Akamai powers and protects life online. Leading companies worldwide choose Akamai to build, deliver, and secure their digital experiences — helping billions of people live, work, and play every day. Akamai Connected Cloud, a massively distributed edge and cloud platform, puts apps and experiences closer to users and keeps threats farther away.
Understanding malware
Malware isn’t going anywhere
Malware remains one of the most pervasive and effective threats to IT security. Each year, cybercriminals launch billions of malware attacks on global businesses, and more than 500,000 new pieces of malware are detected every day. From viruses and Trojans to adware and ransomware, malware enables criminals to steal money and data, hijack computers, spy on computer activity, and damage or disrupt business operations.
Combating a malware infection today requires a multilayered approach to cybersecurity. All systems, from the cloud, to an on-prem operating system, to the edge, are at risk of a malware attack. Any history of malware attacks shows that your defenses must not only attempt to block malware before it lands, but also identify attacks that have already breached defenses and are moving laterally throughout your IT environment. Your cybersecurity solutions should offer threat intelligence that enables your security teams to automate threat protection with insights into recent malware attacks.
Akamai’s robust, flexible platform protects many aspects of your internet-facing infrastructure against a growing range of threats and vulnerabilities. Our security solutions protect your entire ecosystem from cyberattacks without creating lag for your clouds, apps, APIs, and users.
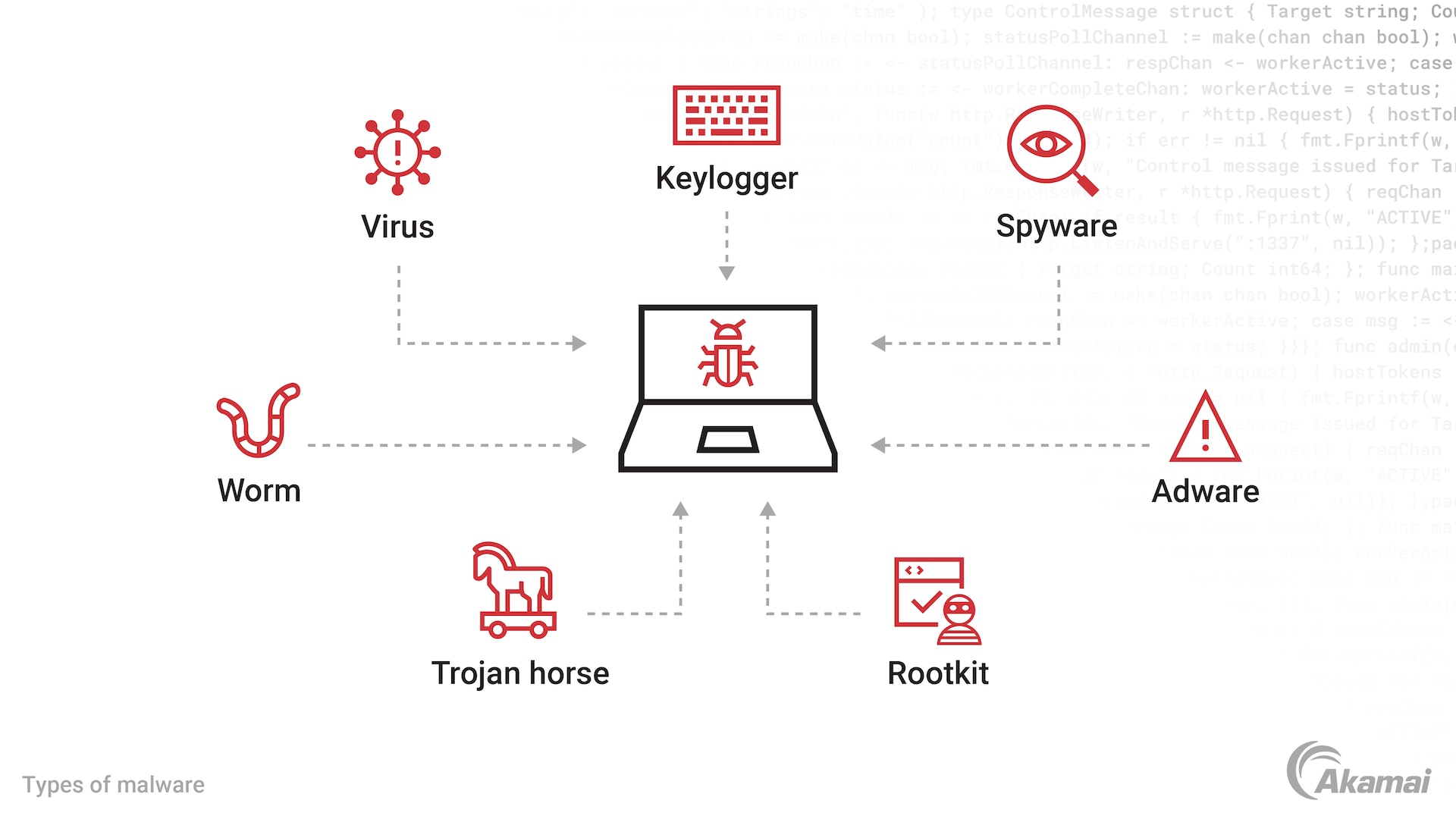
Types of malware
The most common types of malware fall into several categories.
A virus is a piece of software attached to a document or file, which can spread as a computer virus to various systems, like mobile devices, once it is downloaded.
A worm is malicious software that often self-replicates and spreads to any device within a network, without the need for a host program to disseminate it.
Trojan horses often create a backdoor or remote access capability by appearing to be legitimate software programs and execute malicious functions once they have been installed on a system.
Spyware collects sensitive data and information about a user’s computer and activity without their knowledge.
Adware tracks a user’s browser history and downloads, allowing advertisers to target advertisements to the user with greater precision. This is different from malvertising, where malicious code is injected through ads to compromise systems.
Keylogger malware tracks everything that a user does on a computer, including keystrokes, web pages opened, emails sent, and more.
Rootkit is a type of malware that gives an attacker authorization over a system in order to control it and potentially disrupt the efforts of antivirus software or security software.
Ransomware: most dangerous form of malware
Ransomware is a type of malware that enables cybercriminals to encrypt an organization’s files, documents, and other high-value data, and then demand a ransom (usually in cryptocurrency) from the organization to restore access to the data. This type of malware typically gains an initial foothold through social engineering or scareware attacks like phishing emails and spear-phishing campaigns or by exploiting application vulnerabilities. Once ransomware attacks have landed and infected computers or laptops within an IT environment, they move laterally across the network to seek out and encrypt high-value targets. Traditional legacy firewalls are virtually powerless to stop this type of movement, as they can’t block traffic within a virtual LAN, or VLAN.
Akamai Guardicore Segmentation provides a simple, yet powerful way to block ransomware and other adware or spyware attacks from moving laterally within your network, which protects any backups you have or personally identifiable information (PII), like credit card data, separated from the attack. This Akamai solution uses microsegmentation policies to strictly limit communication with digital assets, blocking suspicious and malicious requests that may be part of a malware campaign to keep your systems functioning. Akamai Guardicore Segmentation provides both the real-time and historical visibility required to map application dependencies and flows, which can be used to quickly create AI-powered recommendations for granular segmentation policies that can be implemented in a few clicks.
Comprehensive breach detection capabilities include reputation analysis, dynamic deception, and a threat intelligence firewall. And Akamai Guardicore Segmentation can protect assets in your segmented network no matter where they are deployed, what operating system they are deployed on, or where they are accessed — in the cloud, on-premises, bare metal, virtual servers, or containers.
Stop malware with Akamai security solutions
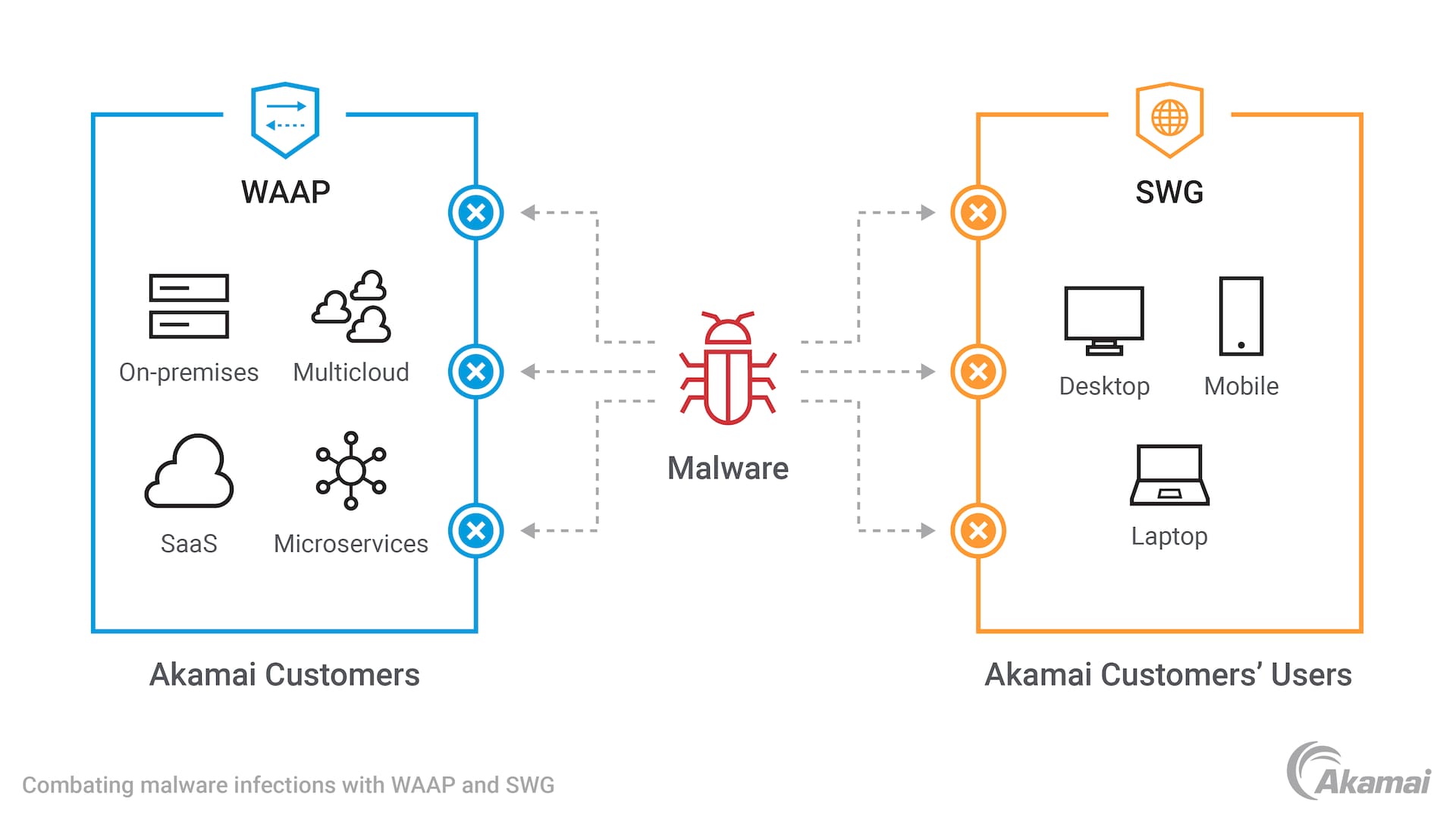 Combating malware infections with WAAP and SWG
Combating malware infections with WAAP and SWG
Akamai security solutions provide intelligent, end-to-end protection against malware threats, data breaches, DDoS attacks, and a wide range of additional multi-vector attacks. Akamai helps your security teams to maximize the effectiveness and ROI of your security investments by moving beyond traditional endpoint detection, using a combination of automation and human specialists to learn what your system looks like when it’s not under threat. Then, when your system is under threat, we know exactly how to identify the attack and stop it.
Akamai offers several anti-malware security solutions designed to block malware outside and inside your IT environment.
Secure Internet Access
Secure Internet Access is a secure web gateway (SWG) that proactively protects against zero-day malware and phishing. With no hardware to be installed or maintained, Secure Internet Access is quick to configure and easy to deploy. Multiple layers of malware protection leverage real-time security intelligence and multiple static and dynamic malware-detection engines. These technologies enable you to proactively identify and block targeted threats such as malware, ransomware, phishing scams, and DNS-based data exfiltration of sensitive information. Through the Akamai portal, security teams can centrally create, deploy, and enforce unified security policies as well as acceptable use policies for all users, however they connect to the internet.
App & API Protector
Akamai App & API Protector protects entire web and API estates with a holistic set of powerful protections. This Akamai solution offers customer-focused automation and self-tuning capabilities that empower security teams to do more with less. Multidimensional, adaptive threat-based detections correlate threat intelligence across the Akamai platform, and advanced decision-making logic stops both common and highly targeted attacks on web applications and APIs with incredible precision. App & API Protector has specialized add-on functions to combat botnets, prevent pop-ups that interrupt customer buying journeys, and scan files uploaded through any web application or web browser for malware and block them before they reach your server.
Frequently Asked Questions (FAQ)
Malicious software, or malware, is a software program or file that is designed to cause damage or disruption to an IT system, or to help hackers gain access to an IT environment. Attackers use a variety of techniques to install and launch malware on computer systems, including writing malicious code into websites and links, weaponizing email attachments, or loading an executable file onto a USB drive instead of just a hard drive.
Malware protection is a security solution that scans files before they are uploaded to web applications to prevent malware from being downloaded to an IT environment, or to stop malicious code from spreading once it has been uploaded.