APIs may be targeted by hackers attempting to steal sensitive data, to gain unauthorized access to IT networks, or to disrupt or damage an organization. API attacks often begin by exploiting security vulnerabilities or a security misconfiguration, and attacks commonly involve SQL injection, broken access controls, distributed denial of service (DDoS), and manipulator-in-the-middle (MITM) techniques, which are all outlined by the OWASP Top 10.
Why do I need API security?
API is the abbreviation for application programming interface. Gartner has predicted that API abuse will “move from an infrequent to the most-frequent attack vector, resulting in data breaches for enterprise web applications.” Just like you would protect your basic information, like the password tied to your user identity on social media, it is equally important on the back end to protect API access, so that identifiers like API keys and API calls do not get misused.
It’s not surprising that APIs represent an increasing security risk, because any web application or web service available is almost certainly supported in some way by an API. From mobile applications and Internet of Things (IoT) devices, to internal applications and cloud-based customer services, to microservices architectures, APIs make your business communication and transactions possible.
Consequently, web API security and API management must be a critical priority for your IT teams throughout the entire lifecycle of your APIs. But protecting APIs from security threats can be a complex challenge, thanks to cloud migration, modern DevOps practices, and constantly evolving APIs.
Akamai can help. Akamai App & API Protector delivers zero-compromise security for websites, applications, and APIs. By automatically discovering and bringing greater visibility to APIs, App & API Protector helps you successfully defend APIs from threats while reducing your attack surface.
Best practices for API security
When implementing controls and protocols to protect APIs, keep these best practices in mind.
1. Discover and track all APIs. Organizations often experience security incidents with APIs they were not even aware of, and this can be related to an API provider. Knowing the location and purpose of APIs — including external APIs that your organization consumes — is essential to protecting them. By paying attention to API development, you can begin tracking APIs from the beginning.
2. Identify vulnerabilities. Use security testing tools to identify vulnerabilities that exist within each API. Begin by searching for logic calls, hard-coded keys, and the potential that API traffic could be compromised by an impersonation attack. Scan storage and repositories for keys that could be used to compromise APIs. Once vulnerabilities are identified, they must be prioritized for remediation and correct configuration based on risk tolerance.
3. Leverage existing security solutions. Start with existing solutions such as WAF infrastructure, identity management, data protection, and specialized API security technologies, ensuring that there are plans in place for continuous API security.
4. Set blanket API security policies. Rather than using unique policies for each API, implement a blanket set of policies that can be reused. Avoid coding policy directly into APIs — this adds unnecessary complexity and denies visibility. Make null the default access level to any API resource, requiring constant authentication.
Akamai App & API Protector
App & API Protector secures entire API and web estates with powerful protections for simplicity and automation across the Open Web Application Security Project® (OWASP) Top 10. This API and web application security solution combines many industry-leading core technologies in API security, web application firewall, DDoS protection, and bot mitigation providing your teams with a single solution that is simple to use. With App & API Protector, you can automatically discover and protect APIs from vulnerabilities, including the OWASP API Security Top 10.
Advanced capabilities for API security
Often, API vulnerabilities exist due to a lack of API visibility, and Akamai makes it easy to automatically discover a full range of known, unknown, and changing APIs across web traffic, including API endpoints, definitions, and traffic profiles. This helps to protect against hidden attacks, reveal unexpected changes, and find errors. Newly discovered APIs can be easily registered with a few clicks, and all API requests are automatically inspected for malicious code, ensuring strong API security by default.
Adaptive, self-tuning security
An adaptive, threat-based detection engine correlates data from each API request with threat intelligence collected from across the Akamai platform making it possible to detect up to 2x more attacks with a 5x reduction in false positives vs. Akamai’s previous detection technology. To stop both common and highly targeted attacks with remarkable precision, Akamai customizes and applies advanced decision-making logic to the traffic of your specific IT ecosystem. Self-tuning capabilities reduce operational friction and administrative overhead. Policy-specific tuning recommendations are developed by automatically analyzing all security triggers — including actual attacks and false positives.
Bot visibility and mitigation
Integrated bot capabilities enable your teams to monitor bot activity, detect and stop unwanted bots, and mitigate bot attacks Akamai provides real-time visibility into bot traffic along with an expansive directory of more than 1,750 known bots, enabling your teams to investigate skewed web analytics, prevent origin overload, and create custom bot definitions.
Automatic updates
Akamai App & API Protector’s adaptive security engine is automatically updated with threat intelligence from the Akamai platform. Our threat researchers analyze more than 300 TB of daily attack data using machine learning to identify new attack vectors or permutations of existing threats. With this level of analysis, you can instantly drop network-layer DDoS attacks and respond to application-layer attacks within seconds. Akamai also provides an open source Terraform API utility through GitHub, which allows for easier integration of App & API Protector into the DevOps workflow.
Frequently Asked Questions (FAQ)
An application programming interface, or API, is a software program that enables two software applications to communicate with each other using a common set of protocols and definitions.
A representational state transfer (REST) API is a type of software infrastructure that allows for more protection while still offering flexibility. The most popular format for information delivery is JSON, which is the easiest format for most humans and machines to understand.
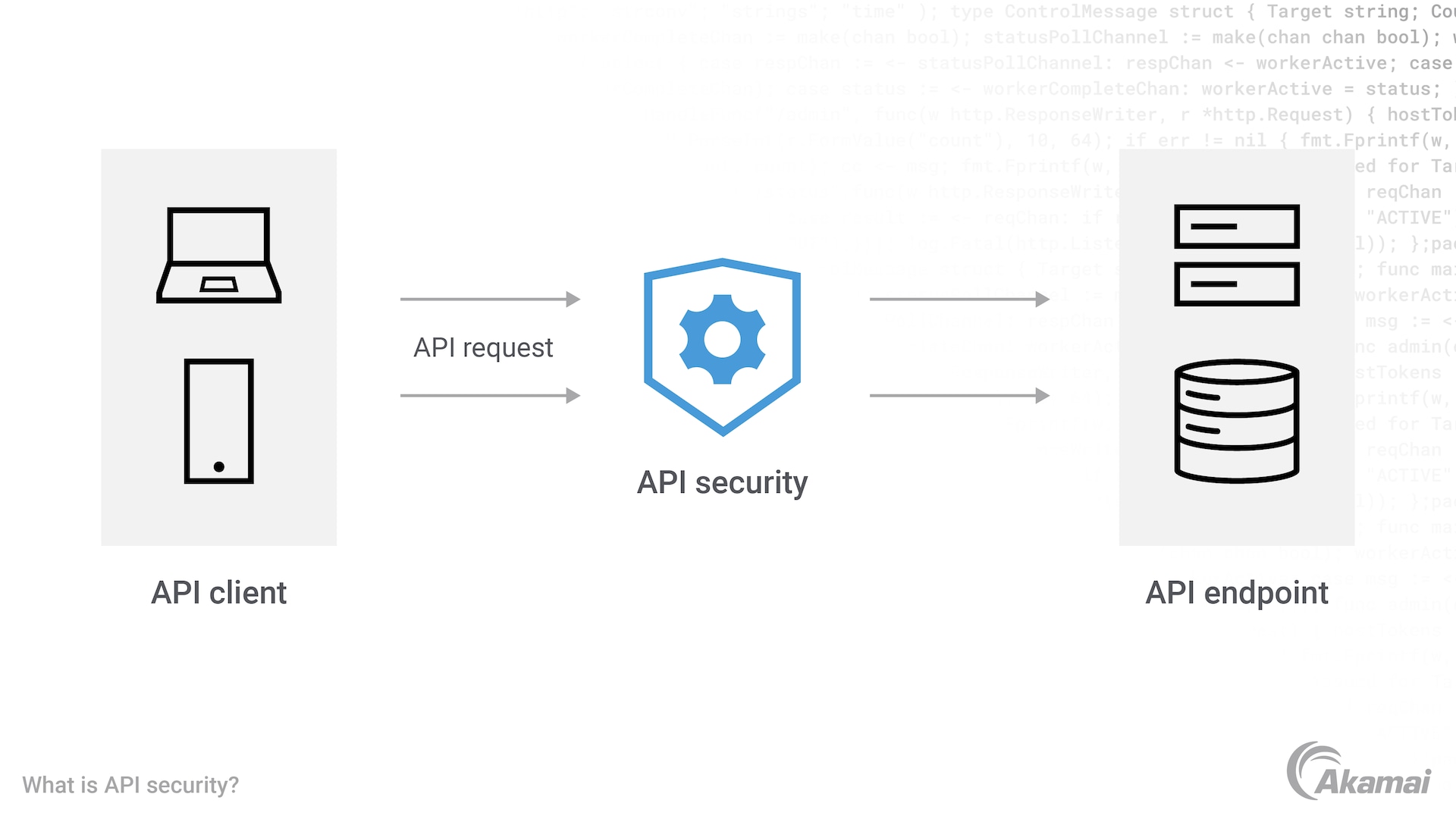
API security is the practice of implementing security controls and protocols to prevent APIs from being successfully attacked. API security begins with gaining visibility into all APIs within an IT ecosystem. Security teams can then protect these APIs with an API gateway, security policy, web application firewall (WAF), user authentication controls, and other technologies that are part of a multi-layered approach to security.
Why customers choose Akamai
Akamai powers and protects life online. Leading companies worldwide choose Akamai to build, deliver, and secure their digital experiences — helping billions of people live, work, and play every day. Akamai Connected Cloud, a massively distributed edge and cloud platform, puts apps and experiences closer to users and keeps threats farther away.

