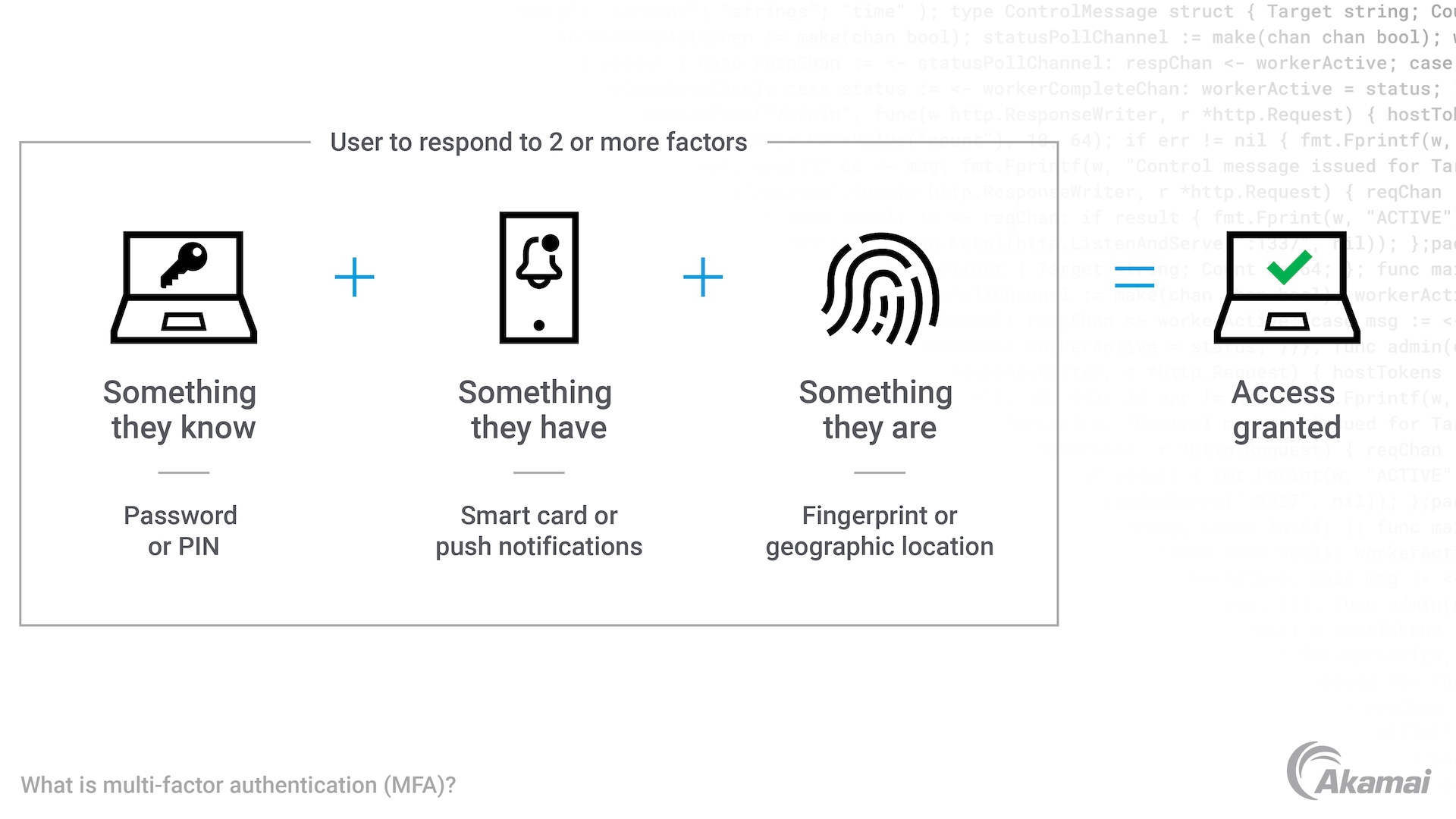
Multi-factor authentication (MFA), also called two-factor authentication, is a security technology that requires a user to present a combination of two or more credentials, or factors, to verify their identity for login. Factors must include something the user knows such as a PIN, password, or answer to a security question; something the user is, which can be satisfied by a fingerprint or facial recognition scan; and something the user has such as a key fob, smart card, one-time password, or push notification to a mobile phone.
Prevent breaches with MFA security
When a user logs in to access an application or service, companies must be absolutely certain that the user is an authorized employee and not a threat actor. Granting access to an unauthorized individual violates the basic principles of Zero Trust, the security model that enables organizations to remove implicit trust.
Multi-factor authentication (MFA) provides an additional layer of assurance when users are requesting access. In addition to a username and password, MFA security requires additional proof of identity such as a fingerprint or facial recognition scan, a key fob, a one-time passcode, or a push notification.
Yet while MFA security offers greater protection than traditional authentication that relies only on a username and password, it can nevertheless be bypassed by a cybercriminal. That’s why more organizations are turning to Akamai MFA to help reduce the risk of employee account takeover and prevent breaches that start with stolen credentials.
The benefits of MFA security
Use of MFA cybersecurity solutions has grown steadily in popularity as organizations seek better ways to protect their networks, data, and users from cyberattacks.
MFA requires two or more forms of authentication credentials to validate a user’s identity. These include:
- Something you know. This type of knowledge-based credential could take the form of a password, PIN, pictograph, or the answer to a security question.
- Something you have. This token-based authentication could be an SMS code delivered to a mobile device, a push notification on an authenticator app, a one-time password (OTP), or a physical device such as a smart card or key fob.
- Something you are. This is a contextual or biometric-based authentication factor. Authentication might be based on a fingerprint, facial recognition, signature, or a voice or speech pattern. This factor could also be based on behavior, location signals, or time of login.
Implementing MFA security substantially reduces the risk of unauthorized access and system breaches. In fact, companies that deploy MFA services are significantly less likely to be compromised than those that do not.
However, since MFA technology first appeared, cybercriminals have developed fairly simple yet effective social engineering and phishing attacks to get past an MFA challenge. As a result, many organizations are seeking phish-proof MFA security solutions. That’s where Akamai can help.
MFA security with Akamai
Akamai MFA represents an innovation in MFA security. Our solution can protect your organization against phishing, credential stuffing, and account takeover with a first-of-its-kind MFA technology that will enable a secure, truly passwordless future.
Akamai MFA leverages FIDO2, the strongest standards-based authentication method available. The FIDO2 standard creates cryptographic login credentials that are unique across every website, never leave the user’s device, and are not stored on a server. As a result, MFA security with the FIDO2 standard is virtually impossible to hack via phishing and social engineering.
Most FIDO2-based MFA security solutions require organizations to deploy the MFA service and to buy, distribute, and manage hardware security keys. Not only does this raise the cost and complexity of managing MFA services, but it creates a less-than-ideal user experience. When employees lose or forget their keys, it can be time-consuming and frustrating to regain access to essential apps and services.
Akamai solves this issue by replacing physical hardware tokens with a smartphone app that results in a delightful and frictionless end-user experience. When an employee receives the secure push notification from Akamai MFA, they can be completely certain it’s genuine.
Benefits of Akamai MFA
Akamai MFA enables users to authenticate quickly and easily using a mobile app on their smartphone. When a user provides their username and password to a primary authenticator such as Microsoft Azure AD, the Microsoft authenticator validates the credentials and connects to Akamai MFA to generate a second factor. Akamai renders a page that allows the user to select an authentication factor and sends a phish-proof push to the user’s mobile device. Once the user responds, Akamai MFA returns control to the primary authenticator, which grants the user permission to access the requested applications or services.
With Akamai MFA, businesses can:
- Reduce risk by deploying authentication technologies based on the strongest security standards available
- Lower total cost of ownership (TCO) by authenticating through existing smartphones and web browsers, with no need to purchase, replace, and maintain additional hardware
- Ensure a frictionless user experience that allows users to authenticate with familiar push notifications
- Implement two-factor authentication quickly and easily using the time-based Akamai MFA app on existing smartphones
- Support the organization’s move to Zero Trust networking and SASE security frameworks
Frequently Asked Questions (FAQ)
By requiring an additional layer of security to successfully authenticate users requesting access to an application or service, MFA security solutions are an essential part of Zero Trust networking and remote work security. Companies that deploy the additional security of an MFA solution are far less likely to be the victim of a security breach than companies that do not.
Why customers choose Akamai
Akamai powers and protects life online. Leading companies worldwide choose Akamai to build, deliver, and secure their digital experiences — helping billions of people live, work, and play every day. Akamai Connected Cloud, a massively distributed edge and cloud platform, puts apps and experiences closer to users and keeps threats farther away.