Network segmentation — and microsegmentation, in particular — can help to achieve a Zero Trust framework. By isolating critical IT assets and protecting them with microperimeters that limit access only to authorized users and purposes, segmentation plays a critical role in improving network security.
Network Segmentation and Zero Trust
As more organizations adopt a Zero Trust framework for their IT environments, security teams need powerful network segmentation solutions that can implement Zero Trust policies quickly and efficiently. In Zero Trust networks, no user, device, or application inside or outside the network can be automatically trusted or deemed safe. Each must be validated before it’s allowed to gain access to internal network assets in the data center or assets in the cloud.
To accomplish this, Zero Trust security uses network segmentation technology to apply microperimeters of control around critical assets and sensitive data. This allows security teams to set granular policies that limit and control access to these assets, minimizing the attack surface and effectively stopping the spread of attacks that have started or landed inside the perimeter of an IT environment.
To be effective, Zero Trust network segmentation requires two core capabilities: visibility of the entire IT environment and the ability to efficiently create and manage microperimeters across dynamic environments. When seeking a solution that enables a faster path to Zero Trust network segmentation, more enterprises turn to Akamai.
How to enable Zero Trust with Akamai
Akamai lets you implement Zero Trust network segmentation policies in five simple steps:
Map connections and flows
Akamai Guardicore Segmentation offers real-time and historical maps that deliver total visibility into applications, workloads, and devices as well as the connections and flows between them. This visibility ensures that your Zero Trust network segmentation policies will be based on complete understanding of application dependencies.
Set microperimeters
Akamai offers automatic Zero Trust recommendations that help your IT operators quickly design secure perimeters.
Enforce Zero Trust segmentation
Akamai’s software-based technology offers a more agile way to achieve Zero Trust network segmentation than internal firewalls and VLANs. With Akamai, you can segment down to the application level to ensure your policies follow workloads across any infrastructure.
Rely on security automation and orchestration
Akamai Guardicore Segmentation integrates easily with orchestration tools to streamline deployment in complex environments. In addition to integrations with many commercial and open source platforms, we offer an extensive, well-documented open REST API that lets you create your own integrations when implementing Zero Trust network segmentation.
Secure your workloads
Implement Akamai’s breach detection technologies to identify and block malicious traffic. Dynamic deception capabilities help identify and analyze malicious lateral movement. And signature-based reputation analysis can detect malicious processes in network traffic.
Frequently Asked Questions (FAQ)
Network segmentation is the practice of splitting a network into multiple subnetworks, or subnets. IT operators have long used network segmentation to boost performance and improve cybersecurity.
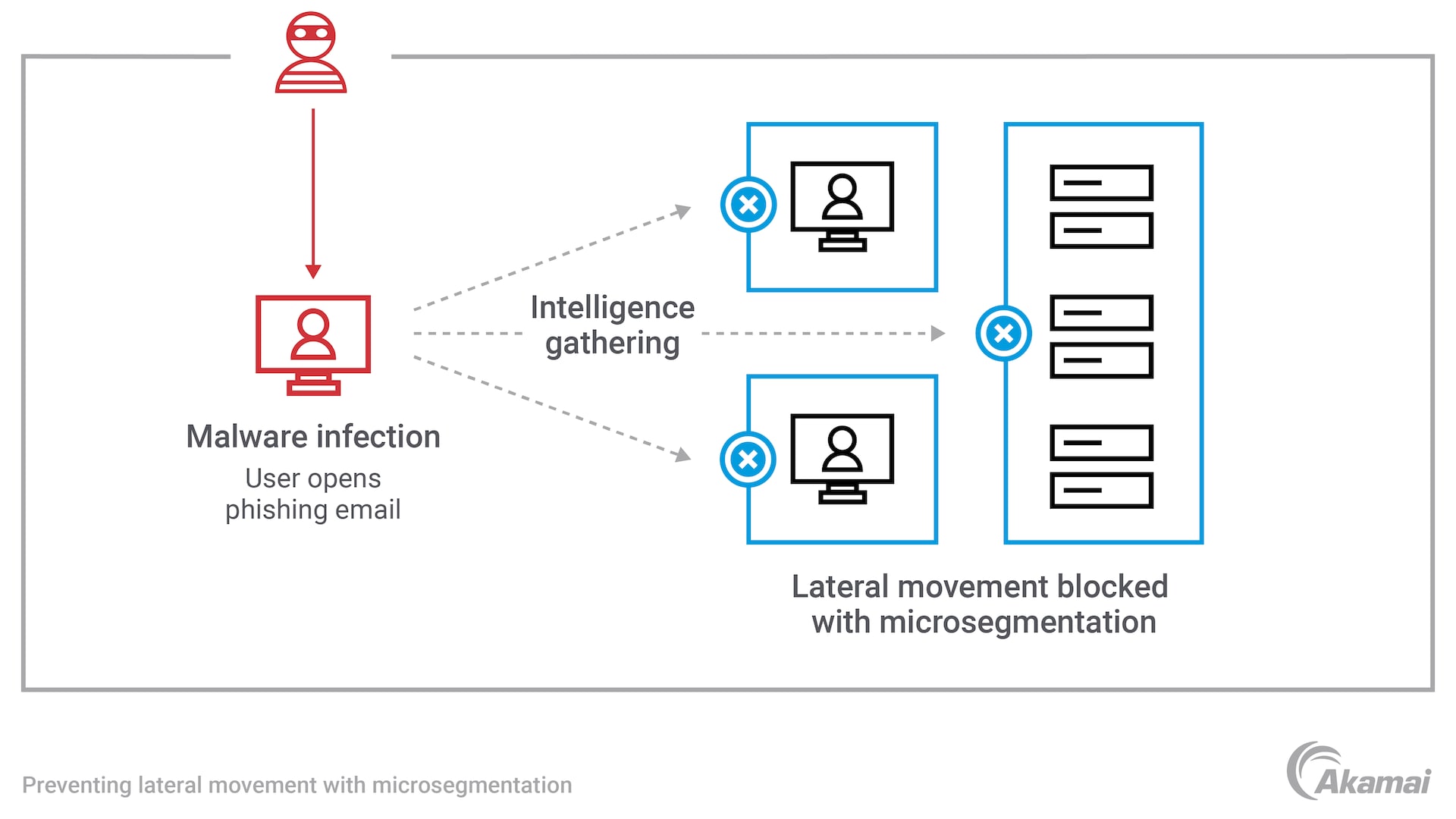
Microsegmentation is a more granular type of network segmentation that can secure individual workloads and isolate them from one another. IT operators can set segmentation rules for elements such as users, devices, domain names, processes, and containers. As a result, microsegmentation is superior at controlling east-west traffic flows within an entire network and protecting against attacks that spread through lateral movement.
For this reason, microsegmentation is far more effective at creating the microperimeters required for Zero Trust security. Traditional network segmentation tools such as internal firewalls, virtual local area networks (VLANs), and access control lists (ACLs) are too complex to manage security controls across dynamic, hybrid IT environments. They are also too slow to adapt to changing business requirements. In contrast, software-defined microsegmentation tools offer greater speed and agility for isolating and segmenting IT assets and enforcing Zero Trust network access. This approach to Zero Trust network segmentation offers IT teams more flexibility for segmenting assets across on-premises and hybrid cloud environments, dramatically increasing cybersecurity.
The concept of Zero Trust is a fundamentally different cybersecurity model than the typical “moat and castle” strategy that ignores threats and compromised assets within a defined network perimeter. Zero Trust security assumes that every system, device, user, and connection may be already compromised, whether it is inside or outside the network. Each of these elements must be validated before access is granted to assets within the network.
Zero Trust network segmentation is highly effective at stopping the lateral movement that is the hallmark of cyberattacks like ransomware. Assets that are protected by microsegmentation cannot be easily accessed by attacks that have successfully landed within the network. As a result, attacks can be effectively neutralized and prevented from spreading.
Akamai Guardicore Segmentation. The fastest way to visualize and segment your assets in the data center, cloud, or hybrid cloud infrastructure.
Enterprise Application Access. Give your workforce fast, secure access with Zero Trust Network Access.
Secure Internet Access. Explore Secure Internet Access, a cloud-based secure web gateway.
Akamai MFA (multi-factor authentication). Prevent employee account takeovers and data breaches with phish-proof MFA.
Why customers choose Akamai
Akamai powers and protects life online. Leading companies worldwide choose Akamai to build, deliver, and secure their digital experiences — helping billions of people live, work, and play every day. Akamai Connected Cloud, a massively distributed edge and cloud platform, puts apps and experiences closer to users and keeps threats farther away.

