Akamai powers and protects life online. Leading companies worldwide choose Akamai to build, deliver, and secure their digital experiences — helping billions of people live, work, and play every day. Akamai Connected Cloud, a massively distributed edge and cloud platform, puts apps and experiences closer to users and keeps threats farther away.
Understanding an ICMP flood DDoS attack
An Internet Control Message Protocol (ICMP) flood is a type of denial-of-service attack, or DoS attack, that was highly popular among attackers in earlier years. While it has fallen out of favor as a primary attack vector, it is often used alongside other methods to create highly complex attacks that are more difficult to mitigate, also known as multi-vector attacks.
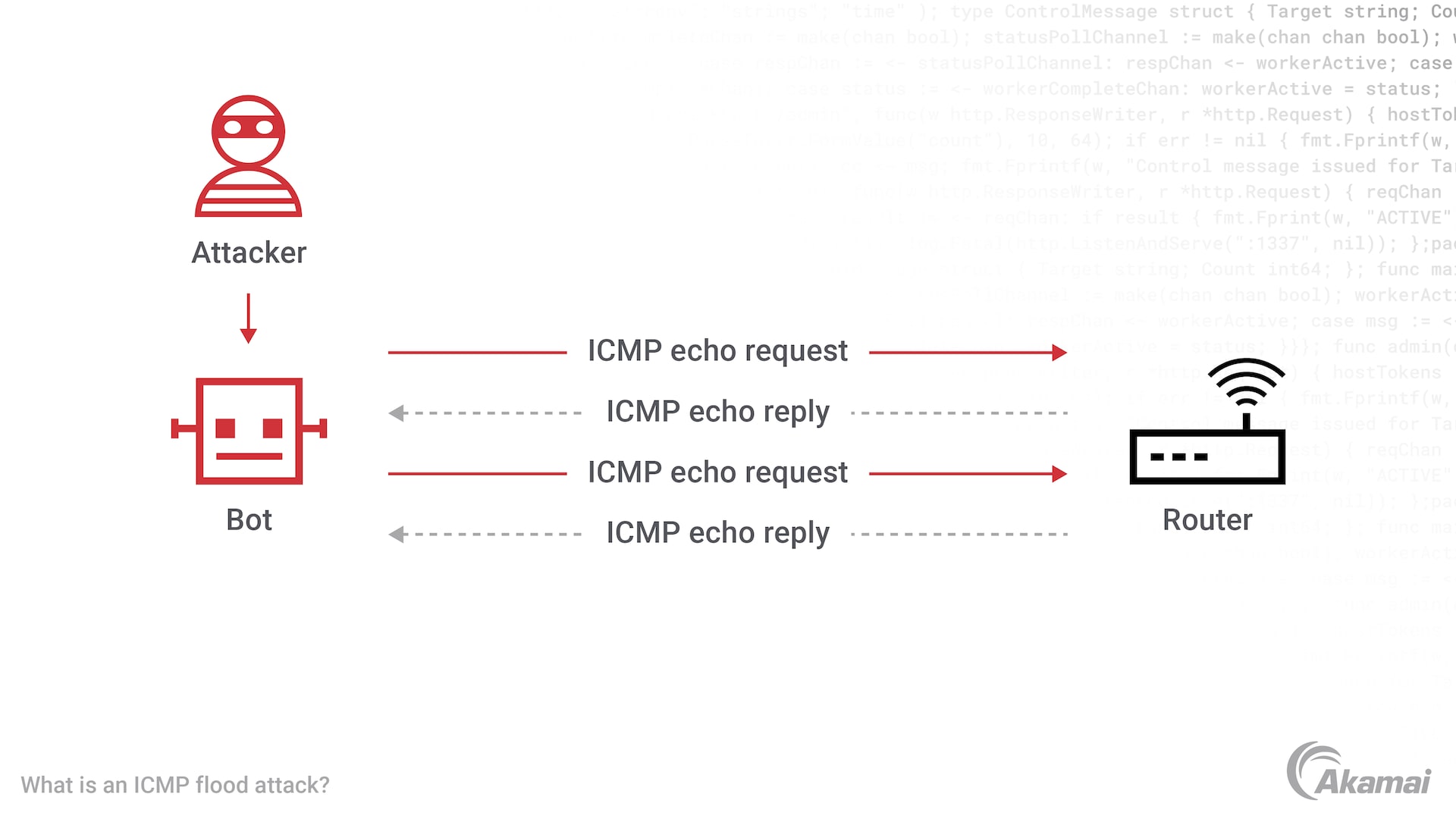
ICMP floods take advantage of the Internet Control Message Protocol that uses echo-requests and echo-replies, or pings, to check on the health and connectivity of a device. In an ICMP flood attack, sometimes referred to as a “ping flood attack,” attackers overload the bandwidth of a targeted network router or IP address, or overload a device’s ability to forward traffic to the next hop downstream by overwhelming it with crafted ICMP packets. As the device tries to respond, all of its resources (memory, processing power, interface rate) are consumed and it can no longer serve legitimate requests or users.
Akamai offers a suite of DDoS protection solutions that can instantly block ICMP floods and other DDoS attacks in the cloud, before they reach applications, data centers, and infrastructure. Akamai’s purpose-built solutions deliver high-performance mitigation to defend against the largest, most complex DDoS attacks today. By reducing attack surface and risk across your hybrid environment proactively for always-on mitigation, Akamai has the ability to stop them in zero seconds, before they cause havoc on your production or corporate internet resources.
How criminals execute an ICMP flood
The Internet Control Message Protocol, or ICMP, was originally designed to test the connectivity between two devices by measuring the amount of time that elapses between sending an ICMP echo-request or ping and receiving an echo-reply. Over the years, ICMP has become part of service providers’ or cloud providers’ ability to monitor the health and state of internet resources — and attackers know that. Threat actors can configure a number of ICMP packets from real source IPs or use spoofing techniques that will generate a certain number of echo-request packets, ping requests, ICMP packets, or data packets, to a targeted device or targeted server. The echo-replies are sent back to the original requesting source IP with the same number of reply packets. Generating large volumes of attack traffic, the attacker not only consumes all available bandwidth on the targeted device, making it inaccessible to normal and legitimate traffic, but also any network devices or next-hop upstream/downstream devices connected to that targeted endpoint.
An ICMP flood can be initiated from a single machine in a denial-of-service attack, or from a botnet as part of a distributed denial-of-service (DDoS) attack. While ICMP DDoS attacks are not as dangerous or as difficult to mitigate as many other attack vectors, they can be used in conjunction with methods such as UDP flood, RESET flood, SYN flood TCP anomaly, PUSH flood and other attack vulnerabilities to create enormously large and complex DDoS attacks. If some of your normal traffic is ICMP and you receive an ICMP flood, then mitigation becomes a bit more complex and requires more advanced controls to ensure quality or consistency of mitigation, due to false positives. ICMP amplification, also known as a Smurf attack, follows the same techniques as traditional ICMP but does not require the attacker to leverage their own hacked resources and can leverage open resolvers or other infrastructure vulnerable to DNS exploitation.
Akamai DDoS protection
Akamai security solutions take a holistic approach to DDoS protection. Acting as a first line of defense, Akamai protects IT environments with dedicated edge, distributed DNS, and cloud mitigation strategies that prevent collateral damage and avoid single points of failure. Where other cloud security provider architectures are designed as “all in one” solutions, Akamai’s purpose-built DDoS clouds offer increased resiliency, dedicated scrubbing capacity, and higher quality of mitigation.
Akamai DDoS protection delivers:
Capacity and scale. We offer the world’s largest mature global DDoS mitigation clouds, allowing us to provide DDoS protection services for multiple clients while simultaneously fighting multiple DDoS attacks. Whether you are protecting entire data centers, individual applications, or authoritative DNS, our solutions deliver the highest capacity, fastest mitigation, and greatest resiliency.
Proven success. We have mitigated some of the largest DDoS attacks ever launched. Our proactive mitigation controls enable true zero-second mitigation, enabling us to offer an industry-leading SLA. Our solutions are effective against a wide range of DDoS attacks, including volumetric attacks like ICMP DDoS attacks, protocol attacks like SYN floods, and application-layer attacks like Slowloris.
Protections that evolve as quickly as attack vectors. DDoS attack vectors keep changing, and the size and complexity of DDoS attacks grows larger every year. Akamai continually invests in, develops, and deploys new tools and rules to detect, simulate, and mitigate attacks, staying ahead of evolving threats.
Solutions that empower a cloud strategy. Akamai Connected Cloud offers DDoS defenses that help extend protections across the core, to the cloud, and to the edge, minimizing risk while providing flexibility around the evolution of future cloud strategies.
A suite of solutions for preventing an ICMP flood
Akamai provides ICMP flood and DoS protection through three purpose-built solutions. The right solution or combination of solutions for your IT environment depends on the use case, application requirements, and desired time-to-mitigate SLAs.
Prolexic
Akamai Prolexic stops UDP flood attacks with a zero-second SLA and the fastest, most effective defense at scale. Prolexic provides cloud-delivered mitigation across all ports and protocols to stop attacks in the cloud before they become business-impacting events. With Prolexic, network traffic is delivered to one of 20+ global high-capacity scrubbing centers, where we can stop attacks closer to the source to maximize performance for users and ensure network resiliency through cloud distribution. At each scrubbing center, the Akamai Security Operations Command Center (SOCC) uses proactive and/or custom mitigation controls to stop attacks instantly, returning clean traffic to the customer origin.
App & API Protector
Akamai App & API Protector is holistic web application and API protection architecture and is designed to defend entire TCP web and API estates with an industry-leading focus on automation and simplicity. This solution brings together core technologies including API security, web application firewall, bot mitigation, and DDoS protection. App & API Protector defends against a broad range of threats, including volumetric DDoS attacks like UDP floods and ICMP floods, injection and API-based attacks, application-layer attacks like Slowloris, and protocol-based threats like TCP out-of-state attacks, SYN floods, or ACK floods that require legitimate users to complete the three-way handshake.
Edge DNS
Akamai Edge DNS is a cloud-based DNS solution that leverages Akamai Connected Cloud to provide access to thousands of DNS servers in more than 1,000 points of presence worldwide. With Edge DNS, organizations no longer need to rely just on two or three DNS servers, a common practice that leaves organizations vulnerable to data center outages and DDoS attacks. This Akamai solution can absorb the largest DDoS attacks while continuing to respond to legitimate user requests, improving DNS resiliency and responsiveness.
Frequently Asked Questions (FAQ)
An Internet Control Message Protocol (ICMP) flood attack is a common distributed denial-of-service (DDoS) attack where malicious actors try to overwhelm a server or network device with ICMP pings, or echo-request packets. Typically, ICMP pings are used to determine the health of a device and the connection to it. By overwhelming a targeted device with ICMP flood DDoS attacks, a device loses its ability to respond with an equal number of reply packets, consuming too many resources and rendering the device unable to function legitimately.
By preventing legitimate requests from getting through to a device, an ICMP flood attack can prevent users from accessing essential applications and services that rely on ICMP as a health monitor or beacon for availability.