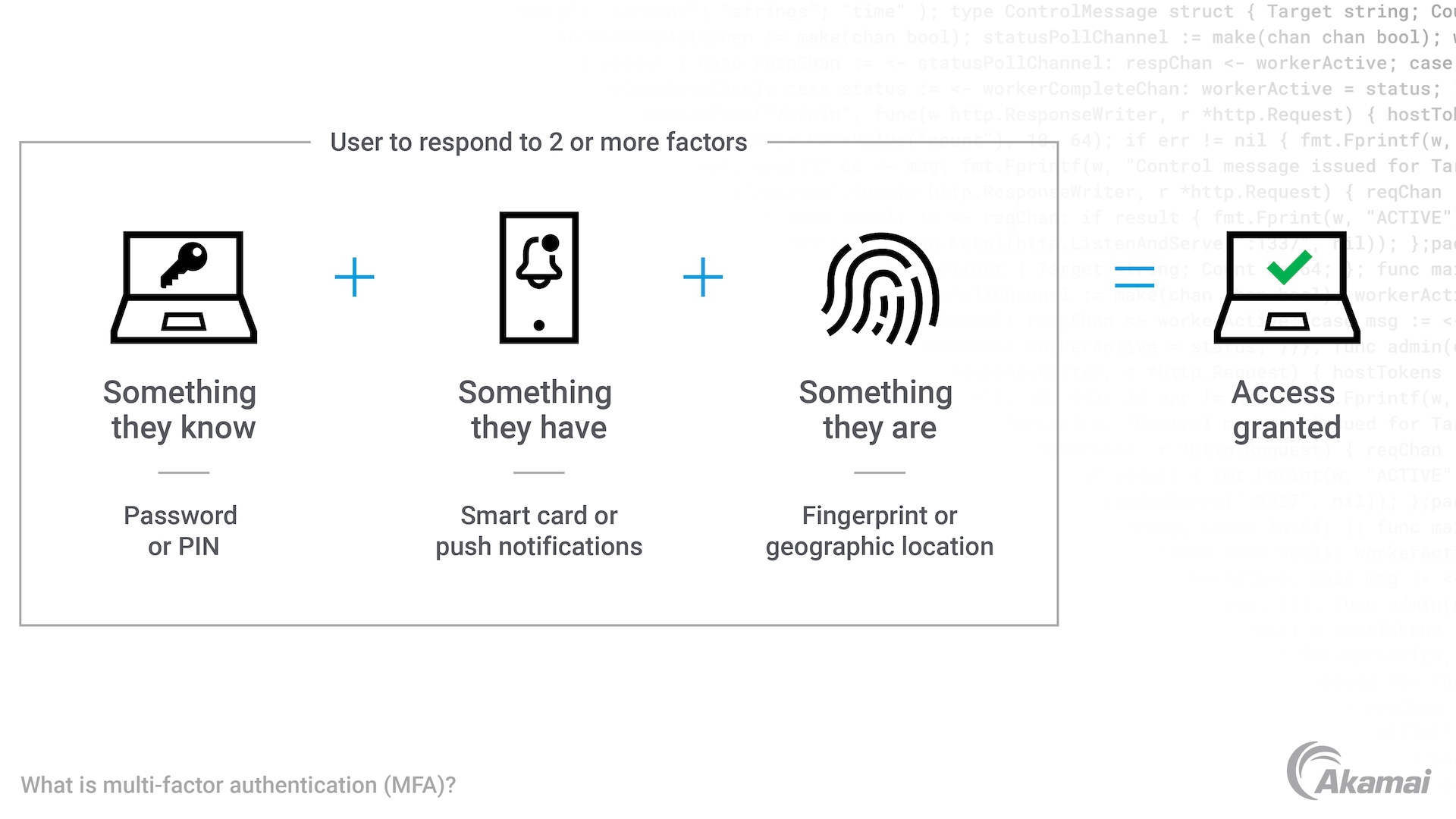
Multi-factor authentication (MFA) is a powerful identity and access management (IAM) tool for protecting cloud services and other applications from data breaches. An MFA solution requires users to authenticate using two or more verification methods. These include something they know, such as a passcode; something they have, such as a push notification or one-time password; and something they are, such as facial recognition.
Protect applications with a cloud MFA solution
As organizations seek to provide employees with access to applications and services in the cloud, multi-factor authentication (MFA) has become a critical tool to configure and optimize for preventing users’ identity breaches and strengthening security posture.
By requiring a second factor or form of authentication to access cloud services, MFA solutions represent a significant improvement over authentication that relies solely on usernames and passwords. Yet sophisticated and persistent cybercriminals can easily hack MFA technology using phishing techniques and social engineering to steal credentials. Cloud MFA solutions built on the FIDO2 security standard offer greater protection, but because they also typically require physical security keys, they can be costly and complex to manage and are not easy for employees to use.
Akamai offers a better approach to two-factor authentication — a next-generation, phish-proof solution based on FIDO2 that couples proven security with the familiar and frictionless user experience of a mobile push, eliminating the need for cumbersome hardware security keys.
How cloud MFA works
Along with a username and password, MFA security requires a second or third form of proof of identity when a user seeks to access applications and services in the cloud. These additional factors may be something the employee knows, such as a PIN; a token-based authenticator, such as a smart card or key fob; or a one-time password, push notification, or SMS code delivered to a mobile app. Alternatively, the additional factor could be biometric authentication, such as a fingerprint or facial recognition.
Implementing cloud MFA technology can substantially decrease the risk of unauthorized access. Organizations that rely on MFA solutions are significantly less likely to be compromised than those that do not. Yet standard cloud MFA solutions can be bypassed using techniques such as phishing, credential stuffing, social engineering, and verification code interception via email or SMS.
The most secure form of MFA technology uses FIDO2, the strongest standards-based authentication method available. These solutions effectively eliminate the risk of phishing, machine-in-the-middle attacks, social engineering, and other attacks. In the past, the only way to enable cloud MFA using FIDO2 was by purchasing physical FIDO2 security keys for every user. This represented a significant increase in the cost of deploying MFA technology as well as the complexity of distributing, configuring, managing, and replacing keys.
To provide an easier cloud MFA solution, Akamai has engineered the first-of-its-kind cloud infrastructure MFA technology to deliver superior security as well as a frictionless experience for employees.
Cloud MFA technology from Akamai
Akamai MFA is a multi-factor authentication service that provides strong secondary authentication for cloud apps as well as on-premises, web-based, SaaS, and IaaS applications.
Our cloud MFA service leverages FIDO2 standards via a smartphone app rather than with physical security keys. Security is ensured through end-to-end cryptography and a sealed challenge/response flow that makes the authentication process impervious to hacks via phishing and social engineering. This next-generation technology is coupled with the familiar and frictionless user experience of a mobile push, simplifying superior authentication technology and increasing user adoption rates.
Authenticating a user with cloud MFA technology from Akamai is accomplished in six simple steps:
- The user enters a username and password to the login prompt.
- Once these credentials are validated, the primary authenticator connects to Akamai MFA to generate the second authentication factor.
- Akamai MFA renders a page that allows the user to select the factor used for authentication. The available factors, including the FIDO2 phish-proof push, will have been configured by the enterprise security team.
- Akamai MFA sends a push notification to the user’s smartphone app.
- When the user accepts the push notification, Akamai MFA returns control to the primary authenticator.
- The primary authenticator then proceeds to provide access for the user account for the requested application or service.
Benefits of MFA with Akamai
Our cloud MFA technology is deployed on Akamai Connected Cloud and managed centrally through the unified, customizable Akamai Control Center. With configurable authentication factors, automated provisioning, and authentication event reporting, Akamai MFA enables security teams to achieve significant objectives.
Mitigate risk. Deploying a cloud MFA solution from Akamai eliminates the impact of phishing and social engineering attacks on the authentication process.
Accelerate deployment. With Akamai, there are no delays related to the need to distribute physical security keys or issue compatible hardware. Akamai MFA can be quickly implemented via an app on existing smartphones.
Reduce the total cost of ownership. By digitizing FIDO2 security with an existing smartphone and web browser, Akamai MFA enables security teams to avoid the need to purchase, replace, and maintain additional hardware.
Delight users. Our cloud technology lets users authenticate with their own smartphone and familiar push notifications.
Zero Trust support. Organizations rely on cloud interface technology from Akamai to support their efforts at creating a Zero Trust security network.
Future-proof authentication investments. With a solution that is delivered in the cloud and based on the FIDO2 standard, Akamai is built to support future use cases such as passwordless authentication.
Frequently Asked Questions (FAQ)
By enabling multi-factor authentication, organizations can prevent data breaches that can occur when hackers steal a user’s credentials. By requiring users to sign in with more than just a username and password, MFA makes it much more difficult for hackers to gain access to sensitive data.
Sophisticated hackers can bypass standard cloud MFA solutions using phishing and social engineering techniques. MFA solutions based on the FIDO2 standard offer a more secure authentication technology.
Why customers choose Akamai
Akamai powers and protects life online. Leading companies worldwide choose Akamai to build, deliver, and secure their digital experiences — helping billions of people live, work, and play every day. Akamai Connected Cloud, a massively distributed edge and cloud platform, puts apps and experiences closer to users and keeps threats farther away.