An account takeover attack is a form of cybercrime where attackers gain unauthorized access to a user or business online account in order to steal account information from financial institutions, transfer funds, or access privileged information.
Preventing account takeover attacks
Account takeover (ATO) attacks are big business in the U.S. By impersonating legitimate account owners, cybercriminals can gain unauthorized access to user accounts and use those privileges to execute a variety of fraudulent activities, including initiating wire transfers to fraudulent bank accounts and stealing intellectual property.
The impact of an account takeover, however, extends far beyond the loss of money and data. Loss of reputation and customer trust can cause much greater damage than the financial setback of a fraudulent wire transfer.
Akamai Account Protector offers a comprehensive solution designed to prevent ATO attacks and mitigate the sophisticated, adversarial bots and botnets that often precede a takeover attempt. With technology that assesses the risk of each authentication request by tracking anomalies from the typical behavior of legitimate users, Account Protector enables organizations to verify and trust the validity of user logins without adding extra friction.
How account takeover works
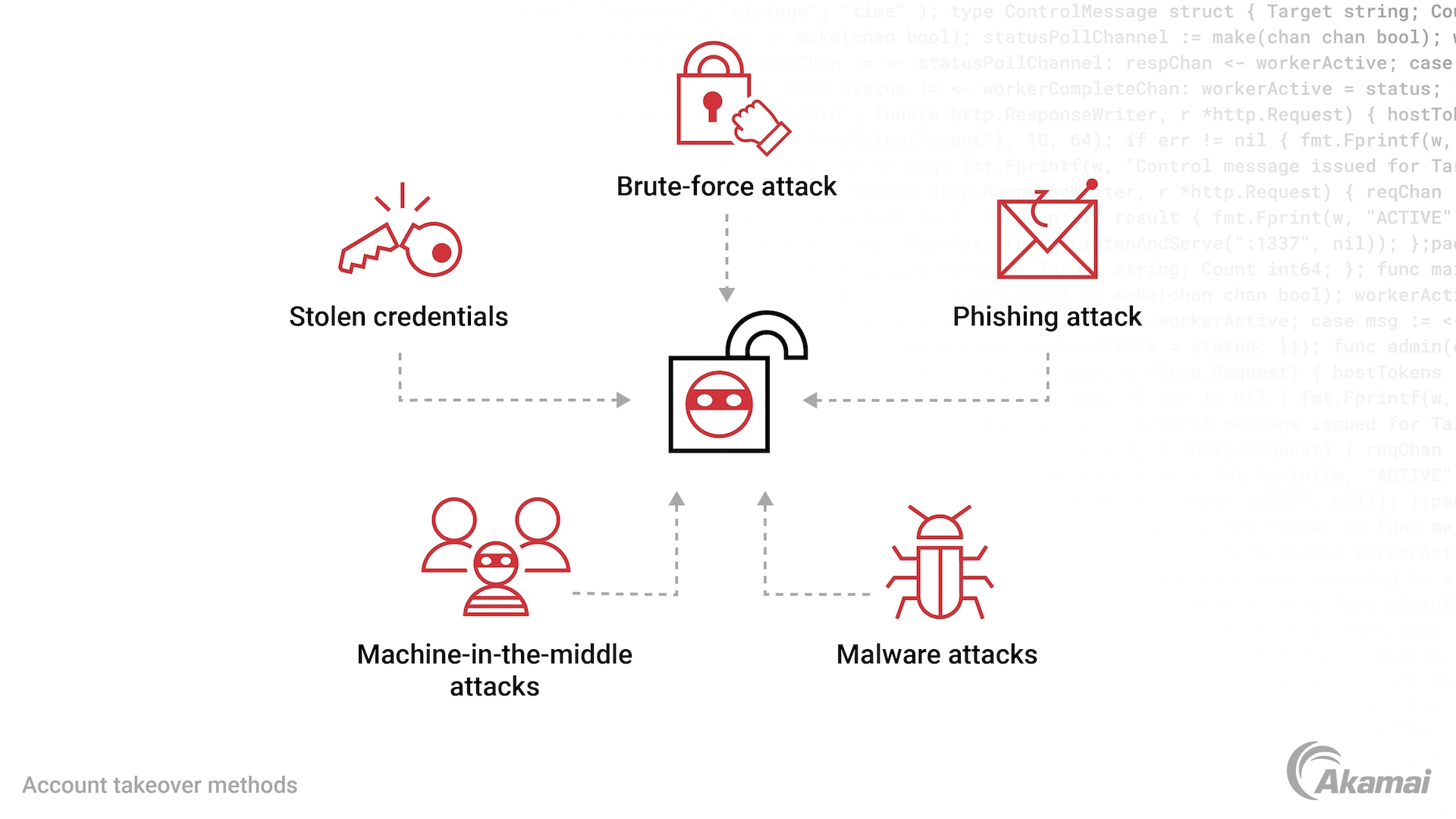
Cybercriminals may take over an account using a variety of methods.
- Stolen credentials. Data breaches often result in the leaking or theft of thousands or millions of usernames and passwords, which hackers can use to gain access to accounts through credential stuffing attacks
- Brute-force attack. Threat actors attempt to access accounts using random username/password combinations, employing a bot network to make thousands of login attempts per hour.
- Phishing attacks. Phishing campaigns dupe users into sharing login credentials via bogus websites, chats, emails, SMS, and other channels.
- Machine-in-the-middle attacks. In this common attack vector, cybercriminals position themselves between the user and unencrypted traffic so they can intercept and alter sensitive data traveling between them.
- Malware attacks. Attackers may use malware such as keyloggers to expose personal data, including user credentials.
In the United States alone, losses from account takeover fraud and new account fraud are estimated at more than $10 billion annually. However, the damages from account takeover scams can reach far beyond the theft of money and data. Businesses may lose customers and potential future revenue, and the company’s brand and reputation may suffer as customers who have experienced account takeover attempts lose trust.
Akamai Account Protector
Akamai Account Protector is designed to detect fraudsters at the edge while allowing customers to get through without added friction. This Akamai solution deploys techniques for understanding the behavior of legitimate account owners, then assesses the risk of each authentication request by searching for anomalies from typical behavior. When there is suspicious activity around an authentication request, Akamai Account Protector applies an appropriate response in real time, without affecting the experience of real account owners.
With Account Protector, you can:
- Preserve customer trust. Protect customers and partners from fraudulent activity by knowing which interactions are legitimate and which are not. Reduce friction for users while protecting customer accounts and enhancing security for the organization.
- Customize protections. Akamai’s bot detection technology features autotuning capabilities that learn the normal traffic patterns of your sites and automatically tune detections based on unique patterns. The ability to compare an individual request to user population profiles enables more customized anomaly detections and protection.
- Gain greater visibility. With Akamai, security and fraud teams can take action based on transparent signals and indicators, rather than on black box analyses.
- Reduce fallout. When you can detect vulnerabilities and prevent account takeover, you can reduce the financial and resource strains of investigating compromised accounts, replacing stolen assets, creating regulatory and legal reports, and managing user complaints.
- Make data-driven decisions. The risk and trust signals in Account Protector can be integrated with fraud, identity theft, SIEM, and other cybersecurity tools to enhance security investments and make more strategic security choices.
How Account Protector works
Account Protector prevents account takeover by using behavioral detections to profile and understand the normal activity patterns of account owners as well as device anomalies and source reputation. When a customer login request is received, Account Protector assesses in real time the risk that the request does not belong to a legitimate account owner. This fraud detection is accomplished by comparing the request to typical user behavior profiles, which can include devices normally used, IP addresses, locations, networks, and the frequency and time of logins.
Account Protector also uses sophisticated anti-bot detections to catch and mitigate adversarial bots and stop automated, large-scale attacks. Using AI and machine learning models and techniques, this Akamai anti-bot technology detects and mitigates bot traffic based on user behavior/telemetry analysis, browser fingerprinting, HTTP anomaly detection, automated browser detection, high request rates, and more.
Frequently Asked Questions (FAQ)
Credential stuffing is a form of a brute-force attack where attackers use login credentials stolen from a data breach to attempt account takeover. Credential stuffing attacks are effective because users often reuse the same password and username combination across many websites.
Why customers choose Akamai
Akamai powers and protects life online. Leading companies worldwide choose Akamai to build, deliver, and secure their digital experiences — helping billions of people live, work, and play every day. Akamai Connected Cloud, a massively distributed edge and cloud platform, puts apps and experiences closer to users and keeps threats farther away.