Spear phishing is a targeted form of phishing that is used to gain access to sensitive information by targeting specific individuals or organizations. It is often used in cyberattacks and is a form of social engineering. It typically involves sending an email to a specific person that appears to come from a legitimate source, such as a trusted contact or colleague, but contains links or attachments that can lead to malicious content.
Phishing remains a dangerous cybercrime
Phishing attacks have grown incredibly sophisticated in recent years. Cybercriminals execute phishing campaigns on an industrial scale, continuously evolving their methods and techniques to fly under the security radar and evade detection. While phishing was once conducted primarily through email, recent attacks use text messages, social media, and other vectors to dupe victims into revealing login credentials, sharing credit card numbers, or downloading malware.
Akamai EVP and CTO Robert Blumofe Explains the Anatomy of a Phishing Attack
Because phishing seeks to take advantage of a user’s willingness to trust messages from what appear to be legitimate sources, security awareness training is a big part of defending against phishing campaigns. However, this approach isn’t a silver bullet. Cybercriminals and their campaigns continue to become more refined, adapting their techniques to overcome basic security awareness training methods. The best defense against phishing attacks uses multiple layers of protection. That’s why more organizations today choose IT security solutions from Akamai to protect users, data, and systems from the threat of phishing and spear-phishing campaigns.
Read the Akamai blog Phishing Is Still a Security Challenge.
How phishing attacks are executed
Phishing campaigns rely on two factors. The first is a lure — something that gets the victim’s attention. This may be a warning or an alarming message with a sense of urgency that causes the victim to act quickly — often without thinking about potential consequences. The second factor is the landing, which might be a malicious link or attachment, a fake website, or a form that requests information such as login credentials or credit card information.
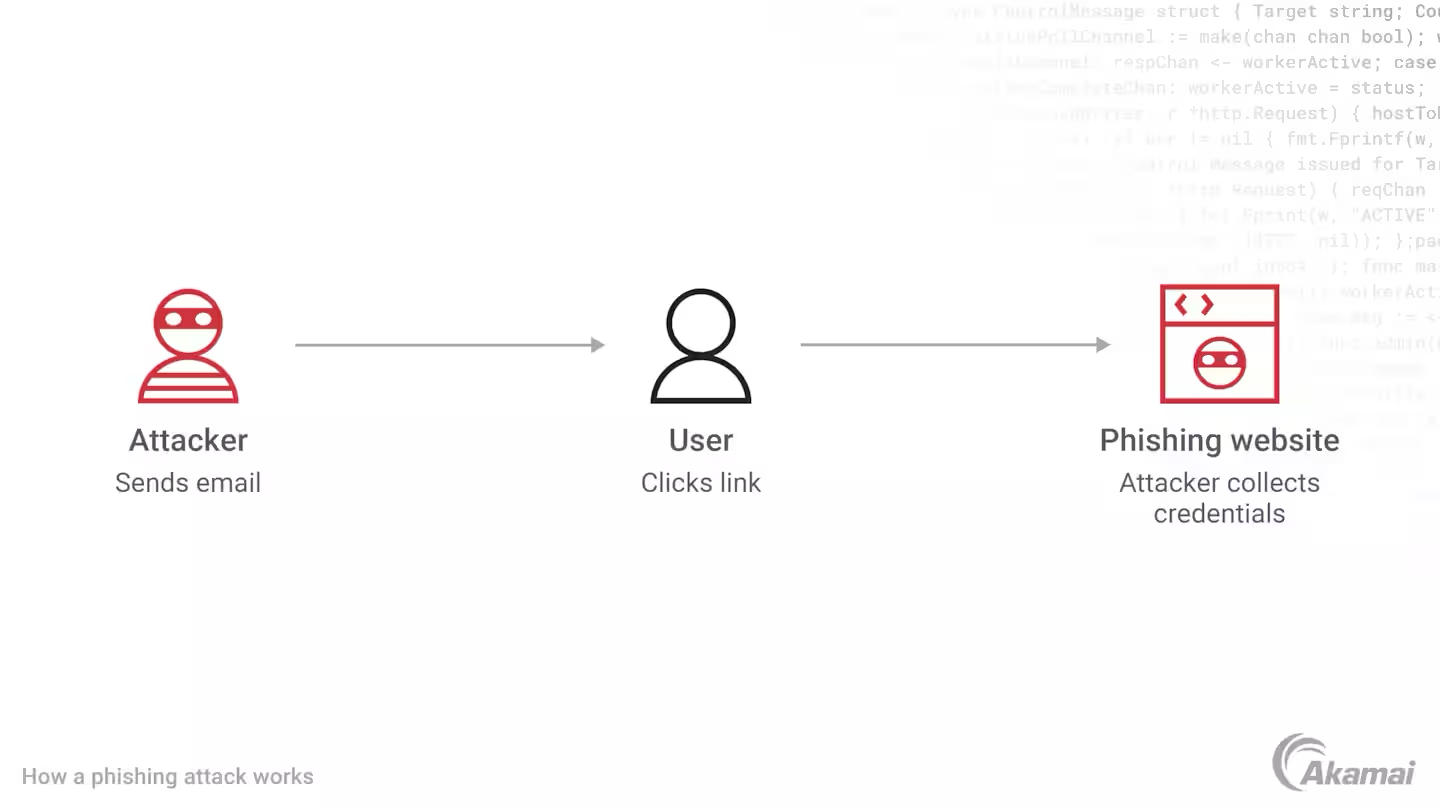
In a standard phishing campaign, attackers send out thousands of phishing messages to potential victims, posing as a legitimate or trusted company and seeking to pressure victims into taking action. In a spear-phishing attack, scammers target a specific individual or group, using social engineering and personal details collected from open source intelligence, social media, websites, and other information in the public domain to convince the target that the sender is legitimate.
When a phishing campaign is successful, the results can be devastating. Phishing attacks can deploy malware to hijack computers as part of a botnet to be used for denial-of-service attacks. Some phishing campaigns convince users to transfer money to fraudulent bank accounts, while other attacks are designed to steal credentials that provide access to high-value sensitive information or intellectual property.
Read the Akamai blog Enemy at the Gates: Analyzing Attacks on Financial Services.
Stop phishing attacks with Akamai
To combat phishing and other cyberattacks, Akamai deploys edge security solutions on a global platform that extends from applications and infrastructure to the user. Situated between potential attackers and your IT ecosystem, our security technology stops attacks in the cloud, at the network edge — before they can jeopardize your applications and infrastructure.
In recent years, our security portfolio has grown from a collection of innovative point solutions into a comprehensive platform with the breadth and depth to protect our customers from the most dangerous threats. Akamai cybersecurity technology surrounds and protects your entire ecosystem — from clouds and users to apps and APIs — providing intelligent, end-to-end protection to defend against a wide range of multi-vector threats.
Akamai stops phishing attacks with solutions that provide:
- Unparalleled scale. The unmatched scale and global distribution of our Akamai Intelligent Edge Platform enables us to stop the largest direct attacks while insulating you from collateral damage of attacks on other customers.
Real-time support. We offer a single point of contact for support and real-time incident response.
Global protection. Defend against attacks on your applications, data centers, public cloud, and multicloud environments anywhere in the world.
Greater visibility. Manage your security programs and multiple security solutions through our web-based portal that delivers greater visibility into attacks and policy control. From high-level dashboards, drill down into different individual areas of concern, integrating existing security information and event management (SIEM) tools to deliver greater awareness across all solutions.
Unified security. Managed from a single pane of glass, our security solutions are designed to work seamlessly together to improve mitigation and simplify management.
- Ease of use. Our Managed Security Service eliminates the need for your teams to deploy physical appliances or software solutions. Our adaptive threat protections keep pace with a quickly evolving threat landscape. And by integrating your application development lifecycle with our management APIs, you can automate changes to your Akamai solution configurations.
- Future-proof solutions. With Akamai security solutions, you can build an infrastructure to respond to future threats, seamlessly deploying new capabilities and solutions as they become available.
Akamai security solutions
Our portfolio offers multiple capabilities to defend against phishing attacks.
Secure web gateway technology
Akamai Secure Internet Access Enterprise safely connects users and devices to the internet while proactively protecting against the zero-day malware and phishing attacks. This Akamai solution offers a multilayered defense that includes multiple static and dynamic detection engines along with threat intelligence developed on the world’s largest edge platform. Secure Internet Access Enterprise can enforce acceptable use policies, identify and block unsanctioned applications, and enhance data loss prevention.
Web application and API protection
Akamai App & API Protector offers one-stop, zero-compromise security for websites, applications, and APIs. With this Akamai technology, you can tailor your defenses by dynamically adapting protections to evolving attacks, including those targeting the OWASP Top 10. Self-tuning capabilities and managed updates simplify security and minimize the effort required from security teams. Advanced API discovery mitigates risk from new or previously unknown APIs while monitoring for malicious payloads.
Microsegmentation
Akamai Guardicore Segmentation is the fastest way to visualize and segment assets in the data center, cloud, or hybrid cloud infrastructure. This software-based segmentation technology prevents lateral movement attacks with a simple, scalable platform featuring real-time threat detection and response capabilities to enforce Zero Trust principles.
Multi-factor authentication
Akamai MFA prevents employee account takeover and data breaches with phish-proof multi-factor authentication. Using the familiar and frictionless experience of a mobile push to a smartphone — rather than clunky physical security keys — Akamai MFA stops bypass attacks with the most secure standard for multi-factor authentication. Self-service enrollment simplifies adoption while end-to-end cryptography and a sealed challenge/response flow make this solution unphishable and confidential.
Scalable secure remote access
Akamai Secure Internet Access Enterprise enables your workforce to connect to your IT ecosystem with Zero Trust Network Access. Using an identity-aware proxy in the cloud, this flexible and adaptable service provides granular decision-making access based on real-time signals such as threat intelligence, user information, and device posture.
Frequently Asked Questions (FAQ)
Phishing is a type of cybercrime in which hackers attempt to defraud victims to steal confidential information such as usernames, passwords, credit card numbers, and other sensitive data. Phishing attacks typically use email messages that look like they’re from a legitimate company or organization. Phishing emails usually ask the recipient to click on a link to a malicious website or open an attachment, which allows attackers to steal their login credentials or surreptitiously download malware to the computer.
A multilayered approach to security is the best way to prevent phishing attacks. This may include a secure web gateway, security awareness programs, multi-factor authentication, microsegmentation, and a diligent cadence for patching software vulnerabilities.
Why customers choose Akamai
Akamai powers and protects life online. Leading companies worldwide choose Akamai to build, deliver, and secure their digital experiences — helping billions of people live, work, and play every day. Akamai Connected Cloud, a massively distributed edge and cloud platform, puts apps and experiences closer to users and keeps threats farther away.


