Spear-phishing campaigns may result in significant loss of data, money, reputation, customers, and business opportunities.
Block spear-phishing attacks with a multilayered defense
Spear-phishing campaigns account for some of the most devastating cyberattacks in history. In a spear-phishing attack, cybercriminals send a message to a target or victim that seems to come from a trusted source, encouraging the victim to take quick action. These attacks are typically designed to dupe the victim into revealing sensitive information, wiring money to a fraudulent account, sharing credentials or credit card numbers, or clicking on a link that downloads malware.
Criminals conducting spear-phishing attacks use social engineering techniques to take advantage of human nature and human error, making these exploits among the most difficult to identify and block. As companies put up increasingly sophisticated defenses, phishing scams have evolved from simple business email-based campaigns to efforts that involve mobile devices, text messages, and social media, giving threat actors more options when it comes to targeting their victims.
Akamai offers a suite of IT security solutions that enables you to adopt a multilayered approach to defending against spear-phishing attacks. By turning expert threat research into automated protection against evolving threats, Akamai helps your organization to be ready for anything, and to protect clouds, apps, APIs, and users without slowing your business down.
The anatomy of a spear-phishing attack
Spear-phishing attacks involve two things: a lure and a landing. The lure is designed to capture the attention of a victim by issuing a warning, an urgent request, or sending a message that is full of alarm or concern. The victim’s response leads to the landing, which may be malicious attachments or malicious links, a cloned website, a fake retail portal, or a web form requesting information.
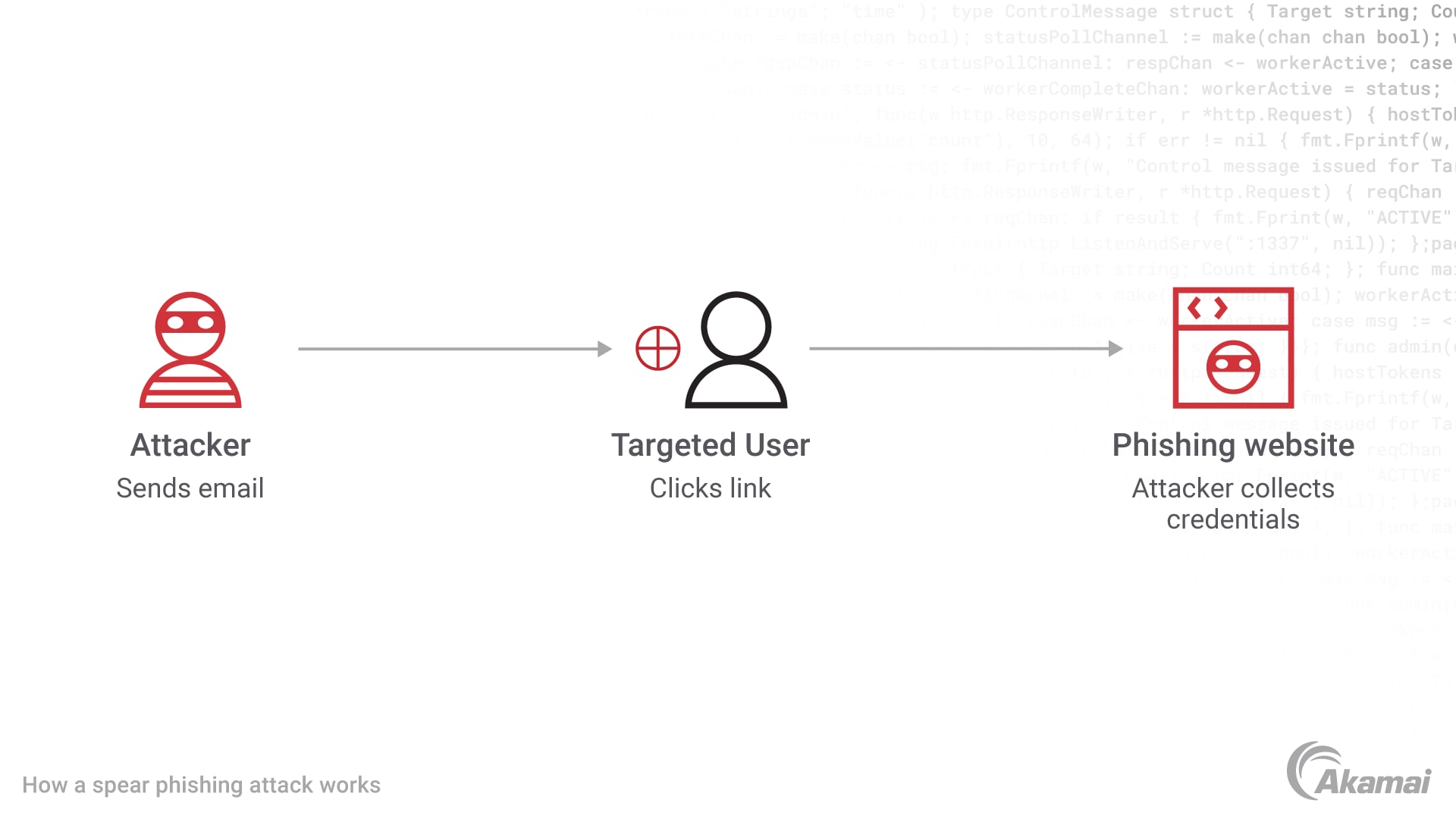
Spear phishing is often called a social-based attack because the lure is designed with information that exists in the public domain. Hackers may use information from public websites and social media to craft a spear-phishing email that appears to come from a well-known source and that references enough specific and credible information to be trusted by the victim or target organization.
When a victim is duped into responding to a spear-phishing message, a variety of adverse events can take place. Some campaigns are designed to land a malicious payload such as ransomware or malware. Other attacks are designed to steal confidential information like login credentials, allowing criminals to access corporate networks and steal sensitive information. Some attacks are geared toward getting employees in the financial department to transfer funds to an account they believe to be legitimate.
Security awareness training can help to prevent spear-phishing attacks by familiarizing employees with targeted attack methods. But since a single failure to recognize a suspicious email can result in an attack of devastating proportions, businesses also need end-to-end security solutions that can recognize and block a wide range of phishing attempts.
Prevent spear-phishing attacks with Akamai
Akamai offers a comprehensive platform with cybersecurity solutions that address our customers’ biggest threats. The breadth of our technology enables customers to adopt the most effective security capabilities while working with fewer vendors.
Akamai security solutions are highly differentiated and recognized as best-in-class technologies for protecting critical assets like websites, applications, data, and access. When defending against spear-phishing attacks, companies may adopt a wide range of Akamai offerings.
App & API Protector
As a holistic web application and API protection solution, Akamai App & API Protector defends entire web and API estates with technical functionality that is designed for customer-focused automation and simplicity. A new adaptive security engine is at the heart of this solution, which brings together industry-leading technologies in web application firewall, API security, DDoS protection, and bot mitigation.
Edge DNS
Akamai Edge DNS is a cloud-based DNS solution that improves DNS responsiveness, ensures 24/7 availability, and has the resilience to defend against the largest DDoS attacks. With Edge DNS, you have access to DNS servers in more than 1,000 points of presence worldwide through the Akamai Connected Cloud, our scalable globally distributed platform. Edge DNS can be implemented as a primary service to replace current technology, or as a secondary DNS service to augment existing infrastructure.
Akamai Guardicore Segmentation
Akamai Guardicore Segmentation provides the simplest, fastest, and most intuitive way to enforce Zero Trust principles within your IT environment. By using machine learning to visualize activity throughout your digital ecosystem, you can implement precise microsegmentation policies to detect possible threats to network security quickly and stop attacks that spread via lateral movement. This Akamai solution makes it easy to implement policies with just a few clicks using AI recommendations, templates for remediating ransomware, and precise workload attributes like processes, users, and domain names.
Akamai MFA
Akamai MFA is a next-generation solution for multi-factor authentication that is impervious to phishing and spear phishing. Leveraging FIDO2, the strongest standards-based authentication method available, Akamai MFA secures the authentication process with end-to-end cryptography and a sealed challenge/response flow. By coupling this proven security with the familiar and frictionless user experience of a mobile push — rather than with cumbersome physical security keys — Akamai reduces risk while improving the user experience.
Akamai Account Protector
Akamai Account Protector is designed to prevent fraudulent human impersonation logins and to mitigate the sophisticated adversarial bots that operate as part of an account takeover attempt. This solution studies and understands the behavior of legitimate account owners, then assesses the risk of each authentication request based on anomalies from typical behavior. With Account Protector, you can know which interactions are legitimate while reducing friction for users and protecting them from fraudulent activity like spear-phishing attempts.
Akamai Managed Security Service
When you want to increase your security posture to better defend against threats like spear-phishing techniques, Akamai Managed Security Service (MSS) provides dedicated security experts with the scale to protect your organization against the largest attacks – while allowing your teams to stay focused on your business.
With Akamai MSS, you can rest assured that our experts and proven online defenses will help to provide superior security management, monitoring, and mitigation. We proactively monitor security events to enable early threat detection, and we deliver intelligence and actionable insights through advisory reporting. If your company experiences any type of phishing attack or data breach, our teams will implement the appropriate responses to quickly mitigate active threats.
Because the threat landscape is constantly evolving, MSS teams regularly update security configurations to ensure the highest levels of protection. MSS experts map out security strategies that align with business needs while integrating industry expertise and best practices that are backed by the global scale of the Akamai Connected Cloud platform.
Frequently Asked Questions (FAQ)
In contrast to a standard phishing campaign that indiscriminately targets a large number of people and attempts to coax them into revealing sensitive data, spear phishing is directed at a specific individual, group, or organization. An attack usually begins with a spoofed email that appears to be from a trusted source, but is actually designed to collect personal information or infect the recipient’s computer with malware. Spear-phishing messages can be a challenge to identify because they often involve carefully crafted messages that appear to be legitimate.
Spear phishing is a specific and targeted attack on one or a select number of victims, while regular phishing attempts to scam masses of people. In spear phishing, scammers often use social engineering and spoofed emails to target specific individuals in an organization.
Preventing a spear-phishing attack requires a multilayered approach to security, including security awareness programs, multi-factor authentication technologies, diligent patching cadences, a secure web gateway, and other defenses that can stop a variety of attacks that cybercriminals may launch with stolen credentials.
Why customers choose Akamai
Akamai powers and protects life online. Leading companies worldwide choose Akamai to build, deliver, and secure their digital experiences — helping billions of people live, work, and play every day. Akamai Connected Cloud, a massively distributed edge and cloud platform, puts apps and experiences closer to users and keeps threats farther away.

