- Implement secure authentication and authorization methods, like OAuth or OpenID Connect.
- Encrypt sensitive data in transit and at rest.
- Validate and sanitize user input to prevent injection attacks.
- Use secure coding practices and keep software up to date to address known vulnerabilities.
- Monitor and log API activity to detect and respond to security incidents.
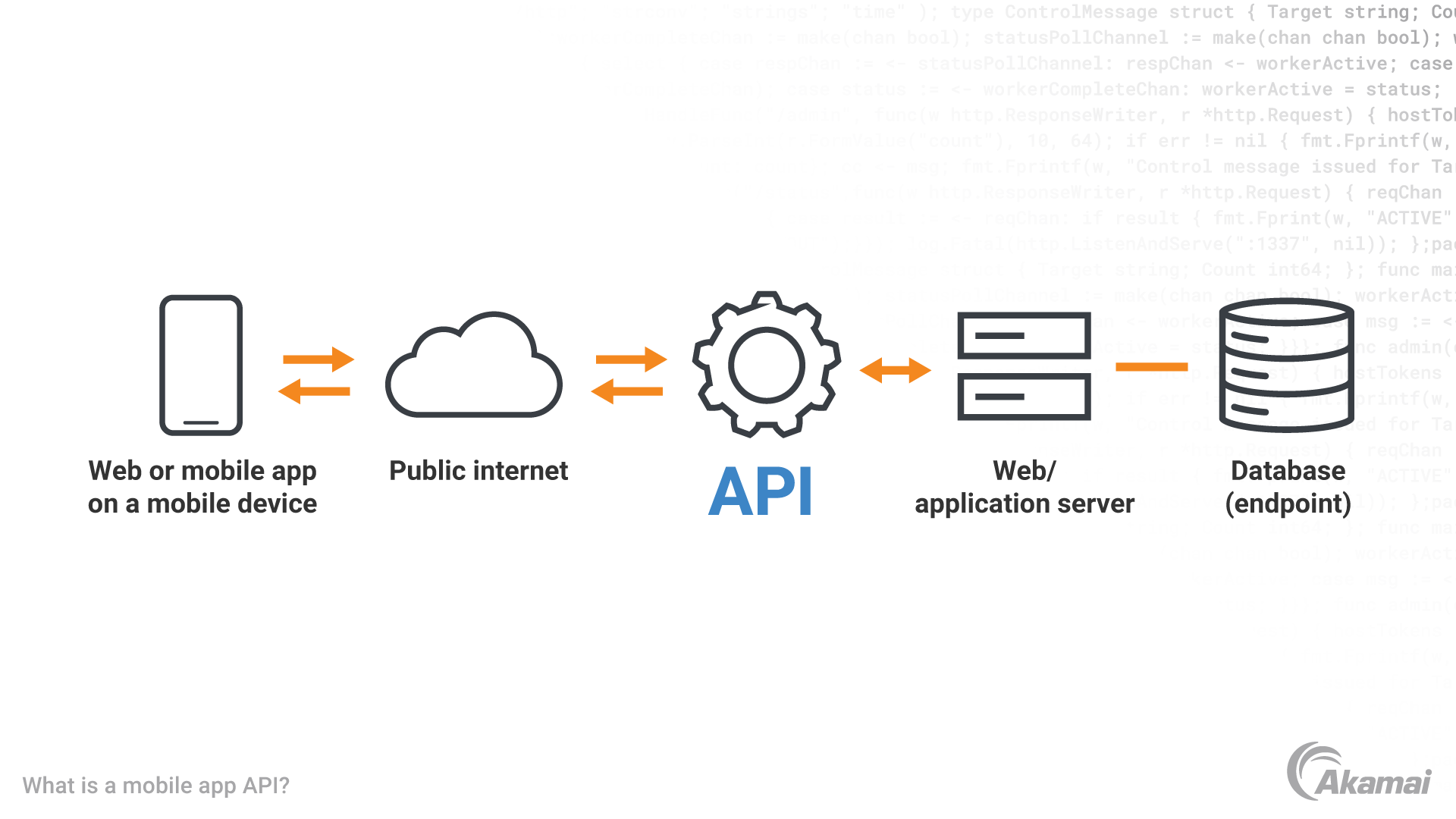
API security is an important part of the development of mobile apps. APIs are the key communication channels between the app and the back-end systems, and they handle sensitive data and transactions
To protect against security threats, it is important to implement secure authentication methods, encrypt sensitive data, validate user input, use secure coding practices, and monitor API activity.