Any organization covered under PCI DSS is subject to stringent penalties and fines for noncompliance with the standard. Fines vary and depend on the severity of the regulation infringement. But typical fines are a few thousand to hundreds of thousands of dollars, which can continue until rectification. However, the cost to reputation can be much higher. The lack of customer trust because of data breaches can lead to loss of customers and even class actions: A data breach involving 34 million payment cards ended in an $8 million lawsuit in 2019; the investigation found several PCI DSS violations.
Hackers follow the money, so financial transactions are a focus for fraud and cybercriminal activity. For example, a 2022 report from Akamai found that web application and API attacks against financial services firms grew by 257% compared with the previous year. In addition, figures from the Federal Trade Commission show that consumers lost almost $8.8 billion in 2022 due to financial fraud, an increase of 44% from 2021 figures.
To help stem the tide of financial fraud and financial crime with payment card data, the PCI Security Standards Council offers an information security standard known as PCI DSS (Payment Card Industry Data Security Standard). Here is a look at what the PCI DSS requirements entail.
Overview of PCI DSS
PCI DSS is a set of security standards that was launched in 2004; these standards apply to any organization that accepts, processes, stores, or transmits credit card data. PCI DSS is administered by the PCI SSC (Payment Card Industry Security Standards Council), formed from a consortium of major credit card companies: Mastercard, Visa, Discover, American Express, and JCB.
PCI DSS is now a globally recognized standard to enforce payment card data security and prevent security breaches. However, this cybersecurity standard is subject to changes because of emerging and evolving threats. The latest version is PCI DSS v4.0, released in March 2022, and full compliance is required in March 2025 (12 months after PCI DSS v3.2.1 is retired in March 2024).
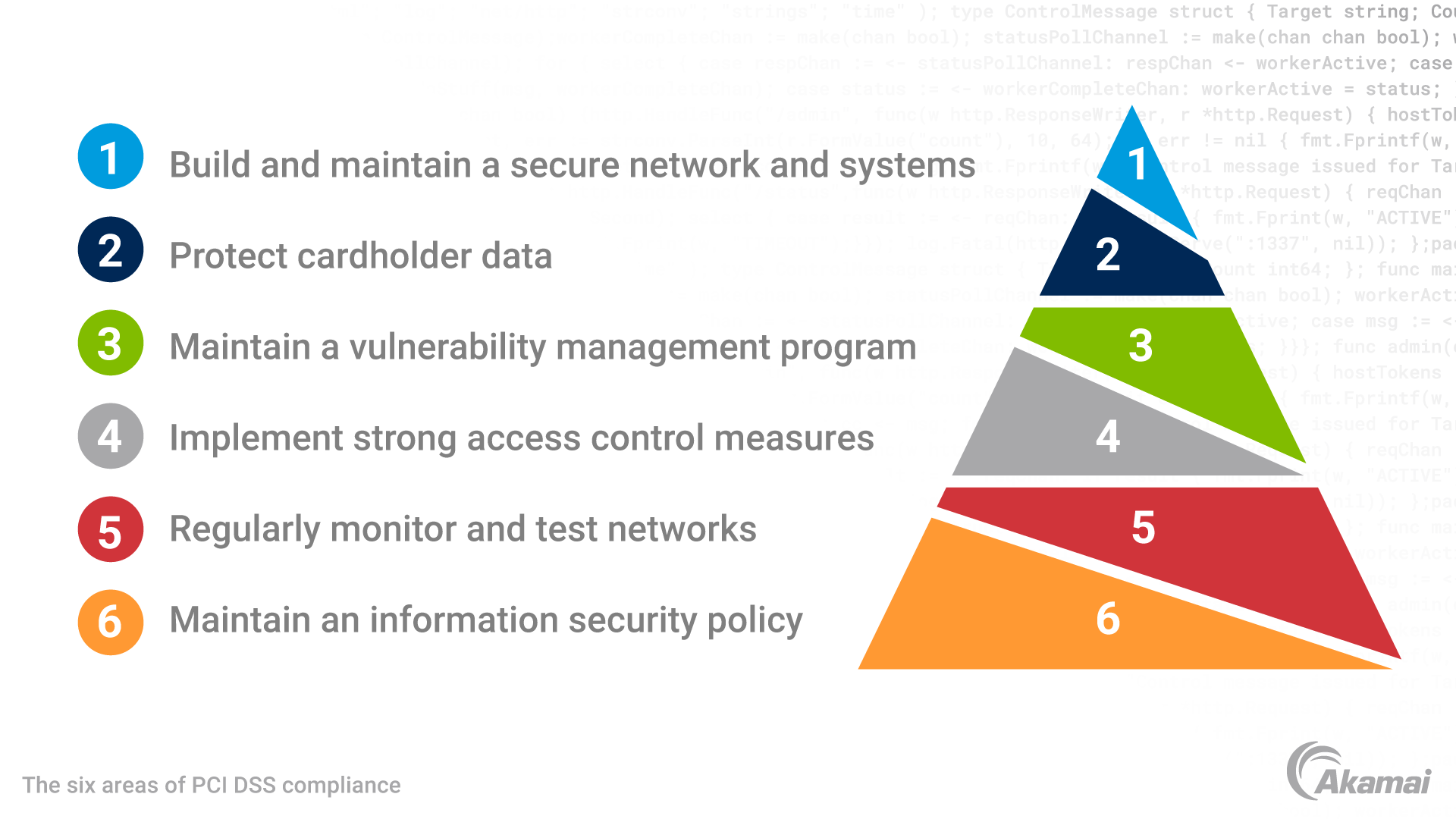
PCI DSS addresses a variety of threats, including the following:
- Malware
- Phishing
- Remote access control and authentication
- Weak passwords
- Legacy software
- Card skimming
PCI DSS security controls
The 12 controls to protect cardholder data covered under PCI DSS are based on the ethos of “people, process, and technology.” Controls include the use of a firewall, data minimization, encrypted transmission of cardholder data, robust access controls, anti-virus software, and regular penetration testing and vulnerability risk assessment, patch management, and general secure environment control.
Types of organizations required to comply with PCI DSS
Any business handling financial transactions is a target for cybercriminals, who follow the money. Ecommerce losses due to online payment fraud are expected to reach more than US$48 billion worldwide by the end of 2023. The PwC Global Economic Crime and Fraud Survey 2022 found that more than half of respondents experienced financial fraud over the previous two years. According to the Verizon 2023 Data Breach Investigations Report (DBIR), in the financial sector, privilege misuse is behind most data breaches.
Since the PCI DSS standard applies to any organization that accepts, processes, stores, or transmits cardholder data, the following types of organizations must demonstrate compliance with the standard:
- Merchants of all sizes
- Financial institutions
- Payment processors, both hardware and software-based
- Point-of-sale (POS) vendors
Examples of organizations impacted by PCI DSS include the following:
Small merchants and retailers
Small and medium-sized businesses (SMBs) are as much at risk of a serious data breach as their larger counterparts. According to the 2022 DBIR, 61% of SMBs experienced at least one data breach. Small merchants must comply with the tenets of PCI DSS, under which there are four merchant compliance levels:
Level 1: Process over 6 million card transactions annually
Level 2: Process 1 to 6 million transactions annually
Level 3: Process 20,000 to 1 million transactions annually
Level 4: Process fewer than 20,000 transactions annually
Small merchants must ensure that security is approached as a comprehensive exercise: ensuring that their IT systems are protected using firewalls, implementing robust access controls, and encryption is applied to cardholder data. To achieve and simplify this level of 360-degree security, SMBs should look for solutions that can secure data, devices, and people.
Service providers
A service provider is any business that could impact payment data security, even belonging to another organization. PCI DSS has two levels of compliance that depend on the transaction levels handled by the service provider:
Level 1 Service Provider: 300,000 or more transactions per year (2.5 million or more transactions for American Express)
Level 2 Service Provider: Less than 300,000 transactions per year (less than 2.5 million transactions for American Express)
As with SMB merchants, service providers must abide by PCI DSS security measures and controls.
How can Akamai help with PCI DSS v4.0 compliance?
Akamai is certified as a PCI DSS Level 1 Service Provider, the highest level of assessment. Akamai also offers a range of solutions that help your organization comply with the six pillars of PCI DSS. The following Akamai solutions offer PCI-compliant security controls to help meet the 12 PCI requirements:
App & API Protector with Malware Protection: Ensure log compliance and protect against PII data leakage, zero-day attacks, and CVEs, as well as other edge-based attacks.
API Security: Detect and mitigate API behavior and logic abuse, protecting the site, assets, and PII loss.
Client-side Protection & Compliance: Maintain an inventory and justification of all scripts executed within the browser, monitor for changes in script behavior, and flag any suspicious script activity.
Akamai Guardicore Segmentation: Scope regulated assets to more easily achieve compliance.
Secure Internet Access Enterprise: Block or monitor content uploads that contain PII, PCI DSS, or HIPAA data.
Frequently Asked Questions (FAQ)
PCI DSS (Payment Card Industry Data Security Standard) sets out security standards to ensure that all companies that accept, process, store, or transmit credit card information maintain a secure environment.
Any organization, irrespective of size or number of transactions, must comply with PCI DSS if that organization accepts, transmits, or stores any cardholder data.
PCI DSS–compliant organizations must focus on protecting financial data. PCI DSS security covers two general classes of data: cardholder data and sensitive authentication data.
Cardholder data
- Primary account number (PAN)
- Cardholder name
- Expiration date
- Service code
Sensitive authentication data
- Full track data (magnetic-stripe data or equivalent on a chip)
- CAV2/CVC2/CVV2/CID
- PINs/PIN blocks
Why customers choose Akamai
Akamai powers and protects life online. Leading companies worldwide choose Akamai to build, deliver, and secure their digital experiences — helping billions of people live, work, and play every day. Akamai Connected Cloud, a massively distributed edge and cloud platform, puts apps and experiences closer to users and keeps threats farther away.

