Akamai powers and protects life online. Leading companies worldwide choose Akamai to build, deliver, and secure their digital experiences — helping billions of people live, work, and play every day. Akamai Connected Cloud, a massively distributed edge and cloud platform, puts apps and experiences closer to users and keeps threats farther away.

What Is a Slowloris DDoS Attack?
Slowloris DDoS Attacks Explained
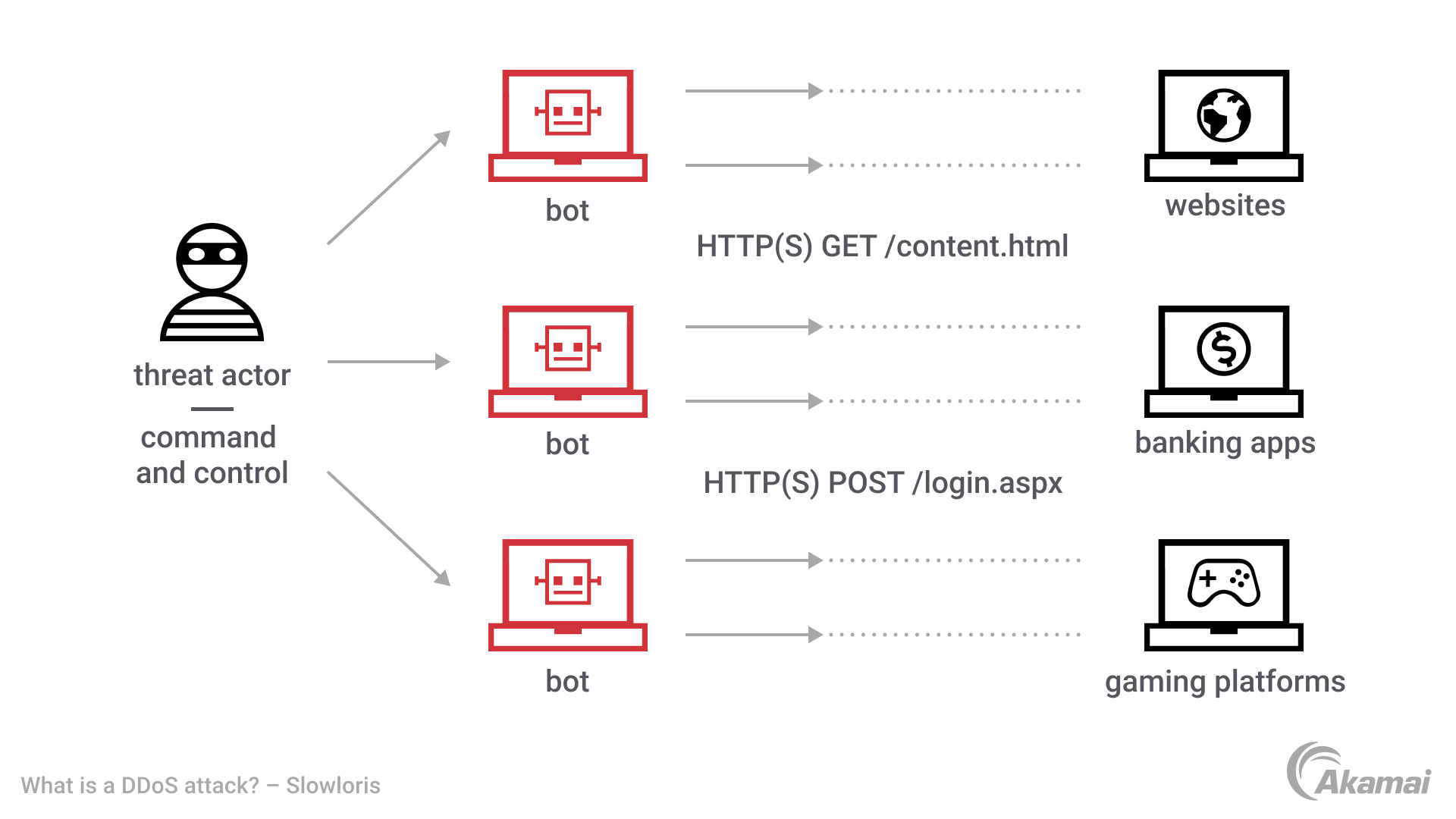
A Slowloris DDoS attack is a type of distributed denial-of-service attack that targets Layer 7 of the OSI model. This type of cyber abuse was designed to overwhelm a single computer, web server, database, or API by opening and maintaining many simultaneous TCP connections to a target FQDN and generating a low rate and/or volumes of HTTP requests or HTTP connections per connected session. Some attacking IPs will open many TCP connection attempts and use those additional open connections or sessions, combining incoming requests to exhaust application or database resources. Named after the slow loris — a slow-moving, Asian primate — a Slowloris attack may last for an extended period of time when undetected. Slowloris attacks were introduced into the mainstream via common attack tool frameworks like HOIC (High Orbit Ion Cannon) and LOIC (Low Orbit Ion Cannon) used by Anonymous, the Iranian government, Killnet, and other threat actor groups. Today, we see other threat actors leveraging these same techniques, but with modernized infrastructure and command and control.
What is a Slowloris DDoS attack designed to accomplish?
This type of DDoS attack is a simple but elegant method that allows an attacker to take down a web server with very low complexity. Being able to identify them and control the quality of mitigation is what makes this denial-of-service attack complex. A Slowloris attack can be implemented with minimal bandwidth, is usually written in Python, and has proven to be extremely effective against many types of web server software, especially Apache 1.x and 2.x. These types of attacks were designed to look like legitimate requests and bypass mitigation filters.
Unlike bandwidth-consuming, reflection-based DDoS attacks, Slowloris uses up server resources with HTTP requests that seem slower than usual but otherwise appear to be standard compliant traffic. Attackers take advantage of a feature unique to the HTTP protocol: the ability for clients to split GET or POST HTTP requests into several packets or sessions. Attackers use Slowloris to target web servers by opening multiple connections and keeping them open as long as possible. This is accomplished by distributing HTTP requests across globally diverse botnet IP addresses and multithreading TCP connections per source. To keep the connection open, the Slowloris software may send HTTP headers for each request just before a TCP connection will time out, causing the denial of service. Eventually, the targeted server reaches the limit of its simultaneous connection pool and cannot process other requests, effectively denying service to other legitimate services. There can be other network infrastructure that is affected by Slowloris DDoS attacks — for instance, Local Traffic Managers (LTMs) or other technologies handling TCP session management.
Why is a Slowloris DDoS attack effective?
A Slowloris DDoS attack is considered a distributed denial of service, and it can remain undetected by traditional intrusion detection systems by sending legitimate HTTP request packets at low request-per-second rates, rather than large volumes or high rates of HTTP requests per second. Additionally, since the log file cannot be written until a request is completed, Slowloris can immobilize a server for periods of time without a single entry appearing in the log file to raise a red flag for anyone monitoring it.
What is a Slowloris DDoS attack vs. a traditional application DDoS attack?
Traditional application DDoS attacks are designed to take down a server by flooding it with an overwhelming number of HTTP requests, which requires substantial resources from the attacker. In contrast, a Slowloris attack may require only a few hundred requests at long, low, and regular intervals, rather than tens of thousands of HTTP requests on an ongoing basis. Bandwidth is not a key measurement for detecting this type of DDoS. Instead, security teams should assess the standard number of connection attempts, open connections, connection pools, incoming HTTP requests, partial HTTP requests, maximum number of allowed connections per source IP address, load balancers maintaining session tables, web server logging infrastructure, and other network or system paths throughout the DMZ.
What is the best way to stop a Slowloris attack?
Slowloris attacks can be mitigated by:
Limiting the number of connections a single IP address may request to open.
Increasing the minimum transfer speed allowed for any connection.
Limiting the time a client is allowed to stay connected.
Increasing the maximum number of clients the server will allow.
Deploying robust cloud mitigation services, configuring robust load balancers, using web application firewalls (WAFs) or other virtual patching techniques, and rate-limiting the number of requests per source.
How is a Slowloris attack conducted?
A Slowloris attack is executed in four steps:
The attacker issues command and control instructions to their botnet or reverse proxies, which sends multiple HTTP requests, randomized headers, and other bypassing techniques, while opening multiple connections to a targeted server from their global networks.
The targeted server opens a TCP connection for each request, planning to close the thread as soon as the HTTP request is completed. The server will time out any connection that is excessively long, to free up the thread for subsequent requests.
To prevent threads from timing out, the attacker will intermittently send partial request headers or additional HTTP requests to keep the targeted web server alive, effectively convincing the server to wait for the HTTP request to be completed.
While waiting for more HTTP requests and TCP connections to be initiated, the target server eventually runs out of available connections and is no longer able to respond to requests from legitimate traffic, leading to denial of service..
Why do Slowloris DDoS attacks occur?
Cybercriminals may launch an attack to bring down the website of a rival or enemy; as part of a political hacktivism campaign; or to draw attention away from other, more dangerous security breaches in progress, called smokescreen attacks. This attack is also commonly used because it is difficult to identify a signature and rate of abuse. Implementing mitigation for these types of attacks can lead to high false positive rates and impact the experience of the user accessing different modules of the web server or web application.
Increase resilience against complex DDoS threats with Akamai
With the world’s most distributed compute platform from cloud to edge, Akamai makes it easy for businesses to develop and run applications while keeping experiences closer to users and threats farther away. Along with our compute and delivery solutions, our suite of leading IT security products helps global companies make life better for billions of people, billions of times each day.
Our security solutions prevent and mitigate DDoS attacks through a transparent mesh of dedicated edge, distributed DNS, and cloud-scrubbing defenses. These purpose-built cloud solutions are designed to reduce attack surfaces, and improve quality and mitigation, while reducing false positives and increasing defense effectiveness. Having the capacity, experience, and diverse and mature technology stack allows our customers to rely on our 100% platform uptime and industry-leading mitigation SLAs.
App & API Protector provides a holistic set of powerful protections with customer-focused automation. While this solution offers some of the most advanced application security automation available today, it remains simple to use. A new adaptive security engine and industry-leading core technologies enable DDoS protection, API security, bot mitigation, and a web application firewall in an easy-to-use solution.
Prolexic stops DDoS attacks with the fastest and most effective defense at scale. Offering a zero-second SLA for DDoS defense, Prolexic proactively reduces attack services and customizes mitigation controls to network traffic to block attacks instantly. Having a fully managed SOCC complements your existing cybersecurity programs and will help augment your time to resolution with industry-proven experiences.
Web Application Protector protects web apps and APIs effortlessly by detecting threats with crowdsourced intelligence. Dynamic protection and self-tuning machine learning reduce effort and false positives. This Akamai solution offers zero-second DDoS mitigation in response to application-layer attacks within seconds.
Edge DNS prevents DNS outages with the largest edge platform, enabling organizations to count on guaranteed, nonstop DNS availability. A cloud-based solution, Edge DNS ensures 24/7 DNS availability while improving responsiveness and defending against the largest DDoS attacks.
Why customers choose Akamai
Related Products
Prolexic
Stop DDoS attacks with the fastest, most effective defense — at scale.
Edge DNS
Rely on highly secure DNS for nonstop availability of web apps and APIs.
App & API Protector
One-stop, zero-compromise security for websites, applications, and APIs.
Additional Resources
DDoS Defense in a Hybrid Cloud World

All DDoS mitigation is not created equal. See how many cloud service providers fall short, and what to look out for.
What can an analysis of malicious DNS traffic reveal about an organization’s risk exposure?

DNS is one of the oldest internet infrastructures. However, an incredible amount of attack traffic passes through it. Details about the most prevalent threats and more can be found in this report.
Related Pages
Learn more about related topics and technologies on the pages listed below.