A VPN (virtual private network) replaces your own IP address with an IP address managed by a VPN provider. The device will look like it has connected to an internet connection from a different geolocation. Having an IP address that is not your actual IP address helps hide online activity.
What is an IP address and how is it used?
Let’s look now at how IP packets are addressed and how a packet finds its destination. We will do this through a series of analogies, eventually coming back to our postal service analogy.
The question we’re going to answer is: How does a packet find its destination?
The internet consists of millions of routers and pipes that interconnect billions of hosts. A host is simply an endpoint that communicates over the internet. Hosts include servers, laptops, smartphones, and other devices. When a host wants to send a packet to another host, that packet has to traverse a path through the internet, specifically through the routers and pipes that make up the internet. The pipes are the physical links that connect routers to each other and to hosts.
Routers connect multiple pipes and have to make the routing decisions. That is, when a packet comes in on a link, the router has to determine which link to send it out on. This is the job of the router’s routing table. To understand routing tables, we will go through a series of analogies.
For our first analogy, let’s look at the internet as a network of streets. In this case, a packet going from host A to host B is like driving from city A to city B. A router, then, is like an intersection where multiple streets come together. When driving and we get to an intersection, we have to determine which way to turn, that is, which street to turn on to. A routing table, then, is like the direction sign that we hope to see at the intersection.
This analogy breaks, because a street sign cannot possibly list every possible city to which we might be going. Analogously, a routing table cannot possibly list every possible host to which a packet might be destined. In other words, a packet’s destination address cannot be something like “Apple web server.”
An analogy that does work, though, is rooms on a hotel floor. In this case, a packet going from host A to host B is like walking from room A to room B. A router, then, is like an intersection where multiple corridors meet up, and the routing table is like the sign at the intersection that says rooms 201–220 to the right and rooms 221–240 to the left. If I’m going to room 211, I know that I turn right.
Why does this work? Well, for one thing, all of the room numbers in a range are in the same place. So we don’t need directions to each room, but just to each range. Also, importantly, all possible room numbers are covered by the ranges on the sign. There are no rooms numbered outside the range 201–240.
We can do the same thing on the internet. So rather than addressing hosts with names, we’re going to use numbers.
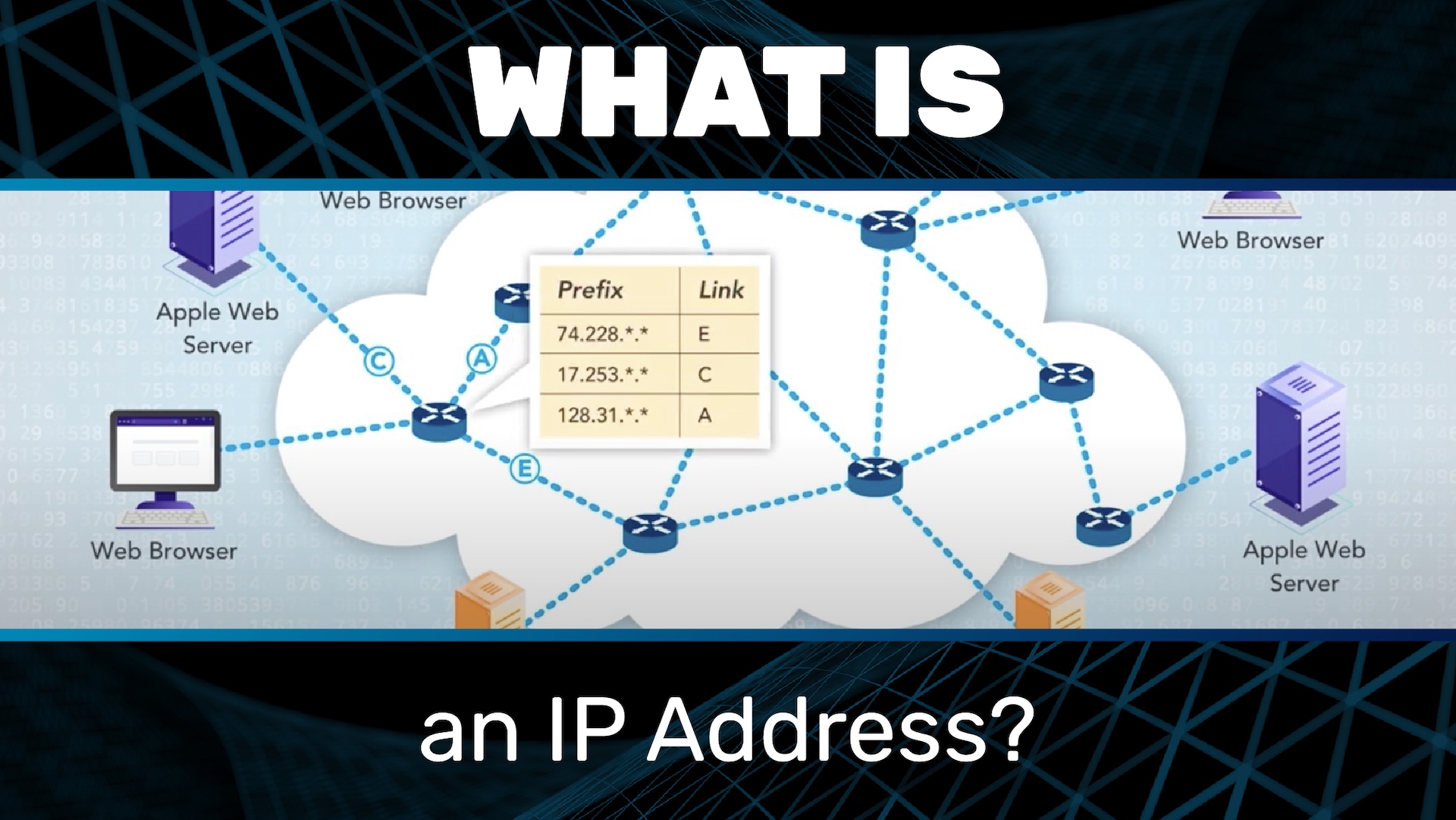
These numbers are called IP addresses, which are (32-bit) numbers. They are usually written in dotted notation, for example, 73.227.130.85. The numbers between the dots are called octets (because they are 8 bits). Hosts are located in contiguous ranges of IP addresses. For example, all hosts with addresses that start with 128.30.*. * and 128.31.*. * are at the Massachusetts Institute of Technology (MIT). Routers only need directions for each range. These ranges are called prefixes or CIDRs, which stands for Classless Inter-Domain Routing.
Let’s return now to our postal service analogy. Now, a packet going from host A to host B is like a letter sent from home A to home B. A router is like a post office. Letters come in on trucks and then have to be sorted to go out on other trucks, so a routing table is like the sorting rules for the letters. So let’s look more carefully at how letters are addressed and sorted.
Continuing our analogy, a packet addressed to 128.30.27.149 is analogous to a letter addressed to Lucille Ball, 1000 Roxbury Drive, Beverly Hills, CA 90210. To route this letter, most post offices don’t have to look at the whole address. In fact, only the 90210 post office has to look at the street address. All other post offices only have to look at the zip code. That is, the letter can go all the way from the sender to the 90210 post office, based only on the zip code.
We do the same thing with IP addresses. Each address is split into a left side and right side. The left side is called the prefix, and it is analogous to the zip code. Recall that all IP addresses with prefix 128.30 belong to MIT. So only the routers in the MIT network have to look at the whole IP address. All other routers on the internet only have to look at the prefix. That is, the packet can go all the way from the sender to the MIT network based only on the prefix.
A quick note: The divide between prefix and the rest of the IP address does not have to occur in the middle or even at an octet boundary, though for simplicity in this presentation, all examples will put the divide in the middle so the prefix is the first two octets.
Now we can see that instead of addressing IP packets with names, we have to address them with numbers, that is, with IP addresses. So instead of something like “Apple web server,” we have something like 17.253.207.54. And instead of “Bobby’s laptop,” we have 73.227.130.85.
We can also see now how a routing table works. A routing table simply maps prefixes to links, and the router sends the packet out on the link corresponding to the prefix that matches the destination IP address. In this example, the destination IP address is 17.253.207.54, which matches the prefix 17.253 on the second row of the table, so the packet goes out on link C.
The key point is that rather than having to list every possible host name or even every possible IP address, routing tables only need to list every possible prefix. Remember it’s analogous to routing letters by zip code instead of having to consider every possible street address.
The internet is a complex system of routers and pipes connecting billions of endpoints. An addressing system determines how the traffic moving through those pipes gets to its correct destination. An Internet Protocol address or IP address is a string of numbers that act as a unique identifier. Every device on the internet is assigned a unique IP address; just like the real-life address and zip code used to route a letter to a recipient, an IP address will route an IP packet to the correct place. An internet service provider (ISP) assigns a device an IP address. The success of this system has been vital in ensuring a reliable internet.
A short history of the IP address
Two versions of the Internet Protocol (IP) are used on the internet: IPv4 and IPv6. The latter is the latest version, and as of July 2023, IPv6 addresses were used by 21.6% of websites. IPv4 has limited space for IP addresses — up to 4.3 billion IP addresses — but the latest version, IPv6, is more scalable, with room for trillions of IP addresses. This expansion was vital to scale and accommodate new types of internet-connected devices. Every type of network device is given an IP address. As such, IP addresses are an intrinsic part of the building blocks of the internet. An IP address is essential for accurate and efficient data transfer between connected devices.
IP addresses are assigned by the Internet Assigned Numbers Authority (IANA). The full range of IP addresses is 0.0.0.0 to 255.255.255.255.
How are IP addresses, IP packets, and HTTP connected?
Hypertext Transfer Protocol (HTTP) is an application-level protocol that uses request-response flows to transmit data across the internet; HTTP belongs to the TCP/IP family of standards. IP packets use HTTP flows to transmit data to perform tasks such as displaying a web page. Each server or client on a TCP/IP is assigned an IP address. This IP address is contained within an IP packet.
What is an IP address, and how does it work?
An IP packet contains the IP addresses of the source and destination. An IP address comprises 32-bit numbers, usually written in dot notation, for example, 73.227.130.85. The numbers between the dots are called octets (8 bits). A real-world analogy that helps to visualize how IP addresses work is that of a letter in an envelope. For example, imagine a letter addressed to the mailing address “Lucille Ball, 1000 Roxbury Drive, Beverly Hills, CA 90210.” When the sender’s post office routes this letter, they focus on the zip code, 90210, rather than the complete address. This allows the letter to be quickly routed from the sender to the 90210 post office. Once at the local post office, this office uses the street address and house number to route it to the correct recipient, Lucille Ball.
IP addresses work similarly. Each address is split into a left side and a right side. The left side is analogous to the zip code. For example, the IP addresses 128.30.*.* and 128.31.*.* belong to the Massachusetts Institute of Technology (MIT). A router uses the left-side ranges known as prefixes or CIDRs (Classless Inter-Domain Routing) like a post office uses a zip code to direct the local router. Once at the local router, the whole IP address is used, the right side of the IP address pointing to the specific device, such as a laptop or mobile phone, on the network.
What is IP routing?
IP routing is used to transmit packets from a host on one network to a host on another network. A router typically performs this process: Routers connect multiple pipes and make the routing decisions. Routers examine the destination IP address of a packet before deciding on the next hop to send the packet onward. Pipes are the physical links connecting routers to each other and hosts (endpoints). When an IP packet arrives, the router must determine which link (pipe) to send it out on. This is the job of the router’s routing table.
What is a routing table?
Routers use routing tables to decide on the optimal next-hop address to forward the packet.
Rather than listing every possible hostname or IP address, routing tables only need to list every possible prefix. In other words, the routing table uses the zip code equivalent, i.e., the IP address prefix. The routing table directs the router similarly to a signpost at an intersection of multiple rooms on a hotel floor. A router is an intersection where numerous corridors meet; the routing table is like the sign at the intersection that says rooms 201–220 to the right and rooms 221–240 to the left. If you are headed to room 211, you know to turn right. In summation, a routing table maps prefixes to links, and the router sends the packet out on the link corresponding to the prefix that matches the destination IP address.
Akamai, IP addresses, and internet-borne attacks
Cloud-based cyberattacks are ubiquitous. Akamai is dedicated to eradicating internet-borne web exploits used by hackers and cybercriminals. IP packet loss can be caused by distributed denial-of-service (DDoS) attacks against a web server. Our dedicated infrastructure provides DDoS prevention to stop attacks in the cloud before they reach applications, data centers, and internet-facing infrastructure (public or private). Akamai's unique architecture segments DNS resources across dedicated, non-overlapping clouds. More than 225 frontline SOCC responders back Akamai; our fully managed solution filters out attack traffic and stops even the most significant attacks, freeing your defenders to focus on high-priority security programs. Akamai protects the modern enterprise from vulnerabilities introduced by the cloud and a distributed workforce.
Akamai and cybersecurity
Akamai’s authority in cybersecurity was built upon a deep understanding of how protocols such as IP, HTTP, and HTTPS work. As well as security, Akamai optimizes cloud computing with our suite of cloud computing solutions, provides security, scalability, and visibility, and is agnostic to the cloud service provider. Our cloud computing product suite includes the Download Delivery product line that optimizes large HTTP file downloads flawlessly, every time, at a global scale.
Frequently Asked Questions (FAQ)
There are four types of IP addresses: public, private, static, and dynamic.
The divide between prefix and the rest of the IP address does not have to occur in the middle or even at an octet boundary.
Dynamic Host Configuration Protocol (DHCP) is a client/server protocol that assigns an Internet Protocol (IP) host with its IP address.
The Domain Name System (DNS) network maps an IP address to a domain name, such as apple.com
Why customers choose Akamai
Akamai powers and protects life online. Leading companies worldwide choose Akamai to build, deliver, and secure their digital experiences — helping billions of people live, work, and play every day. Akamai Connected Cloud, a massively distributed edge and cloud platform, puts apps and experiences closer to users and keeps threats farther away.