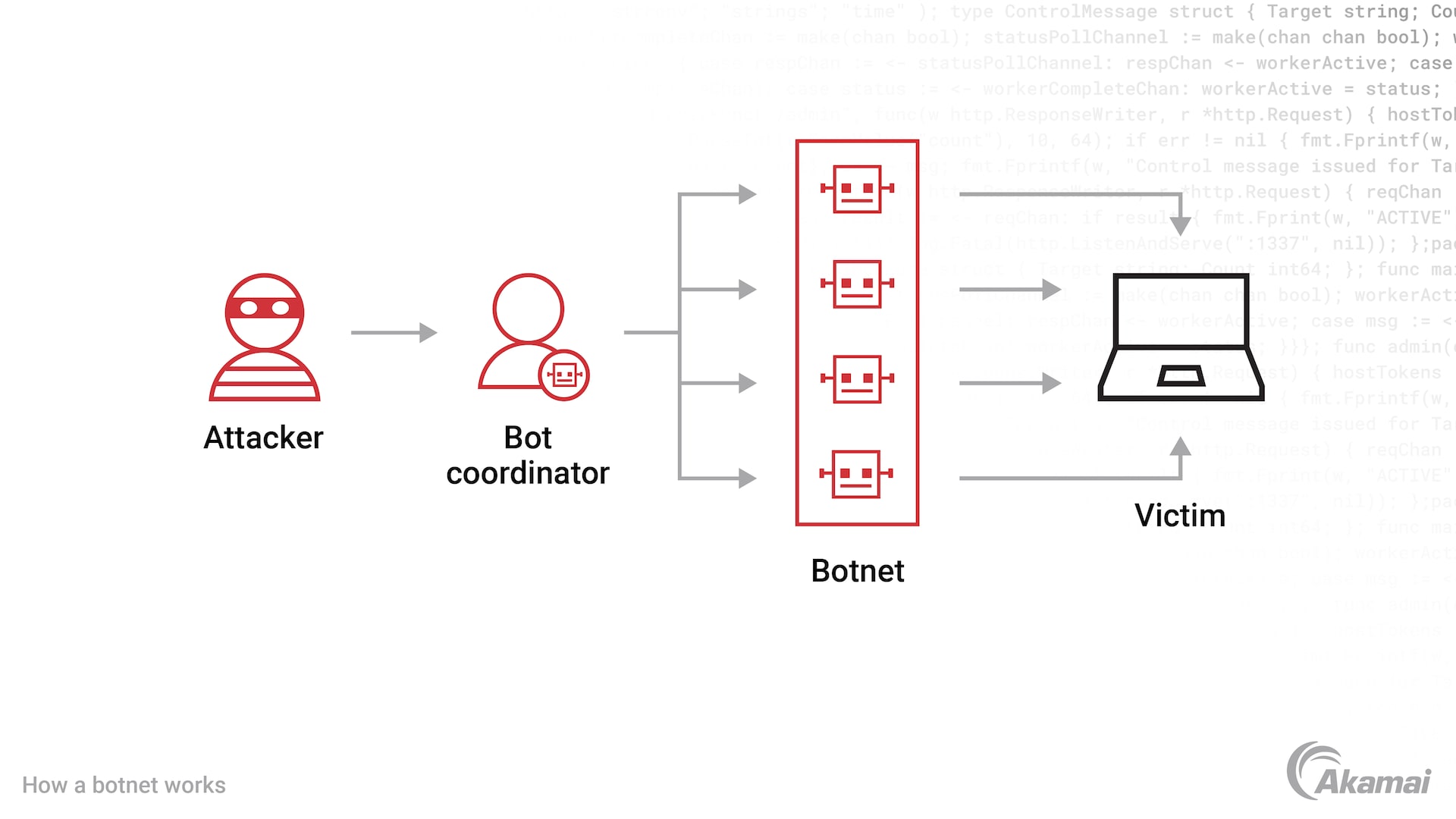
Credential stuffing is one of the most potent uses of a bot network. In a credential stuffing attack, cybercriminals use bot networks to automatically inject stolen username and password pairs into the login forms of websites, seeking a combination that will ultimately grant them unauthorized access to IT networks or user accounts. A single botnet can conduct hundreds of thousands of fraudulent login attempts per hour, and when successful, can cause companies and their customers to lose money, privacy, and trust.
Akamai Account Protector offers superior defenses against bot networks, botnet attacks, and credential stuffing. Deploying highly effective detection and bot mitigation technologies, Akamai’s solutions can spot suspicious human and bot behavior in real time to prevent credential stuffing, dangerous bots, and other account takeover attempts.
Bot networks and credential stuffing
Credential stuffing is a type of brute-force attack where hackers try multiple credentials in an attempt to gain access to an account. Where typical brute-force attacks use random username and password pairs, credential stuffing attacks use login information that has been stolen during a data breach. This technique is effective because users often employ the same username and password credentials on many websites.
To make their work easier, attackers use automated bot networks to inject the stolen credentials into a broad range of websites — from social media sites and web apps to online marketplaces. When a login is successful, the attacker can drain bank accounts, make purchases, access additional information such as credit card numbers, or sell the credentials to other cybercriminals for use in ransomware attacks and other scams.
Because the opportunities for financial gain are so significant, credential stuffing attacks attract some of the most experienced attackers, who use highly sophisticated bot networks. Many bot solutions can initially detect most bot activity, but operators will continually update or “mutate” their bot software as they work to circumvent defenses. Mutated bot networks can then avoid the original detection methods as they attempt to evade network security and gain access to user accounts through credential stuffing.
To block bot networks and credential stuffing attacks, organizations need advanced technology that can recognize sophisticated threats without compromising the user experience with cumbersome captcha controls. That’s where Akamai can help.
Akamai Account Protector
Akamai Account Protector is designed to detect imposters at the edge while allowing customers to get through without adding friction to their experiences. This comprehensive bot security solution prevents fraudulent human logins and mitigates the sophisticated bot networks that are often part of an account takeover attempt.
To distinguish between legitimate and fraudulent activity, Account Protector studies the behavior of legitimate account owners, creating user and population profiles that document typical behaviors around devices used, IP addresses, networks, locations, and frequency and time of logins.
For each authentication request, Account Protector assesses the risk that the request is illegitimate and takes appropriate action if the request is deemed to be fraudulent. Assessments are based on observation of any anomalies from the typical behavior profile, as well as the reputation of the source, based on past malicious activity observed across all Akamai customers. Machine learning constantly tunes the assessment process to the organization’s individual traffic and user behavior patterns.
To detect and mitigate harmful bot networks, this Akamai solution also uses AI and machine-learning models and techniques such as browser fingerprinting, behavior/telemetry analysis, automated browser detection, HTTP anomaly detection, high request rates, and others.
Akamai Bot Manager
Along with Akamai Account Protector, Akamai Bot Manager provides additional protection against bot network activity. Bot Manager uses multiple technologies to detect and mitigate bots where they make initial contact, rather than allowing them to reach a website first. These detection engines are automatically and constantly updated with insights from our threat intelligence teams, based on observation of worldwide web and bot traffic.
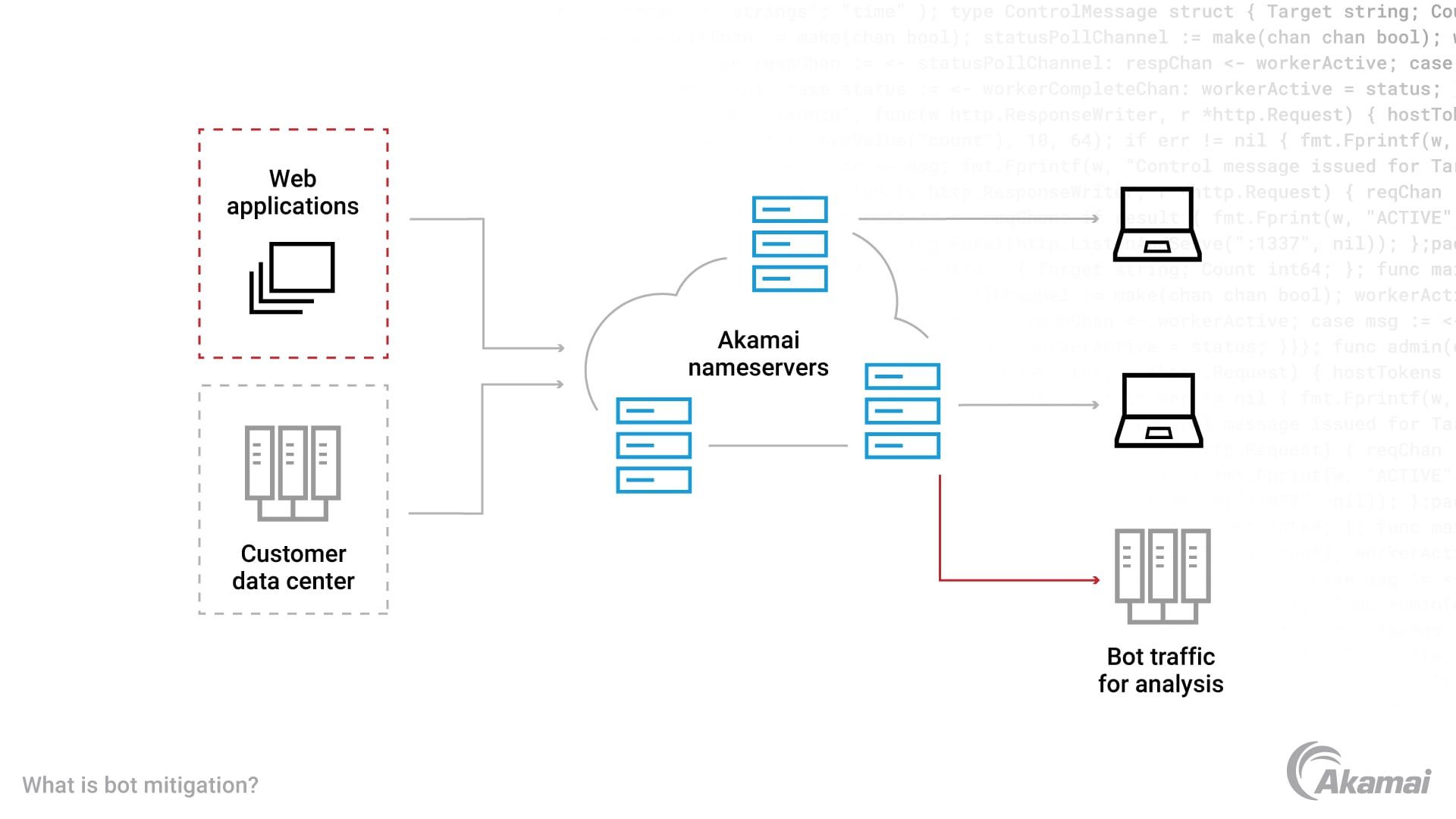 Image illustrating the process utilized by Akamai Bot Manager
Image illustrating the process utilized by Akamai Bot Manager
To recognize botnet activity, Bot Manager collects “clean traffic” data on traffic patterns, traffic types, and traffic volume as seen on Akamai Connected Cloud, the largest edge platform in the world. Across the network, Akamai sees an average of 11.5 billion bot requests per day and 250 million bot logins. This visibility enables our algorithms to quickly learn which bots are good and which are bad or part of a malicious bot network.
Bot Manager holistically combines all the detection triggers to identify sophisticated bots and provide a Bot Score that calculates the likelihood the request is coming from a bot vs. a human. Requests that are more likely to be from bots can be mitigated immediately or challenged with cutting-edge challenges that slow sophisticated bot attacks to a crawl and drive up the costs for attackers.
Frequently Asked Questions (FAQ)
A bot is an automated piece of software that is programmed to perform specific assignments. These are often highly repetitive tasks that a bot can execute much faster and more accurately than a human being.
Good bots perform helpful services — web crawling bots, for example, index the content on websites to make it easier for search engines to find them, while chatbots enable users to ask questions and navigate a company’s services on a website.
A bot network, or botnet, is a group of thousands or millions of infected machines, computers, and Internet of Things (IoT) devices that are directed to perform types of attacks like large-scale, distributed denial-of-service (DDoS) campaigns or credential stuffing attacks.
A botnet service is essentially a botnet for hire, where a cybercriminal will use a botnet to carry out various cybercrimes on behalf of another party for a fee.
Why customers choose Akamai
Akamai powers and protects life online. Leading companies worldwide choose Akamai to build, deliver, and secure their digital experiences — helping billions of people live, work, and play every day. Akamai Connected Cloud, a massively distributed edge and cloud platform, puts apps and experiences closer to users and keeps threats farther away.

