Cloud-based security solutions provide security services from servers in remote data centers via an internet connection. With cloud-based solutions, enterprises can avoid the cost and effort of deploying on-premises equipment.
What you need to know about enterprise cloud security
Enterprise cloud security is the collection of practices, protocols, policies, and controls that organizations put in place to secure their digital assets in the cloud. Enterprise cloud security is designed to protect cloud environments, data that resides in the cloud, applications running in the cloud, and users that interact with cloud assets. In most cloud environments, security is a shared responsibility between the cloud provider and the customer.
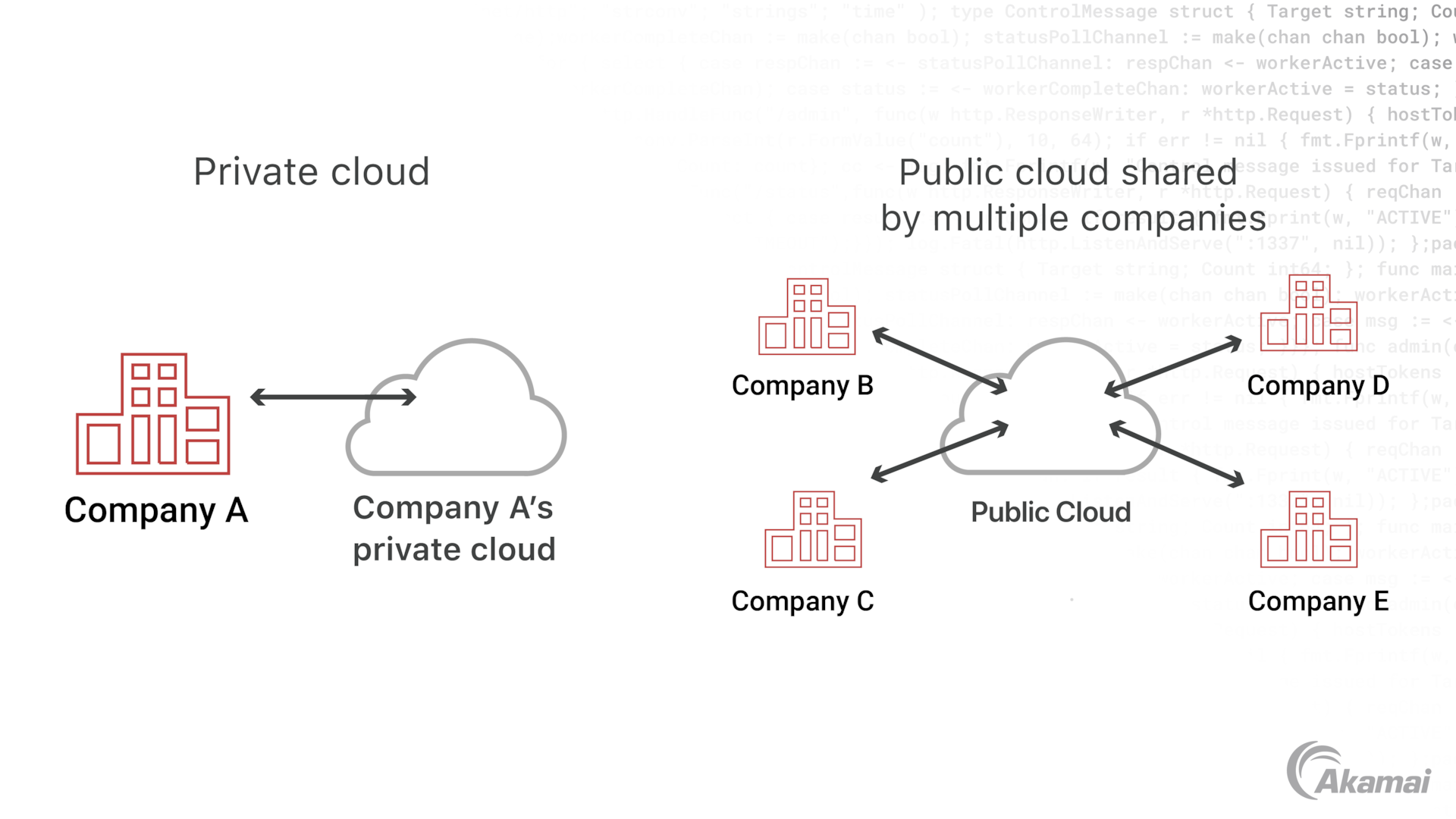
How secure are public vs. private clouds?
Public cloud services are delivered by a third-party provider from a virtualized pool of resources where multiple customers or tenants may be renting computing resources on the same physical server. This can add a slight security risk to a customer’s assets running in the cloud. Additionally, security teams have limited visibility into workloads running on public cloud offerings, making it more difficult to ensure protection. On the other hand, a private cloud may offer greater control and security, since all the resources within the cloud are dedicated to a single customer. Private cloud customers have access to bare metal servers within the cloud that help ensure they won’t compete for bandwidth with other customers — and avoid the security risks that other customers may represent. Additionally, security teams have greater visibility into the underlying infrastructure of a private cloud.
What are threats to enterprise cloud security?
Enterprise cloud environments face a wide array of security challenges and potential security threats.
- Misconfiguration. When security settings are misconfigured or not implemented, it may allow malicious actors to exploit vulnerabilities and easily gain unauthorized access to data, applications, and systems.
- Denial-of-service (DoS) attacks. DoS attacks and distributed denial-of-service (DDoS) attacks are designed to slow down or crash a machine or network. DoS attacks are often a preamble to more devastating attacks.
- Cyberattacks. Cybersecurity threats like ransomware, malware, and data breaches are common and potent, often resulting in millions of dollars of damages for enterprises.
- Unprotected APIs. When APIs that enable software programs to communicate with each other are left unprotected, they make an easy entry point for malicious actors.
- Account takeover. Threat actors can use stolen credentials to access and hijack a user account, impersonating the user to steal money or access sensitive data.
- Data leaks. Malicious or inadvertent data leaks can threaten data security and expose sensitive information or customer data stored in the cloud.
- Human error. Research shows that most cloud security failures are the result of human error such as visiting a malicious website, sharing login credentials, falling for a phishing scam, or failing to practice good security hygiene.
What are the challenges of enterprise cloud security?
- Multitenant cloud environments. Customers in public cloud environments utilize cloud resources that may share a physical server with other customers or tenants, increasing concerns that a customer’s assets may be compromised by malicious attacks on another tenant.
- Lack of visibility. Visibility can be an issue for organizations using multiple cloud providers. This decentralized approach to cloud management can create blind spots such as endpoints, workloads, and traffic that are not properly managed or secured.
- Shadow IT. With the trend toward remote and hybrid workplaces and the use of personal devices, there’s a greater risk of users employing shadow IT or unauthorized cloud resources as they seek to access the data and resources they need to stay productive.
- Dynamic workloads. Workloads in the cloud involve a variety of processes and resources including VMs, containers, databases, and more. Ensuring that every part of the workload is secured can be a complex endeavor.
- Regulatory compliance. Regulatory frameworks like HIPAA and PCI DSS have strict requirements for how enterprises must store, use, and protect customer data and patient information. When data is stored in the cloud, organizations may find it harder to ensure compliance with data residency and sovereignty requirements.
What is the shared responsibility model for enterprise security?
Most cloud service providers approach enterprise cloud security with a shared responsibility model. Under this arrangement, the cloud provider is responsible for securing the underlying infrastructure that they make available to customers as cloud services, and the customer is responsible for securing any part of the cloud environment over which they have control. When IT teams and organizations are unclear about their responsibilities under this model, it can lead to gaps in security controls and programs that can be easily exploited by malicious actors.
How does shared responsibility work in different cloud environments?
The level of responsibility that enterprises have to protect their assets in the cloud depends on the type of cloud service delivery model. In infrastructure as a service (IaaS) solutions, the cloud provider is responsible for securing infrastructure like servers, storage, and networking components, while the customer is responsible for securing applications, endpoints, workloads, and data. In platform as a service (PaaS) offerings, the cloud provider secures all hardware and software, while the customer is responsible for securing any applications developed on the platform, as well as endpoints, workloads, and user and network security. In software as a service (SaaS) solutions, the cloud services provider secures all infrastructure and applications, while the customer is responsible for securing only endpoints, workloads, data, and user and network security.
What are the keys to enterprise cloud security?
To maintain a strong security posture, enterprise cloud security requires a multilayered approach to security strategy. The most common cloud-based security solutions include:
- Identity and access management. Robust access control, strict permissions, and multi-factor authentication solutions make it more difficult for threat actors to use stolen credentials to access cloud environments.
- Continuous monitoring. Security solutions that allow IT teams to continuously monitor cloud platforms and services can help to quickly identify and remediate potential threats.
- Cloud network security. Solutions for segmenting cloud assets can reduce the impact of a breach. Cloud network security technology can also monitor traffic, and protect data and digital assets against exploitation and lateral movement.
- Data protection. Encrypting data in transit and at rest can protect data stored in the cloud and simplify compliance with a wide range of laws and regulations.
- Threat intelligence. Access to up-to-the-minute threat intelligence can help organizations identify and defend against emerging cyberthreats.
- Cloud access security brokers (CASBs). A CASB sits between customers and their cloud services to help enforce security policies and add a layer of security.
- Zero Trust Network Access (ZTNA). ZTNA solutions provide secure remote access to cloud assets with every request, ensuring users or requesting applications are continually authenticated.
What are the advantages of cloud-based security?
Cloud-based security solutions provide security services from servers in remote data centers via an internet connection. With cloud-based solutions, enterprises can avoid the cost and effort of deploying on-premises equipment. Security teams can manage security programs remotely from a single dashboard, from anywhere in the world. Cloud-based security solutions offer much greater scalability than on-premises technology, and choosing cloud-based solutions helps to future-proof security systems.
Frequently Asked Questions (FAQ)
With public cloud services, multiple customers or tenants may share computing resources on the same physical server, increasing risk for assets in the cloud. Additionally, security teams have limited visibility into workloads running on public cloud offerings, making it harder to ensure protection. Private cloud environments offer greater control and security, since all the resources within the cloud are dedicated to a single customer, and security teams have greater visibility into the underlying infrastructure of a private cloud architecture.
Cloud optimization is the process of determining the best way to choose and allocate cloud resources to maximize performance while reducing waste and minimizing cost. By helping to mitigate the uncontrolled spread of cloud instances, services, or providers across an organization, cloud optimization can help improve security posture.
Public and private clouds are ways to store data on the internet. Public cloud services are shared between multiple customers, meaning they can be less secure. Private clouds are only for one customer and give them more control and security.
Why customers choose Akamai
Akamai powers and protects life online. Leading companies worldwide choose Akamai to build, deliver, and secure their digital experiences — helping billions of people live, work, and play every day. Akamai Connected Cloud, a massively distributed edge and cloud platform, puts apps and experiences closer to users and keeps threats farther away.