In a botnet service, a botnet operator uses a large group of malware-infected machines to perform actions or carry out attacks on behalf of a third party for a fee.
Defending against botnet services
Botnet attacks have been plaguing enterprises for years. From distributed denial-of-service attacks and phishing schemes to brute-force attacks and click fraud, botnets (short for “robot networks”) are deployed in many of the attack vectors used in cybercrime today.
Recently, there has also been a rise in botnet-as-a-service offerings. Cybercriminals who have invested in building a botnet with thousands or millions of hijacked computers are recouping their costs by performing services with their botnets for other attackers.
Defending against bots, botnets, and botnet services requires sophisticated anti-bot technology that can adapt as quickly as attackers’ methods evolve. The best bot detection technology must also distinguish between the helpful bots that are essential to productivity and the malicious bots that can compromise performance and lead to devastating attacks on network security.
As a leader in securing IT ecosystems, Akamai offers superior bot security solutions with unmatched detection and mitigation capabilities. With Akamai, you can block malicious botnet services and botnet traffic without compromising on performance or degrading the experiences of users.
How a botnet service works
A botnet is a network of computers, routers, servers, mobile devices, and Internet of Things (IoT) technologies that have been infected with malware and controlled by an individual called a bot herder. Botnets may range from a few hundred machines to millions of infected devices. From a central location, bot herders can direct the devices on part of a botnet to carry out a broad array of actions.
- Spamming Botnets’ work often involves spam operations, sending out messages that may include a “Trojan horse” or another type of malware.
- DDoS attacks By directing millions of hijacked devices to send requests to targeted network traffic or a central server, DDoS attacks render these IT resources unavailable to legitimate users.
- Adversarial attacks Some botnets are designed to exploit software vulnerabilities or to assist in ransomware campaigns.
- Credential stuffing Threat actors use botnets to attempt hundreds of thousands of logins per hour, using credentials stolen from another website. Since many users repurpose their usernames and passwords across many sites, attackers can eventually gain access to IT environments to steal data or money, disrupt business, damage systems, or launch larger attacks.
Building a botnet requires considerable time and resources. To offset their costs, some operators offer botnet services to other cybercriminals, carrying out a variety of attacks for a fee. Botnet services are typically sold and purchased on the dark web. For botmasters, offering botnet services helps to recoup the investment they’ve made in building a botnet. For customers, a botnet service allows them to carry out a range of nefarious activities with little effort and minimal investment.
Block botnets with Akamai Account Protector
In recent years, Akamai has grown into a cybersecurity powerhouse, with a portfolio that offers comprehensive defenses against a broad range of threats. Our platform offers multiple solutions that can help to defend against bots, botnets, and botnet services.
Akamai Account Protector, for example, is a comprehensive solution that’s designed to prevent fraudulent login attempts and to mitigate the sophisticated adversarial bots that often precede these types of attacks. Using a variety of techniques to understand the typical behavior of legitimate account owners, Account Protector can then assess the risk of each authentication request and determine the likelihood that it is or is not coming from a legitimate account owner.
For individual users and user populations, Account Protector develops profiles that cover the devices normally used as well as typical IP addresses, networks, locations, and frequency and time of logins. When the behavior of a user deviates from the profile or when there are anomalies in the authentication request, Account Protector can take appropriate action to challenge or block the request.
Additionally, Account Protector offers defenses against sophisticated bots, botnets, and botnet services that target organizations in automated, large-scale attacks. This Akamai technology uses AI and machine learning models to detect and mitigate harmful bots while ensuring that legitimate bots and endpoints have unhindered access.
Stop dangerous bots with Akamai Bot Manager
Akamai Bot Manager offers additional protection against bots and botnet services. Using multiple detection technologies, Bot Manager detects and mitigates bots when they make initial contact, rather than allowing them to access websites first. Detection engines are constantly updated with insights from Akamai’s threat intelligence teams, which analyze 300+ TB of new attack data daily to gain insight into the latest mutations of bots and botnet services.
Based on analysis of “clean traffic” across a large volume of traffic and a wide distribution of data types, Bot Manager combines a variety of detection algorithms to calculate a Bot Score. High scores indicate a request from a malicious bot and can be immediately mitigated. Low scores that indicate a request is from a human can be watched or monitored. For scores in the middle, Bot Manager issues cutting-edge challenges that slow bot attacks to a crawl while increasing expenses for attackers.
With Akamai Bot Manager, security teams can protect their organizations from harmful bot traffic while increasing the trust and bandwidth of customers and reducing the burden of remediating fallout from bot attacks.
Frequently Asked Questions (FAQ)
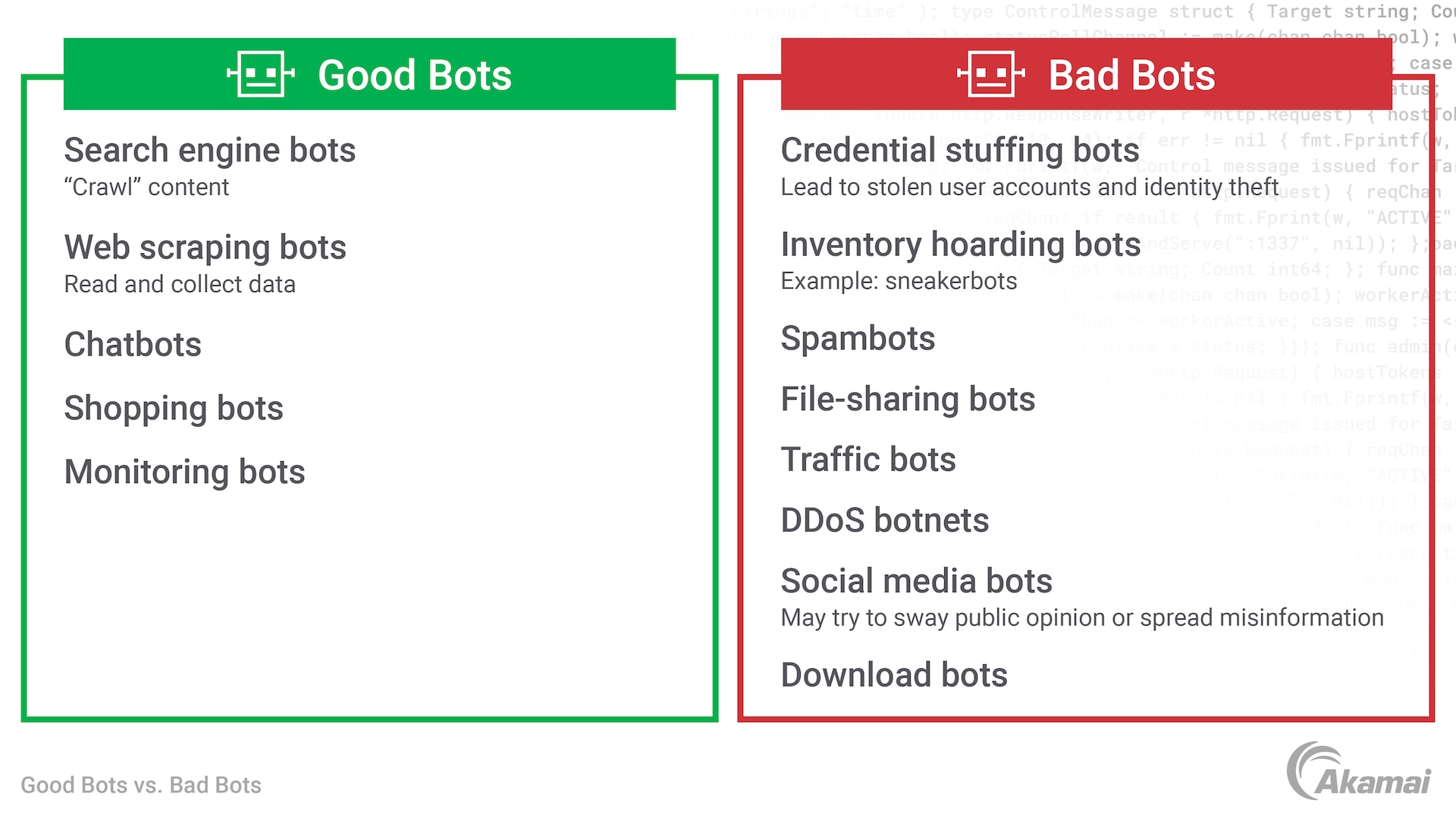
A bot is a software program that is designed to operate independently and perform specific tasks. Legitimate bots perform helpful activities with greater speed and precision than human beings can. However, many bots are designed for malicious or illicit purposes. Spambots, for example, harvest email addresses from websites for use by spammers, while traffic bots create artificial traffic on websites to drive up numbers of visits or to increase the number of likes on a social media account.
A botnet is a network of computers, Internet of Things (IoT) devices, and other machines that work together to launch large-scale, automated attacks. Often these botnets include devices that were infected with malware and whose owners don’t even realize they’re being employed this way. Cybercriminals use these infected machines to carry out a coordinated attack on a network or system using command and control software. Botnets and botnet malware are often involved in a variety of attack vectors, including the bad bots above — inventory hoarding, credential stuffing, spambots, and distributed denial of service, among others.
A botnet agent is a type of malicious software that is used to control or manage a network of computers, known as a “botnet.” This type of malware is typically used to create a zombie network of computers, which is then used to perform various malicious activities such as sending spam, launching distributed denial-of-service (DDoS) attacks, and stealing personal information.
A botnet is a network of computers that have been infected with malicious software and are under the control of a third party. The botnet is used to launch cyberattacks, send spam, and steal data. A botnet service is a set of services offered by a provider to manage a botnet. This typically includes the ability to control and configure the botnet, monitor its status and performance, and manage updates and upgrades.
Why customers choose Akamai
Akamai powers and protects life online. Leading companies worldwide choose Akamai to build, deliver, and secure their digital experiences — helping billions of people live, work, and play every day. Akamai Connected Cloud, a massively distributed edge and cloud platform, puts apps and experiences closer to users and keeps threats farther away.