Multi-factor authentication (MFA) — also known as two-factor authentication — is a technology that adds additional security to the login process. MFA services require users to present two or more “factors” to prove their identity. MFA authentication factors may include something the user knows, like a PIN; something they are, like a fingerprint scan; or something they have, like a push notification. MFA technology plays an important role in remote work security and in the transition to Zero Trust networking and the SASE security framework.
The dangers of credential stuffing
Credential stuffing is a lucrative activity for cybercriminals — and a potentially costly event for enterprises. According to Ponemon Institute, the cost associated with credential stuffing attacks can range from $6 million to $54 million annually, realized through fraud-related losses, application downtime, and customer churn.
Credential stuffing is an automated cyberattack where hackers use bots to continually attempt to access a website with credentials purchased from the dark web. These attacks are often successful because individuals tend to reuse passwords across multiple accounts. When attackers discover a set of credentials that work, they may use them to illegitimately access a company’s network, or sell the validated credentials to other criminals who can use them to commit data theft, account takeover (ATO), and other fraudulent activity.
Unfortunately, it’s hard to stop credential stuffing attacks as they do not have a pattern that makes them easy to identify and block. Because these types of attacks are typically automated, a bot management technology is often the best defense.
Credential abuse happens when malicious bots steal your users’ login information. Find out how it starts, and how to protect your users, brand, and revenue.
Akamai Bot Manager provides the visibility and control you need to safeguard your business from credential stuffing attacks. Bot Manager uses multiple patented technologies to detect and mitigate bots when they make initial contact — rather than allowing them to reach your site first.
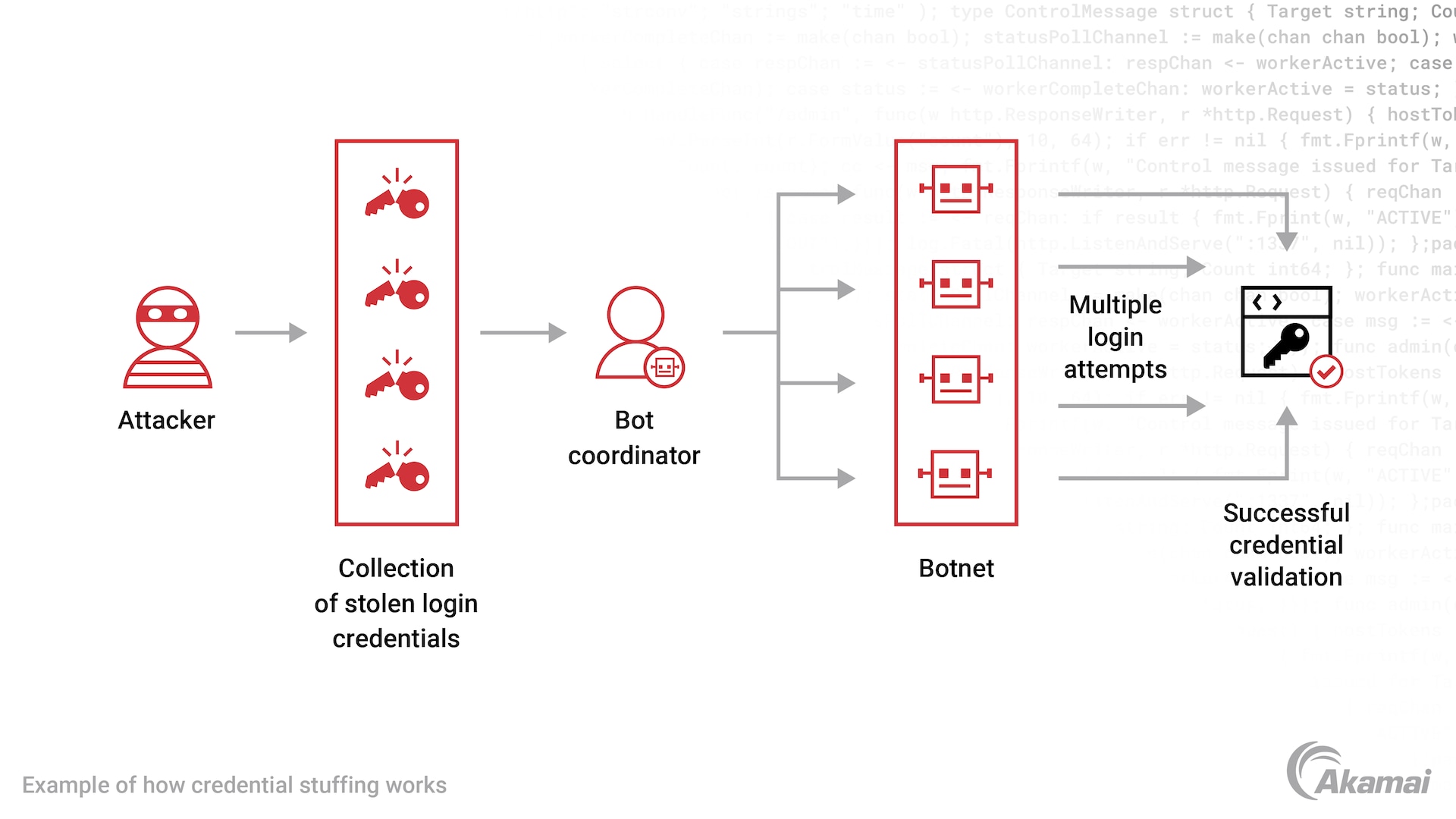
How credential stuffing works
With credential stuffing, attackers take advantage of poor password hygiene to gain access to a company’s network, applications, or services. The most likely targets are popular websites with high brand reputation, where user credentials leaked from data breaches are available on the dark web. Armed with a list of stolen username and password combinations, attackers repeatedly attempt to log into a site with stolen credentials. When they are successful, they may take over the account for financial gain or sell the validated credentials on the dark web to other criminals.
Credential stuffing attacks typically rely on bots or automated tools to repeatedly attempt to access the site with compromised credentials. When hackers use a single bot to make repeated login attempts from a single IP address, the attack is fairly easy to identify and block with standard IP traffic management tools. But when login attempts come from hundreds or thousands of different IP addresses — as is the case with automated tools or a botnet — the attack can be far more difficult to stop.
Credential stuffing is notoriously difficult to detect. Attackers frequently change methods they use to bypass defenses and impersonate authorized customers. It’s hard for companies to distinguish between a credential stuffing attack and a customer who simply mistypes a password or uses the wrong credentials. False positives with credential stuffing solutions are a big concern, and no company wants to face the ire of frustrated customers who are mistakenly shut out of their accounts.
One of the most successful strategies for preventing credential stuffing is customer education plus a bot management solution that combines advanced behavior anomaly analysis and behavioral telemetry with machine learning. That’s where Akamai Bot Manager can help.
Read the Akamai blog: Enemy at the Gates: Analyzing Attacks on Financial Services
Akamai Bot Manager
Akamai Bot Manager uses multiple patented technologies to detect and mitigate bots at first contact. Bot Manager views traffic at the edge, where users first connect to an application, and where Bot Manager can access clean data on traffic patterns, traffic types, and traffic volume. Viewing an average of 1.5 billion bot requests and 280 million bot logins per day, Bot Manager uses machine learning algorithms to understand what “clean traffic” looks like and to distinguish good bots from bad. By automatically incorporating insight from Akamai’s threat intelligence researchers, Bot Manager issues a Bot Score that combines all the detection triggers to identify sophisticated bots and get a more accurate assessment of each request.
With Akamai Bot Manager, your company can:
- Mitigate credential stuffing attacks. Understand which interactions are legitimate, protecting your company from fraudulent activity while building trust with consumers and partners.
- Minimize the burden of remediation. Reduce financial and staff resources required to constantly check for compromised accounts, replace stolen accounts, and address user complaints after a bot attack.
- Improve decision-making. Detailed analytics and reporting enable your IT teams to make better, data-driven decisions about customer journeys, security posture, risk tolerance, and IT operations.
Read the Akamai blog: Credential Stuffing and Account Takeover—The Business View
Key features of Akamai Bot Manager
Akamai Bot Manager includes sophisticated and innovative capabilities for preventing credential stuffing attacks and other dangerous bot activity.
- Known-bot directories enable Bot Manager to automatically respond appropriately to known bots, both good and bad.
- Dynamic bot detection uses AI and machine learning models and techniques to detect unknown bots at first interaction. These include user behavior analysis, automated browser detection, HTTP anomaly detection, browser fingerprinting, high request rates, and more.
- A Bot Score model automatically scores each request, calculating the likelihood that a request is coming from a bot.
- Custom settings for endpoints provide the flexibility to set strategic responses differently for each endpoint. A response tuning simulator adjusts strategic responses based on endpoint and risk tolerance.
- Auto-tuning capabilities reduce the need for human intervention as bots evolve.
- Nuanced response actions enhance bot mitigation with options such as serve alternate content, serve challenge, and more.
Frequently Asked Questions (FAQ)
Credential stuffing is an attempt to fraudulently gain unauthorized access to a user account by automatically injecting stolen usernames and password pairs into a website login form.
Brute-force attacks attempt to guess passwords with no context or clues, using characters at random. Credential stuffing uses exposed data, dramatically reducing the number of possible correct answers.
Why customers choose Akamai
Akamai powers and protects life online. Leading companies worldwide choose Akamai to build, deliver, and secure their digital experiences — helping billions of people live, work, and play every day. Akamai Connected Cloud, a massively distributed edge and cloud platform, puts apps and experiences closer to users and keeps threats farther away.