The most common types of attack vectors include ransomware, compromised weak passwords or credentials, misconfigurations, malware, security vulnerabilities, phishing or pop-ups on web forms, social engineering, malicious insider threats, credit card compromises, weak encryption, uploaded malicious code, unpatched vulnerabilities in operating systems or computer systems, zero-day attacks that result in data breaches or confidential information leaks, and denial-of-service attacks.
Defending against evolving attack vectors
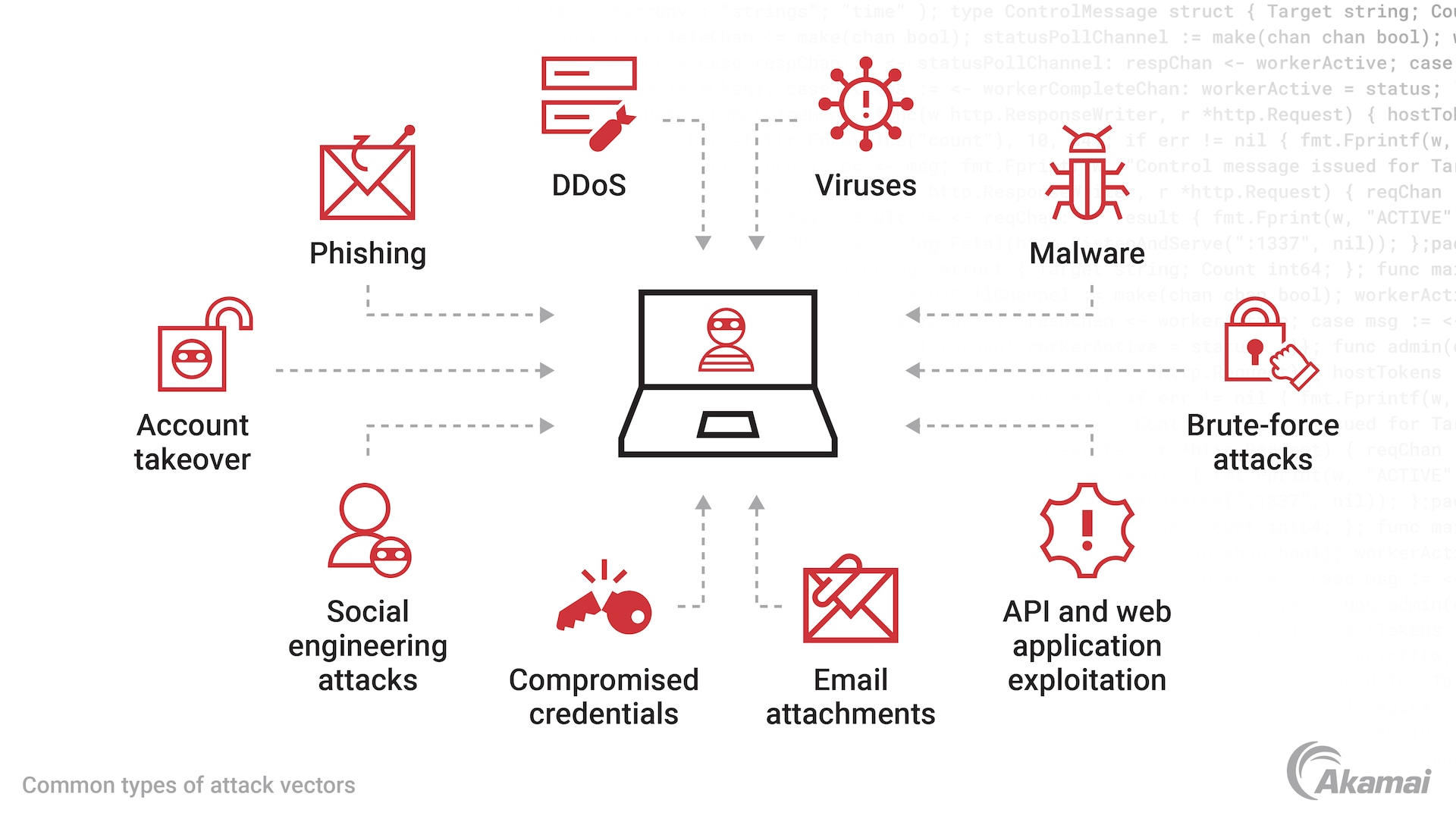
An attack vector is the method that a threat actor uses when trying to gain illegitimate access to an IT system and access sensitive information, usually by exploiting a vulnerability in a network, system, or application. Common attack vectors include email attachments, malware, Trojans or viruses, social engineering attacks, phishing, brute-force attacks, compromised credentials for authentication abuse, account takeover, distributed denial of service, and API and web application exploitation.
Protecting IT systems from rapidly changing attack vectors is a critical challenge for IT security teams. Cybercriminals are constantly adapting new methodologies and finding creative ways to exploit vulnerabilities in applications, as well as weaknesses in cybersecurity defenses caused by inconsistent policies, and sometimes third-party software or service providers missing security incidents. Insider threats and some vectors like ICMP flood are some of the oldest vectors, while new vectors like instant messages are constantly emerging, and familiar vectors are continually evolving.
Akamai can help. Our purpose-built solutions for DDoS protection act as a first line of defense, providing dedicated edge, distributed DNS, and cloud mitigation strategies designed to prevent collateral damage and eliminate single points of failure.
Types of attack vectors
Most denial-of-service attack vectors follow the same basic premise. Use an internet resource or machine, and transfer packets in an effort to degrade performance or render it inaccessible to legitimate users and requests. Using multiple compromised resources across multiple networks of infected computers or bots is a distributed denial-of-service attack. This is accomplished by flooding the system with unwanted traffic or sending requests for resources that eventually cause the target system to grind to a halt.
Volumetric DDoS attacks overwhelm networks with massive amounts of traffic by saturating the bandwidth of the target resource or hindering the ability for a network device to process packets. This unforeseen onslaught of traffic can significantly slow down or prevent access to internal or external internet-facing services. There are a variety of common attack vectors that fall in the volumetric DDoS category, many leveraging reflection and amplification attack techniques.
Domain Name System (DNS) DDoS attacks are a common type of attack vector that cross the line between volumetric and application DDoS. Hackers generate legitimate requests at high rates, or they spoof the IP address of their target to send a large number of requests to open DNS servers, and the reflection of those packets respond to the malicious requests by the spoofed IP address, creating a flood of DNS replies to the intended target. This large volume of traffic inevitably overwhelms the target system and renders it unavailable, preventing legitimate traffic from reaching its intended destination.
Application-layer attacks take advantage of certain vulnerabilities within a specific application, attempting to overwhelm certain functions to make the application unresponsive or unavailable to legitimate users. API endpoints are also vulnerable to application DDoS and payload protections.
DDoS protocol attacks exhaust the compute capacity of network infrastructure resources by sending malicious out-of-state connection requests that take advantage of vulnerabilities in protocol communications. In TCP out-of-state attacks like SYN floods, for example, attackers exploit the TCP protocol by generating a large number of SYN packets per second, per IP address, that initiate a handshake but never complete the connection. This leaves the target device or server waiting for responses and leaves the TCP connections half open. Eventually the server runs out of capacity to accept new connections and can no longer provide service to legitimate requests. Mitigating these attacks usually involves some type of anti-spoofing challenge, as these are commonly spoofed IP addresses.
How Akamai Can Help
Enhance security with Akamai
Akamai’s suite of DDoS protection solutions boosts resilience against complex DDoS threats by providing multiple layers of defense. Akamai’s technology defends against the largest DDoS attacks today, increasing resiliency with 200+ Tbps of network capacity and 100% platform availability. With Akamai, your security team can fine-tune mitigation to your web- and internet-facing services wherever they are hosted, reducing risk across your hybrid environments.
Akamai DDoS protection offers three mitigation solutions that provide holistic, cloud-delivered DDoS defense. The right solution for your organization will depend on the application requirements, use case, and desired time-to-mitigate SLAs.
Prolexic
Akamai Prolexic is purpose-built to stop DDoS attacks in the cloud, before they reach data centers, applications, and internet-facing infrastructure. With Prolexic, network traffic is directed to one of 20 global high-capacity scrubbing centers where the Akamai Security Operations Command Center (SOCC) deploys proactive and/or custom mitigation controls to stop cyberattacks instantly.
App & API Protector
Akamai App & API Protector provides one-stop, zero-compromise security for websites, applications, and APIs. Built for ease of use, App & API Protector offers some of the most advanced security automation available today. A new adaptive security engine powers many industry-leading core technologies for web application firewall, bot mitigation, API security, and DDoS protection.
Edge DNS
Akamai Edge DNS is a cloud-based solution that delivers 24/7 DNS availability while improving DNS responsiveness and delivering the resilience required to defend against the largest DDoS attacks. Edge DNS leverages Akamai Connected Cloud, with thousands of DNS servers in more than 1,000 points of presence worldwide providing a high level of DNS service availability.
Benefits of Akamai security solutions
When defending against the latest attack vectors with Akamai DDoS protection and other security solutions, organizations can:
Reduce DDoS risk with proactive mitigation controls that stop more than 80% of attacks instantly and that block highly complex, record-breaking attacks without sacrificing quality of mitigation.
Ensure business continuity with optimized incident response, custom runbooks, service validation exercises, and operational readiness drills.
Protect websites, applications, and APIs from a broad range of cyberattack vectors.
Maximize security investment with a solution that includes API protections, bot visibility and mitigation, DDoS protection, SIEM connectors, web optimization, API acceleration, cloud computing, and more.
Simplify maintenance through automated updates and self-tuning capabilities designed to reduce operational friction and administrative overhead.
Reduce the API attack surface by automatically discovering and protecting APIs from vulnerabilities, including the OWASP API Security Top 10.
Guarantee 24/7 DNS availability by leveraging Akamai’s scalable, globally distributed platform.
Achieve faster, more reliable DNS resolution with zone apex mapping and thousands of servers worldwide.
Frequently Asked Questions (FAQ)
An attack vector is the path or method that a cybercriminal uses when attempting to gain illegitimate access to an IT system. Most attack vectors attempt to exploit a vulnerability in a system or application. When successful, attackers can breach the defenses protecting an IT system to steal sensitive data, credentials, money, or intellectual property, or to disrupt the business by making IT resources unavailable.
An attack vector is the method a cybercriminal uses to gain unauthorized access. An attack surface is a set of points on the boundary of a system, a system element, or an environment where an attacker can try to enter, cause an effect on, or extract data from that system, system element, or environment.
Why customers choose Akamai
Akamai powers and protects life online. Leading companies worldwide choose Akamai to build, deliver, and secure their digital experiences — helping billions of people live, work, and play every day. Akamai Connected Cloud, a massively distributed edge and cloud platform, puts apps and experiences closer to users and keeps threats farther away.