Akamai powers and protects life online. Leading companies worldwide choose Akamai to build, deliver, and secure their digital experiences — helping billions of people live, work, and play every day. Akamai Connected Cloud, a massively distributed edge and cloud platform, puts apps and experiences closer to users and keeps threats farther away.
Cybersecurity is the practice of protecting IT (information technology) networks, systems, data, applications, and devices from attacks. Cyberattacks are typically designed to disrupt business operations, gain unauthorized access to systems, take data or intellectual property, or steal or extort money from organizations. Strong cybersecurity requires a multilayered defense involving technologies, processes, policy, and security expertise to protect organizations from attacks that can result in loss of business and reputation.
What is a cybersecurity program designed to do?
Effective cybersecurity programs are designed to identify threats and remediate them as quickly as possible. Cybersecurity technologies may be designed to stop threats before entering a network or to recognize and stop attacks in progress. Because of the sheer volume and increasing sophistication of cyberattacks, many cybersecurity programs are focused both on stopping attacks as well as ensuring business continuity during attacks that successfully breach initial defenses.
Why is cybersecurity important?
IT systems’ networks, applications, and data are critical to operations in every organization. As the business world becomes more interconnected, these resources become more valuable to cybercriminals and more vulnerable to cybercrime, data breaches, and attack. A strong cybersecurity program helps organizations prevent loss of data (data protection), damage to reputation, and a negative impact on the bottom line.
What is a cybersecurity threat?
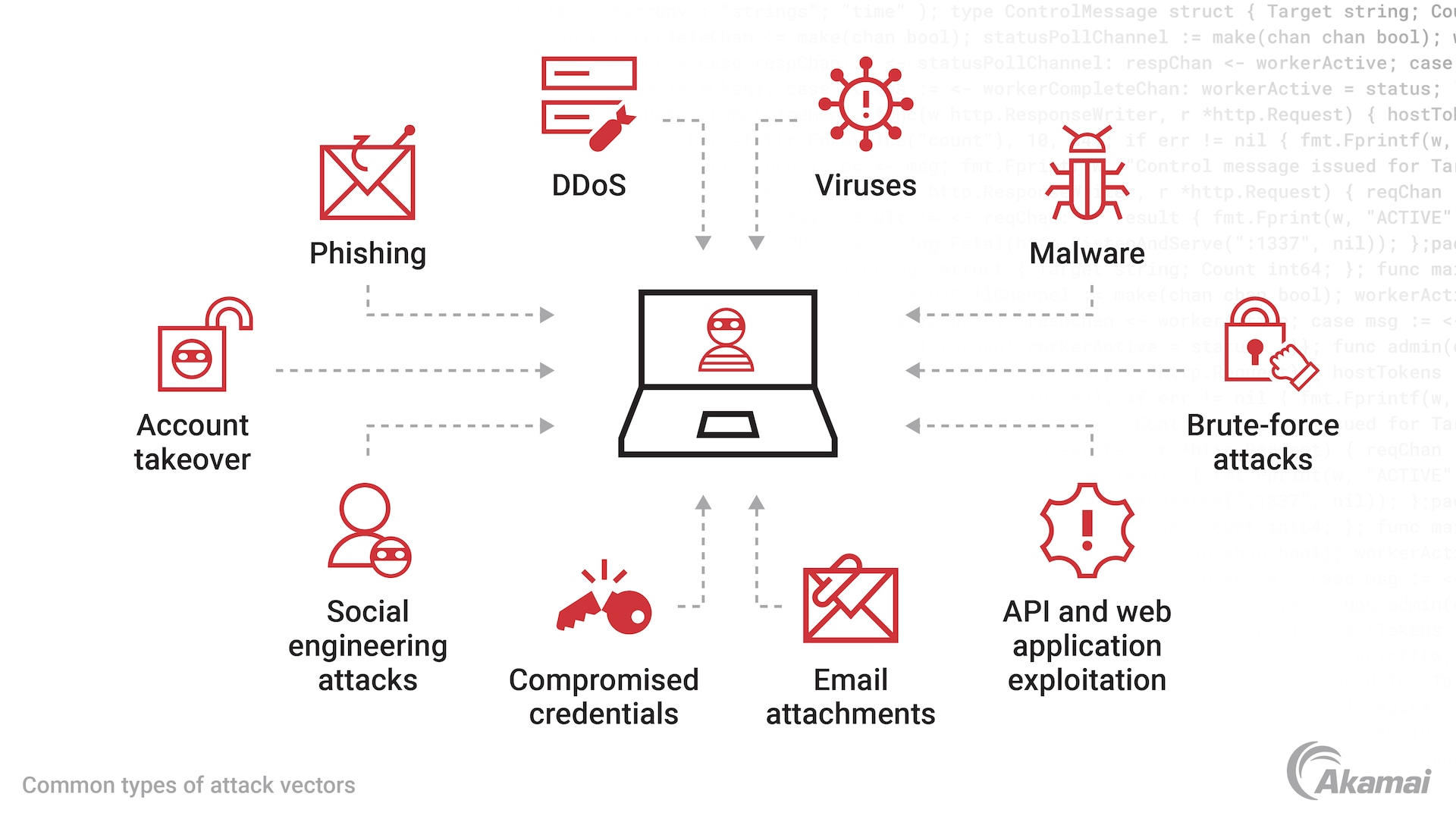
While the threat landscape is constantly evolving, there are categories of common cyberattack methods that continue to present a challenge for cybersecurity programs.
Malware is malicious software — such as viruses, worms, or spyware — that is designed to steal data or damage networks and systems.
Ransomware attacks use a form of malware that encrypts files within a target network, allowing cybercriminals to extract a ransom before providing an encryption key that restores access to important data.
Phishing attacks use fraudulent email or text messages that appear to be from a trusted source. Phishing enables attackers to gain access to data or to steal money by convincing targets to reveal login credentials, account numbers, credit card information, and other sensitive information.
Insider threats are individuals such as current or former employees, partners, or vendors who abuse their permission to access information systems or networks to steal data or mount an attack.
Denial-of-service (DoS) or distributed denial-of-service (DDoS) attacks cause networks, websites, or servers to crash. A denial-of-service attack floods a target with an overwhelming number of requests until the target can no longer perform as usual or continue to serve legitimate requests.
Advanced persistent threats (APTs) are prolonged cybersecurity attacks where an intruder infiltrates the system and remains undetected for an extended period of time to steal sensitive information or spy on the target organization’s activity.
Machine-in-the-middle attacks are a way for hackers (attackers) to surreptitiously insert themselves in the middle of communication between two users to steal data or credentials, or to impersonate a user.
SQL injection is a technique where attackers insert malicious code into a website or app to gain unauthorized access and steal or manipulate information in a database.
- Botnets are networks of malware-infected computers that can be controlled by a cybercriminal to mount large-scale attacks on a targeted computer system.
What are the elements or types of cybersecurity?
A robust cybersecurity program’s security measures will include technology, processes, and policy to protect critical parts of the IT ecosystem. They include:
Network security or information security defends against attacks aimed at vulnerabilities and operating systems, network architecture, servers, hosts, wireless access points, and network protocols.
Cloud security protects data, applications, and infrastructure residing in public, private, or hybrid clouds.
Internet of Things (IoT) security is tasked with securing thousands or millions of devices that are part of an IoT network.
Application security prevents attackers from exploiting vulnerabilities in software.
Identity and access management controls permissions granted to individuals to access systems, applications, and data.
Endpoint security focuses on protecting internet-connected devices like laptops, servers, and mobile phones.
- Data security solutions protect sensitive data and information assets while in transit or at rest through methods such as encryption and data backups.
What are common cybersecurity challenges?
Top challenges for ensuring cybersecurity include:
An evolving threat landscape. Cybercriminals are constantly refining methods and inventing new ways to penetrate security defenses. To protect against attacks, organizations must continually review the effectiveness of their security programs and adopt new technologies to combat rapidly changing attack methods.
Human error. The behavior and actions of users are often the weakest link in the cybersecurity chain. As a result, security awareness education must be part of any multilayered security program.
Increasing reliance on IT systems and cloud services. To remain competitive, organizations are moving more resources to the cloud and relying more heavily than ever on IT systems, increasing the size of their attack surface.
Remote work. A growing number of users are working remotely or from home, increasing the risk that their connections and devices may be compromised.
- Bring your own device (BYOD) policies. As more users prefer to access a corporate network with their own laptops and smartphones, organizations have a harder time securing these devices.
What are cybersecurity best practices?
Invest in a comprehensive security solution. The most effective approach to cybersecurity is a multilayered defense that protects an organization and critical infrastructure from a wide range of threats.
Implement a Zero Trust approach. Traditional perimeter-based defenses (like firewalls and antivirus software) assume that any traffic or user already within the network can be trusted. Yet this approach is ineffective against attacks that successfully land and move laterally within a network to infect devices and access systems. A Zero Trust approach to cybersecurity assumes that any request may be compromised and requires every user, device, and connection to be authenticated before access is granted.
Deploy strong identity and access management (IAM) technology. IAM solutions define the roles and access privileges for users. Strong IAM solutions require multi-factor authentication and provide visibility into suspicious activity on endpoints.
Stop cybersecurity threats with Akamai security solutions
Akamai has long been a global leader in solutions that help businesses develop and run applications while keeping experiences closer to users. Today, Akamai is a cybersecurity powerhouse as well. Our comprehensive platform provides the tools our customers need to address their biggest threats through a multilayered approach to cybersecurity risk defense. The unique breadth of our offerings is important to customers who want the most effective capabilities while working with fewer vendors.
Akamai cybersecurity framework solutions are highly differentiated and have been recognized as best-in-class technologies to protect enterprise websites, applications, data, access, and other critical assets.
Our solutions include:
Akamai serves as a strategic partner in cybersecurity risk management not only for the breadth and strength of our solutions, but because of the extent of our expertise, the depth of our threat intelligence, and the scale of our platform. We also have the industry’s largest and most experienced teams of cybersecurity professionals, with thousands of engineers and consultants working on security issues for our customers.