DNSSEC is the protocol extension responsible for authenticating responses and preventing DNS poisoning attacks. However, DNSSEC does not protect against DDoS. In fact, DNSSEC protected zones are often targets for DNS amplification attacks, as attackers recognize that signed responses are larger than standard DNS messages since they include additional record types (NSEC, RRSIG).
DNS and DDoS
A distributed denial of service (DDoS) is an attempt to employ a network of distributed machines to overwhelm a target’s computational resources until it is no longer functional or performant. DNS (Domain Name System) is a common target for DDoS attacks since a website’s or application’s critical services are contingent upon names being translated to IP addresses without interruption. This type of malicious traffic can prove difficult to mitigate without disrupting legitimate queries, since DNS nameservers often only have visibility into the resolver’s IP address — an intermediary that is responsible for continually resolving recursive queries from a potentially large pool of users. As a result, blocking or rate limiting traffic based on this address is likely to result in false positives. In addition, volumetric DNS attacks can be difficult for Layer 3 scrubbing centers to successfully isolate, since DNS DDoS queries often advertise relatively low bps (bits per second) or pps (packets per second) rates compared to overall traffic.
There are a variety of different DNS DDoS attacks, but most can be classified into two groups: DNS flood and DNS amplification.
What is a DNS flood attack?
DNS flood attacks attempt to exhaust the resources of a DNS nameserver by sending an overwhelming number of queries. Sophisticated attackers will leverage distributed botnets to obfuscate the attack by sourcing the malicious traffic from a variety of recursive resolvers.
A common DNS flood technique is a NXDOMAIN attack, aka Pseudo Random Subdomain (PRSD), where malicious actors will trigger excessive requests for nonexistent domains (e.g., doesnotexist.example.com) to consume an authoritative nameserver’s resources while exhausting a recursive resolver’s cache pool. A successful DNS flood attack can thus increase DNS resolution times for legitimate queries or even achieve an outright DoS.
What is a DNS amplification attack?
Instead of targeting the nameserver responding to a malicious query, a DNS amplification attack attempts to cripple another machine’s resources by sending a substantial number of DNS requests to a spoofed source IP address. The attack is similar to sending someone a letter in the mail with a fabricated return address and requesting a response. As a result, DNS messages will be directed to an unsuspecting third party that never requested the data in the first place. Attackers will typically submit a request for as much zone information as possible, to maximize the amplification effect with the hope of overwhelming the victim with useless incoming bandwidth.
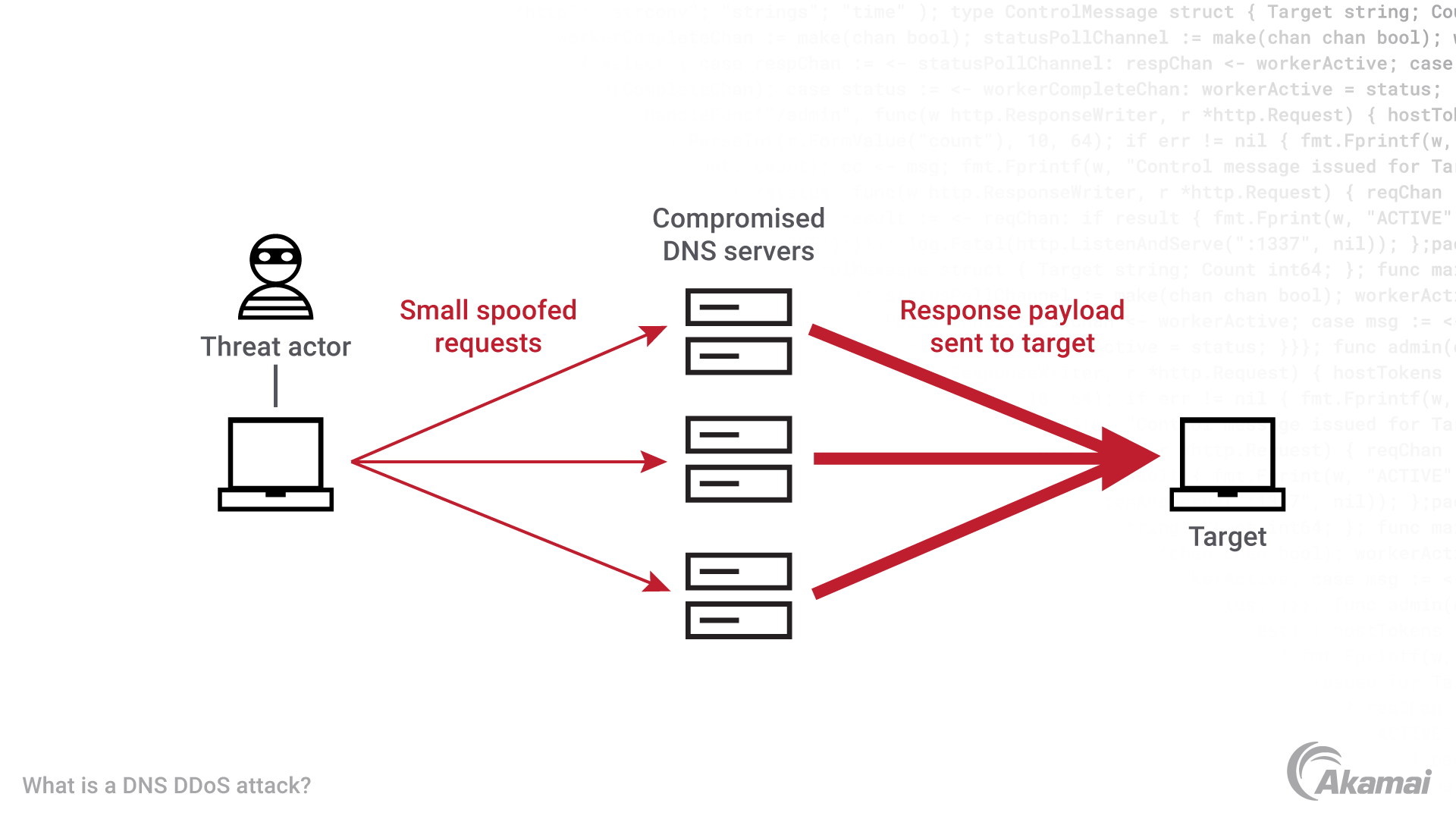
Malicious actors often choose to exploit DNS for this type of “reflection” attack since it offers more attack ammunition than HTTP. HTTP connections require a TCP handshake, and thus the largest response that will be sent to the target will be TCP SYN-ACK packets, which include a relatively small amount of data. However, DNS messages are typically transported by UDP, a connectionless protocol, so larger messages can be sent to any destination without a prior acknowledgement.
What are common methods to help protect against DNS DDoS attacks?
While it is difficult to detect and mitigate DNS DDoS attacks without disrupting legitimate users, there are several techniques that are recommended to improve protections:
- A geographically distributed anycast DNS network expands the surface area to absorb large-scale attacks.
- Increasing record TTLs can help reduce both legitimate and illegitimate queries from reaching authoritative nameservers, which can save nameserver bandwidth.
- Disabling DNS ANY requests, the largest possible DNS response, prevents attacks from exploiting this record type to augment amplification attacks.
- While it may prove difficult to block DNS queries without interrupting legitimate requests, many DNS servers have the ability to delay responses to save bandwidth if a certain resolver is sending an excessive amount of traffic. More sophisticated servers can incorporate nuanced rate limiting logic, such as queuing requests from a specific resolver or client that is responsible for a spike in NXDOMAIN responses.
How can Akamai help?
Akamai Edge DNS is a cloud-based DNS solution that is uniquely positioned to defend against the largest DDoS attacks. With over 300 points of presence (PoPs), standard customer traffic typically consumes less than 1% of total nameserver capacity, leaving malicious actors little opportunity to successfully administer distributed, volumetric attacks. In addition, Edge DNS is built on a highly resilient anycast network, so queries are seamlessly routed by BGP to the topologically closest PoP, and in the rare occasion a node or region is down, traffic will be directed to a healthy nameserver via the platform’s built-in failover mechanisms. Along with sophisticated rate-limiting capabilities, these unique, resilient characteristics ensure Edge DNS can guarantee a 100% uptime SLA.
Frequently Asked Questions (FAQ)
Relying on multiple cloud DNS providers to answer queries can offer a safety net in case of a provider outage, as resolvers will typically retry another NS record if an initial attempt to contact a nameserver fails. However, each provider may have different record capabilities that, if not fully accounted for, could lead to problematic handout inconsistencies, performance degradations, or even outright DoS. DNS admins should specifically review each provider’s ALIAS record capabilities and DNSSEC support if they plan to implement these features.
Anycast is a network addressing and routing technique that allows IP addresses to be announced from multiple points on the internet. Combined with a geo-distributed DNS footprint, an anycast implementation increases the server surface area to absorb large-scale DDoS attacks, as several nodes can absorb distributed malicious traffic against an individual IP. Unicast, which assigns one IP per destination, introduces a higher likelihood of a centralized single point of failure for attackers to exploit. In addition, it is difficult to scale a distributed DNS network with a unicast implementation since many registrars have glue record limits, and assigning a large number of A record outputs to an NS record lookup introduces operational challenges and performance drawbacks. As a result, anycast offers a more performant, scalable option to implement a distributed and resilient DNS posture.
Why customers choose Akamai
Akamai powers and protects life online. Leading companies worldwide choose Akamai to build, deliver, and secure their digital experiences — helping billions of people live, work, and play every day. Akamai Connected Cloud, a massively distributed edge and cloud platform, puts apps and experiences closer to users and keeps threats farther away.

