A CLDAP reflection DDoS attack can result in network disruption, website downtime, and financial losses.
What is a CLDAP reflection DDoS attack?
In recent years, distributed denial-of-service (DDoS) attacks have become a significant threat to businesses and organizations worldwide. Attackers use various tactics, techniques, and procedures to overload servers with traffic, making websites or services unavailable to users. One of the techniques used by cybercriminals is amplification and reflection DDoS attack. A specific type of amplification attack called CLDAP reflection has been widely used since 2016, and this page helps to explain how it works and what you can do to protect yourself from it.
What is a CLDAP?
CLDAP stands for Connectionless Lightweight Directory Access Protocol. It is an RFC used by various devices and servers to access active directory services over local or public networks. LDAP, its Transmission Control Protocol (TCP) counterpart, is the connection-oriented version of the User Datagram Protocol (UDP), CLDAP. This attack vector is a type of DDoS attack that exploits the protocol’s weaknesses to overwhelm a target network with traffic.
What is a CLDAP?
CLDAP stands for Connectionless Lightweight Directory Access Protocol. It is an RFC used by various devices and servers to access active directory services over local or public networks. LDAP, its Transmission Control Protocol (TCP) counterpart, is the connection-oriented version of the User Datagram Protocol (UDP), CLDAP. This attack vector is a type of DDoS attack that exploits the protocol’s weaknesses to overwhelm a target network with traffic.
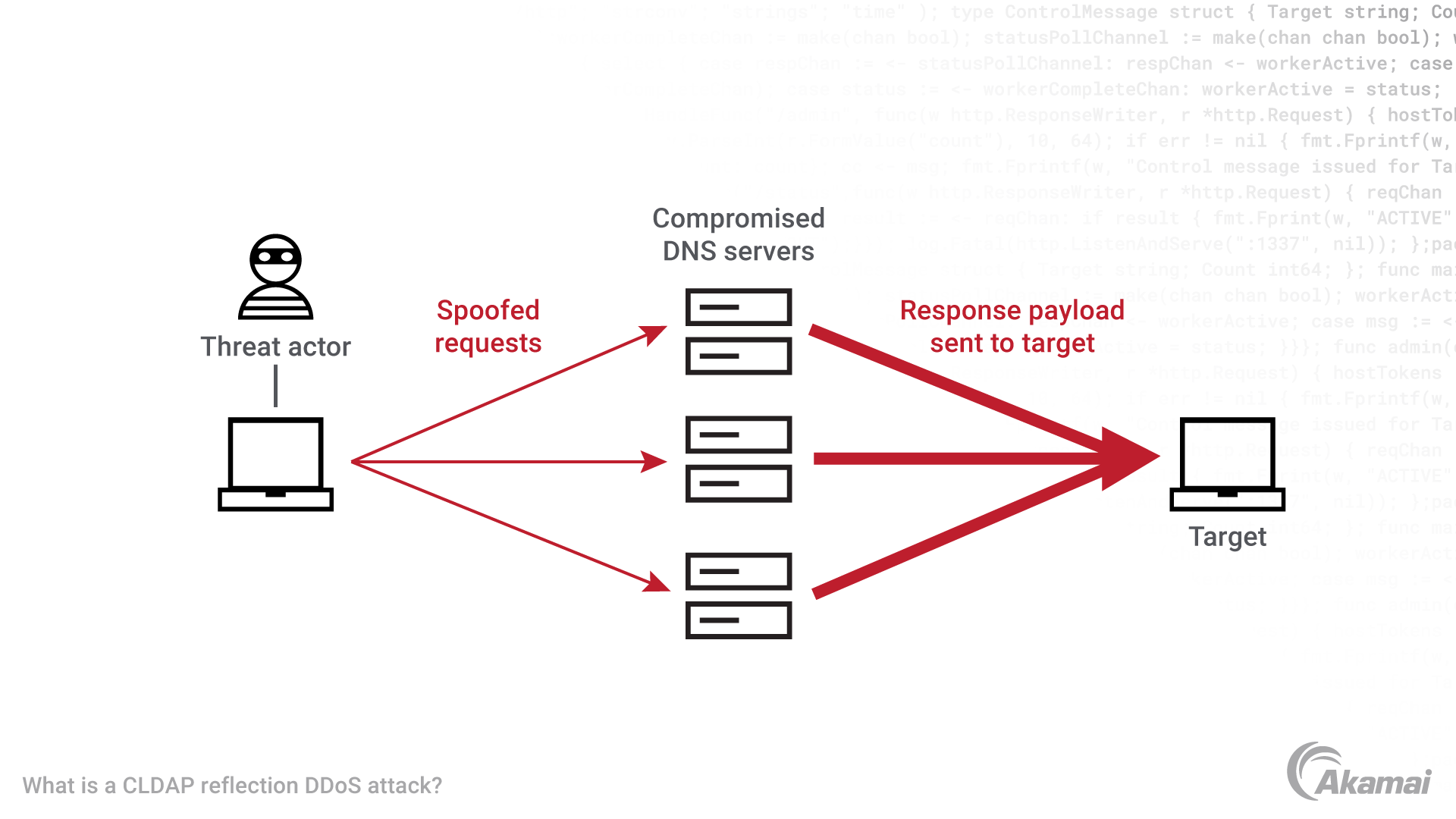
In this attack, the hackers send a large number of spoofed CLDAP requests to open servers on the internet. Usually, these DNS servers then respond to the spoofed requests, sending a much larger amount of data to the target network than was originally sent by the attacker. This amplification effect can result in a massive influx of data overwhelming the target network, rendering it inaccessible to legitimate users.
How does a CLDAP reflection DDoS attack work?
A CLDAP reflection DDoS attack works in three stages:
Reconnaissance: Attackers search for IP addresses of open servers that respond to CLDAP requests. This is usually done using automated tools that scan the internet for vulnerable servers. Most are discovered to be open DNS resolvers.
Spoofing: The attacker sends a large number of spoofed CLDAP requests to the open servers, making it appear as though the requests are coming from the target network.
Amplification: The open servers respond to the spoofed requests, sending a much larger amount of data to the target network than was originally sent by the attacker. This amplification factor (56–70 times the original request) can result in a massive influx of bandwidth and data overwhelming the target’s IP infrastructure.
Threat actors tend to prefer reflection and amplification attack vectors because they provide an easier return on their investment. They no longer have to maintain botnet infrastructure to leverage these CLDAP reflectors, or other known types like SNMP, SSDP, Chargen, Memcached, and NTP, and these tend to use UDP-based attack traffic.
Now that they have performed the minimum three stages above, the denial-of-service attacks are easy to orchestrate. Simply launching a script, they have the source IP addresses of the open CLDAP servers, they have the victim’s IP address for the targeted endpoint and destination port, and now they can begin their attack campaign. Over the years, Akamai cybersecurity experts have tracked the use of these attack vectors, and average attack size ranges from 1 Gbps to 60 Gbps. Forwarding rates have been recorded anywhere from 1 Mpps to 30 Mpps, giving CLDAP a respectable amplification factor.
How can you protect yourself from a CLDAP reflection DDoS attack?
There are several steps you can take to protect your network from a CLDAP reflection DDoS attack:
- Disable the CLDAP protocol: If you do not use the LDAP or CLDAP protocol, it is recommended that you disable it on all devices and servers facing the internet to prevent attackers from exploiting its weaknesses.
- Implement access control lists (ACLs): ACLs can be used to restrict access to CLDAP servers, limiting ingress access to a number of open servers that can be exploited by attackers.
- Use a DDoS protection service: DDoS mitigation services can detect and stop DDoS attacks, including CLDAP Reflection DDoS, before they can reach your network.
- Keep your systems up to date: Regularly patching and updating your systems can help prevent attackers from exploiting known vulnerabilities.
- Monitor network traffic: Monitoring network traffic can help detect unusual activity and allow you to take action before an attack occurs.
- Limit rate: Limiting the number of ingress or egress requests and responses can reduce the likelihood for these CLDAP or LDAP servers to be overwhelmed.
Frequently Asked Questions (FAQ)
A DDoS attack involves overwhelming a network with traffic from multiple sources. A CLDAP reflection DDoS attack involves the use of a specific type of server to amplify the size of the attack and is considered a specific type of DDoS attack vector.
While it is difficult to completely prevent a CLDAP reflection DDoS attack, organizations can take steps to mitigate the risk, including using firewalls and intrusion detection/prevention systems, regularly updating and patching software and operating systems, implementing proper network access controls, and engaging services with cloud service providers.
Conclusion
The CLDAP reflection DDoS attack is a serious cyberthreat that organizations must be aware of and take steps to protect against. By understanding how these attacks work and implementing appropriate security measures, organizations can reduce the risk of a CLDAP reflection DDoS attack and mitigate the potential impacts of such an attack.
Why customers choose Akamai
Akamai powers and protects life online. Leading companies worldwide choose Akamai to build, deliver, and secure their digital experiences — helping billions of people live, work, and play every day. Akamai Connected Cloud, a massively distributed edge and cloud platform, puts apps and experiences closer to users and keeps threats farther away.