Credential stuffing is a brute-force attack using valid credentials that have been exposed in a data breach or on the dark web. Since many users reuse the same username and password, attackers can often use credential stuffing to gain unauthorized access to user accounts on other sites.
Defending against brute-force attacks
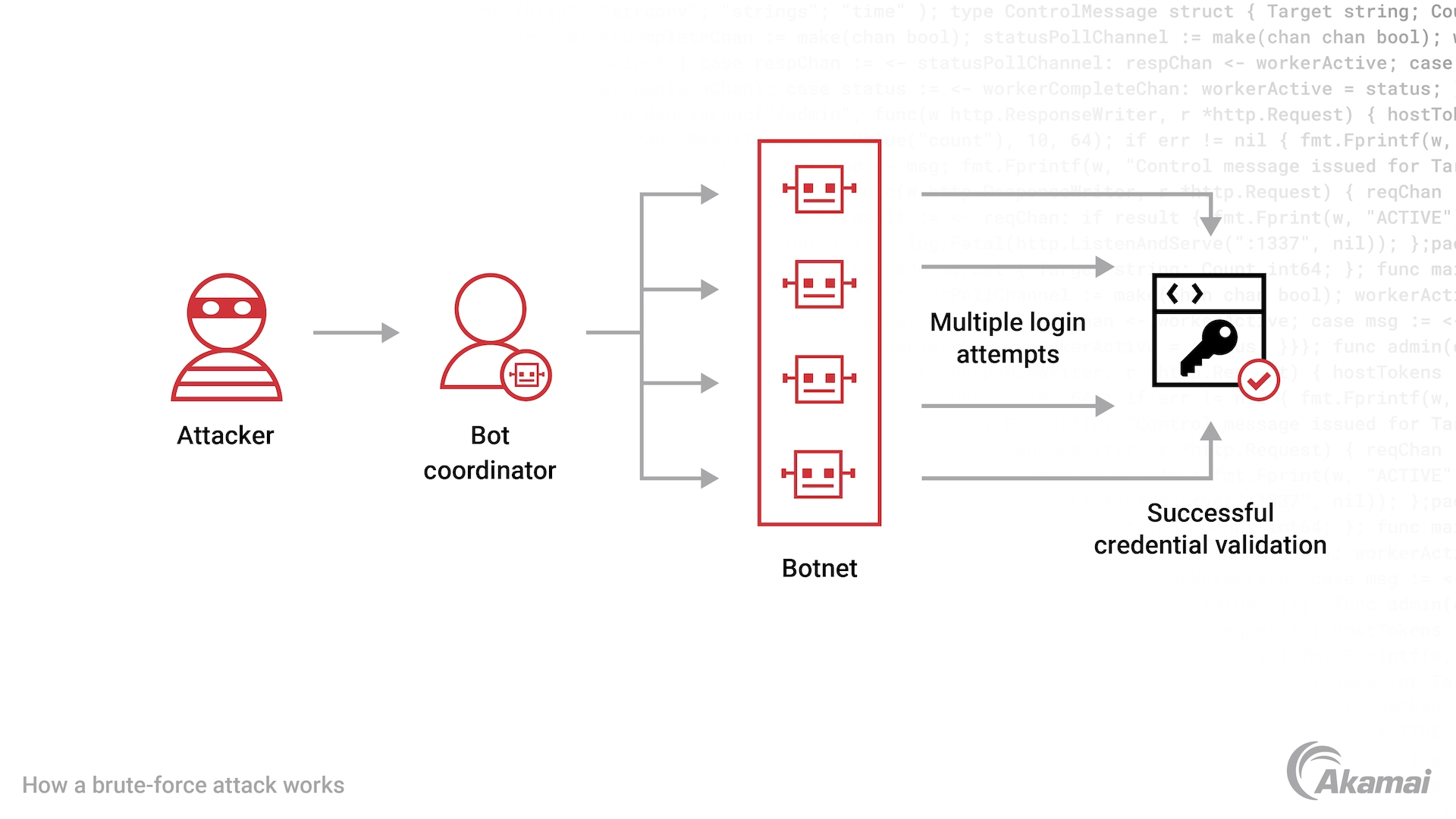
In the field of cyberthreats, brute-force attacks remain a popular and profitable attack method for cybercriminals. In these attacks, threat actors attempt to access user accounts by entering a large number of username and password combinations into login pages on websites or web applications. Since they are often carried out by botnets that can make hundreds of thousands of trial-and-error login attempts per hour, brute-force attacks have a high degree of success.
It’s critical to block these attacks before they gain access to user accounts and personal data. Once inside an account, brute-force attacks are much more difficult to stop. The right bot detection solutions must be able to differentiate between legitimate bot traffic from malicious bots, while also tracking bots and botnets (short for “robot networks”) as they rapidly evolve in an attempt to evade detection.
As the world’s most distributed computing platform, Akamai offers superior bot security technology with intelligence gleaned from 11.5 billion bot requests and 280 million bot logins daily. With Akamai anti-bot security solutions, cybersecurity teams can effectively block brute-force attacks without slowing down performance or impacting the online experience for legitimate users.
The anatomy of a brute-force attack
In a brute-force attack, hackers use numerous username/password combinations to gain access to a user account or an IT environment. Nearly all brute-force password attacks today are performed by programs called bots, which can repeatedly perform specific tasks on their own without human intervention. Many of these password-cracking attacks are carried out by botnets, which is a network of bots comprising hundreds or thousands of computers infected with malware, which allows them to be controlled by a single attacker.
Common types of brute-force attacks include:
- Simple brute-force attacks. This form of attack uses standard password combinations or personal identification numbers. Simple attacks are often successful because so many users don’t use a password manager and still rely on weak passwords with common words that can be easily guessed.
- Dictionary attacks. Attackers start with an individual username and test possible passwords drawn from dictionaries, amending words with special characters and numbers.
- Hybrid brute-force attacks. This format uses external logic to determine password variations and possible combinations that are most likely to be successful, then tries as many variations as possible.
- Reverse brute-force attacks. In this approach, attackers use a collection of common passwords against many possible usernames.
- Credential stuffing. Attackers use known passwords acquired from data breaches to attempt to log in to a variety of other sites. This approach is successful even when users have complex passwords because many individuals reuse the same credentials across a wide range of accounts.
Blocking brute-force attacks requires technology that can quickly detect and mitigate malicious traffic from bots and botnets. Yet because so much web traffic today originates from good bots as well as bad, superior solutions must be able to distinguish and block bots with few or no false positives. That’s where Akamai technology excels.
Stop brute-force attacks with Akamai Bot Manager
Akamai Bot Manager provides the visibility and control that security teams need to protect against brute-force attacks and many other bot-related threats. Bot Manager features unmatched detection and mitigation capabilities that effectively stop bad bots and botnets while enabling legitimate bot-related activity to operate effectively and safely.
Using multiple patented technologies to detect and mitigate bots, Akamai Bot Manager stops bots where they make initial contact instead of allowing them to reach a site first. Detection engines are continually updated with threat intelligence produced by Akamai’s security research teams, which analyze hundreds of terabytes of attack data daily.
To distinguish malicious from legitimate bot traffic, Bot Manager collects data on “clean traffic” across a wide distribution of data types and in large volumes of traffic on Akamai Connected Cloud. Our platform protects some of the largest and highest-profile companies in the world — which are often the targets of the most advanced bot operators. When a new bot is detected at one customer, the data is added to a known bot library and informs the algorithms for all customers.
Bot Manager uses a scoring model to calculate the likelihood that any request is coming from a bot vs. a human being. High-scoring requests (definitely a bot) can be aggressively mitigated, while low-scoring requests (likely a human) can be watched and monitored. For scores in the “gray area,” Bot Manager issues cutting-edge challenges that can slow attacks and drive up costs for bot operators.
Benefits of Akamai bot management technology
With Akamai Bot Manager, security teams can:
- Protect organizations, users, and IT environments from the impact of brute-force attacks
- Easily distinguish legitimate bot traffic from malicious attacks
- Build customer and partner trust with protection from fraudulent activity
- Reduce the burden of remediating the fallout of bot attacks such as replacing stolen accounts, checking for compromised accounts, and managing user complaints
- Enhance operational control to reduce business and financial risks, while controlling IT spend and strategically managing partner bots
- Improve decision-making with data-driven analysis and reporting that allows IT administrators to make creative and effective choices about security posture, risk tolerance, and IT operations across their network security
Frequently Asked Questions (FAQ)
A brute-force attack is a cyberthreat in which attackers attempt to gain access to an account or an IT environment by injecting many username and password combinations until a valid pair is discovered. Brute-force attacks are usually carried out by botnets that can make hundreds of thousands of login attempts per hour, reducing the amount of time it takes to access an account.
To combat brute-force attacks, security teams can deploy bot management technology, two-factor authentication, or multi-factor authentication solutions, and encourage users to adopt strong passwords. Unique passwords are often longer passwords with a mix of lowercase and uppercase letters as well as numbers and symbols. Password length impacts the amount of time it takes for bots and botnets to guess your password.
A bot is a computer program that is designed to perform specific tasks without supervision from a human being. Many bots perform helpful activities such as searching the internet for the lowest prices or gathering knowledge from a variety of sources. Some bots perform malicious or illicit activity — spambots, for example, collect email addresses from websites that spammers can use to send unwanted messages. Traffic bots create artificial traffic on websites or social media accounts to drive up certain metrics. Bots can also carry out cyberattacks as part of a large network — a botnet, where multiple devices are controlled by a single attacker. Attackers may even make bots available as part of a botnet service, carrying out attacks on behalf of a third party for a fee.
Why customers choose Akamai
Akamai powers and protects life online. Leading companies worldwide choose Akamai to build, deliver, and secure their digital experiences — helping billions of people live, work, and play every day. Akamai Connected Cloud, a massively distributed edge and cloud platform, puts apps and experiences closer to users and keeps threats farther away.