A botnet is a collection of thousands or millions of malware-infected computers or devices functioning as individual bots that are directed to perform a variety of cyberattacks. Botnets are controlled by a command and control (C2) server and are often involved in large-scale DDoS attacks, illicit cryptomining, and credential stuffing attacks.
Bot or botnet traffic is traffic generated by automated computer programs, commonly known as bots. These bots are used to send automated traffic to websites, often to manipulate search engine rankings or perform other malicious activities. Botnets are networks of computers that are used to carry out large-scale attacks, such as distributed denial-of-service (DDoS) attacks.
Botnet traffic, even from good bots, brings challenges
Bot traffic continues to confound organizations large and small. Bots, or botnets (groups of bots networked together to act toward one purpose), are becoming an ever larger portion of traffic for many web properties. For example, bad botnets can send hundreds of thousands of requests to websites and mobile apps in very short periods of time. Sometimes this traffic is from bots acting maliciously, from targeting software vulnerabilities to conducting DDoS and brute-force attacks, and other abusive behaviors.
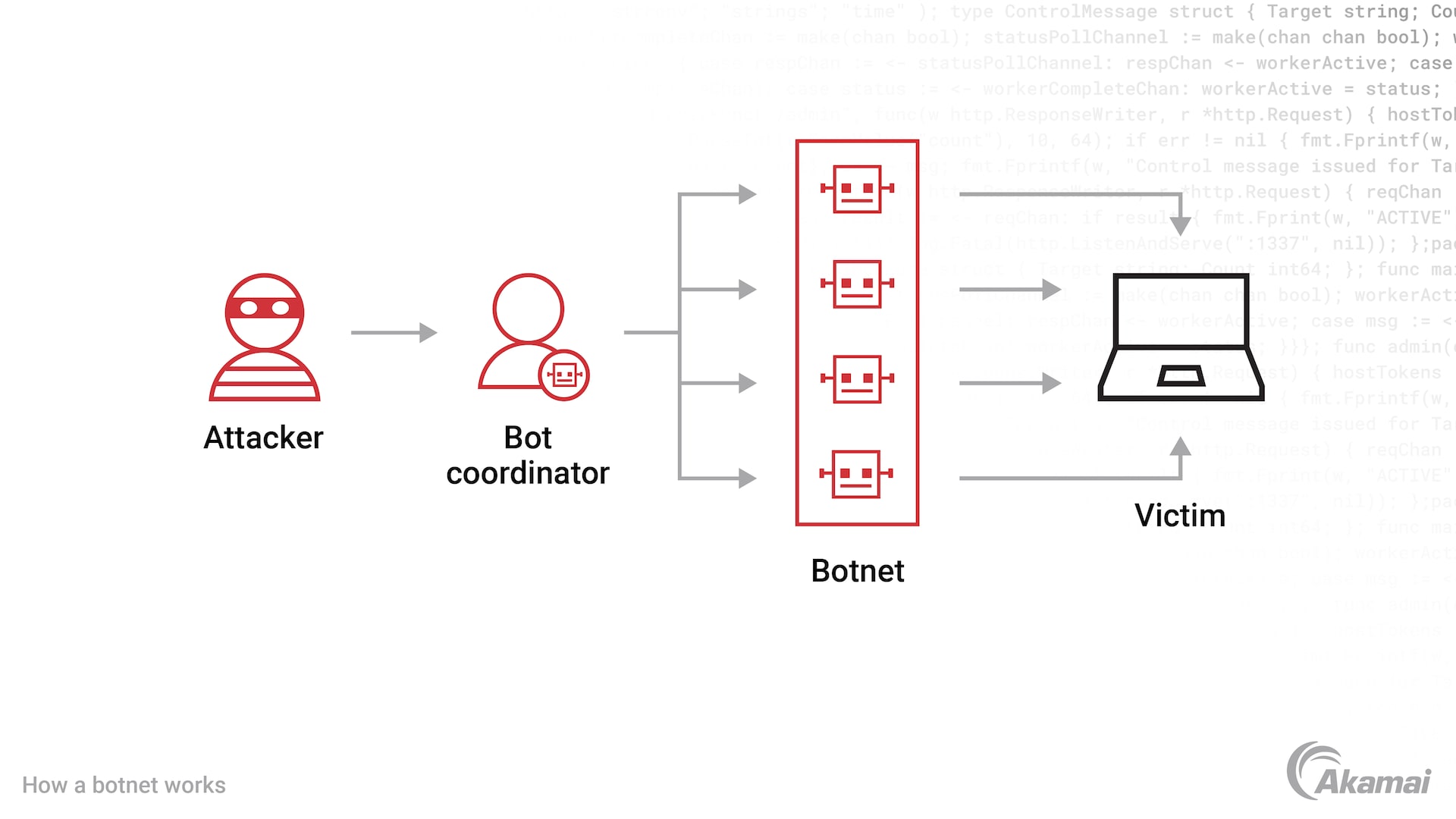
A great deal of malicious botnet traffic today is dedicated to credential stuffing, where attackers attempt to gain unauthorized access to user or customer accounts using stolen credentials. A botnet with an army of hijacked or infected computers can attempt hundreds of thousands of login attempts per hour, using username and password combinations that are known to be valid on other sites. Since many individuals reuse passwords across websites, attackers are frequently successful in using botnet traffic to gain access to IT environments, taking over accounts to steal money and data, and commit other types of fraud.
Mitigating botnet traffic is difficult, as initiating multiple login requests doesn’t result in patterns that can be easily identified and blocked. Fortunately, Akamai offers several bot security solutions that can effectively detect and mitigate bots and botnet traffic while ensuring no compromise on performance for legitimate users.
The role of botnet traffic in credential stuffing
Credential stuffing attacks are big business for cybercriminals. Login credentials that have been exposed in a data breach are easily available for purchase on the dark web. Botnets make it easy for a criminal to use thousands of credentials on thousands of websites thousands of times per day, eventually striking gold by successfully accessing the site.
Once a username and password have been proven valid on a specific site or web app, attackers can log in to take over the account — or sell the credentials to other cybercriminals — in order to make purchases, transfer money, steal data, or launch larger cyberattacks from within the IT environment.
Defending against credential stuffing requires bot mitigation detection techniques that can accurately recognize malicious traffic and block botnet activity — without false positives that inadvertently block legitimate users as well. The challenge is that login requests in a credential stuffing attack can be difficult to recognize, since the verified credentials represent valid requests.
As anti-bot technology has become more effective, bot operators have become quite adept at evolving their botnet attacks to evade detection. To protect an organization, security teams need botnet detection systems that can adapt as quickly as attackers. That’s where Akamai can help.
Stop botnets with Akamai Account Protector
Akamai Account Protector provides protection from botnet traffic as well as fraudulent login attempts. This Akamai technology is designed to detect imposters and stop bots at the edge while allowing customers to get through without encountering additional friction.
Account Protector employs a variety of techniques to learn the behavior of legitimate account owners, such as the types of devices they tend to use, as well as typical IP addresses, networks, locations, and frequency and time of logins. After developing profiles of individuals and user populations, Account Protector examines each new authentication request for any variation from normal behavior, searching for anomalies that may be signs of fraud or credential stuffing. When a request is deemed suspicious or illegitimate, Account Protector automatically applies the appropriate response in real time, without affecting the experience of real customers or account owners.
Key capabilities include:
- Real-time user session risk scoring. Account Protector evaluates risk and trust signals during authentication in real time to assess the risk that the request isn’t coming from a legitimate account user.
- Profiles. Account Protector constructs a behavioral user profile for individuals, and aggregates these into a population profile where variances in behavior can be compared to the entire population of users for better anomaly detection.
- Source reputation. This feature evaluates the reputation of sources based on past malicious activity observed across all Akamai customers, including many of the world’s largest, most heavily trafficked websites.
- Known-bot directories. Akamai’s directory of 1,750+ known bots enables fast and appropriate responses to bot and botnet traffic.
- Sophisticated bot detections. Using a variety of AI and machine learning models and techniques, Akamai detects unknown bots from the first interaction.
- Analytics and reporting. Akamai Account Protector can analyze activity on individual endpoints, investigate a specific user, or review users by risk level. High-level statistics and detailed analyses can be imported into security information and event management (SIEM) tools for improved detection of fraud.
Control bot traffic with Akamai Bot Manager
Akamai provides additional protection against botnet traffic in Bot Manager, a bot management solution with unmatched detection and mitigation capabilities. Using multiple patented technologies, Bot Manager detects and mitigates bots where they make initial contact, rather than allowing them to reach websites first. Information from Akamai’s threat intelligence researchers is automatically incorporated into Bot Manager’s detections and analytics.
Bot Manager learns to detect botnet traffic by gathering data on “clean traffic” across a wide distribution of data types. By observing clean data on network traffic patterns, traffic types, and traffic volume, Bot Manager holistically combines detection triggers to give every request a Bot Score. High scores indicate that a request is generated by a bot and should be mitigated. Low scores suggest the request is from a human and can be watched or monitored. Requests in the “gray area” in the middle can be challenged with innovative challenges that slow sophisticated bot attacks to a crawl while driving up the costs for attackers.
Frequently Asked Questions (FAQ)
Bot or botnet traffic is traffic generated by automated computer programs, commonly known as bots. These bots are used to send automated traffic to websites, often to manipulate search engine rankings or perform other malicious activities. Botnets are networks of computers that are used to carry out large-scale attacks, such as distributed denial-of-service (DDoS) attacks.
A bot is a computer program that is designed to operate independently, performing a set of specific tasks. Often, these activities are highly repetitive and can be performed by bots much faster and more accurately than by humans. Bots can be extremely helpful — spider bots, for example, crawl websites to index content, making them easier for search engines to find. Other bots can be malicious, such as bots that harvest email addresses for spammers or bots that artificially drive up traffic metrics on websites or followers on social media. Organizations rely on bot management solutions to distinguish between good and bad bots, enhancing web and network security without slowing productivity and business operations.
A brute-force attack is a type of cybercrime where attackers use trial and error to crack passwords, credentials, and encryption keys. Many brute-force attacks use botnets or malicious software to try thousands of username/password combinations in an effort to gain unauthorized access to an account or IT system.
Why customers choose Akamai
Akamai powers and protects life online. Leading companies worldwide choose Akamai to build, deliver, and secure their digital experiences — helping billions of people live, work, and play every day. Akamai Connected Cloud, a massively distributed edge and cloud platform, puts apps and experiences closer to users and keeps threats farther away.

