Akamai powers and protects life online. Leading companies worldwide choose Akamai to build, deliver, and secure their digital experiences — helping billions of people live, work, and play every day. Akamai Connected Cloud, a massively distributed edge and cloud platform, puts apps and experiences closer to users and keeps threats farther away.
What Is Two-Factor Authentication (2FA)?
More businesses today are choosing two-factor authentication solutions to improve the security of workforce logins. This is the result of a startling fact: Nearly 80% of data breaches involve the use of stolen or compromised employee credentials and brute-force logins. Compromised credentials are increasingly being used to create a beachhead for cybercriminals as they deliver ransomware and other forms of malware that can have devastating consequences for business profitability and reputation.
Two-factor authentication provides an additional layer of security by requiring users to log in with more than just a password, which can be easily stolen. This extra cybersecurity measure can drastically reduce incidents of breaches — organizations that use two-factor authentication (2FA) or multi-factor authentication (MFA) solutions are 99.9% less likely to be compromised. Two-factor authentication technology built on the FIDO2 security standard is even more secure, preventing hackers from using phishing attacks and credential stuffing techniques to bypass standard MFA security.
Akamai MFA is an MFA service that provides a strong secondary authentication of a user’s identity for cloud, web-based, SaaS, on-premises, and IaaS applications. By combining FIDO2 security with a frictionless authentication process and easy-to-use authentication methods, Akamai MFA also overcomes the cost and complexity of other two-step verification solutions that require administrators and users to manage physical security keys and additional hardware.
Reducing risk with two-factor authentication
When weighing the options for authentication solutions, it’s important to understand the risk associated with each technology.
Username and password authentication
Businesses that rely only on usernames and passwords for account security are highly vulnerable to a breach. Login details are constantly stolen and harvested by cybercriminals, and often used or sold on the dark web. Hackers may use credential stuffing, password spraying, brute force, keystroke logging, and password reset techniques to gain unauthorized access to online accounts, networks, and systems. Even the most complex, algorithm-generated passwords have inherent vulnerabilities that can threaten enterprise security.
Standard multi-factor or two-factor authentication
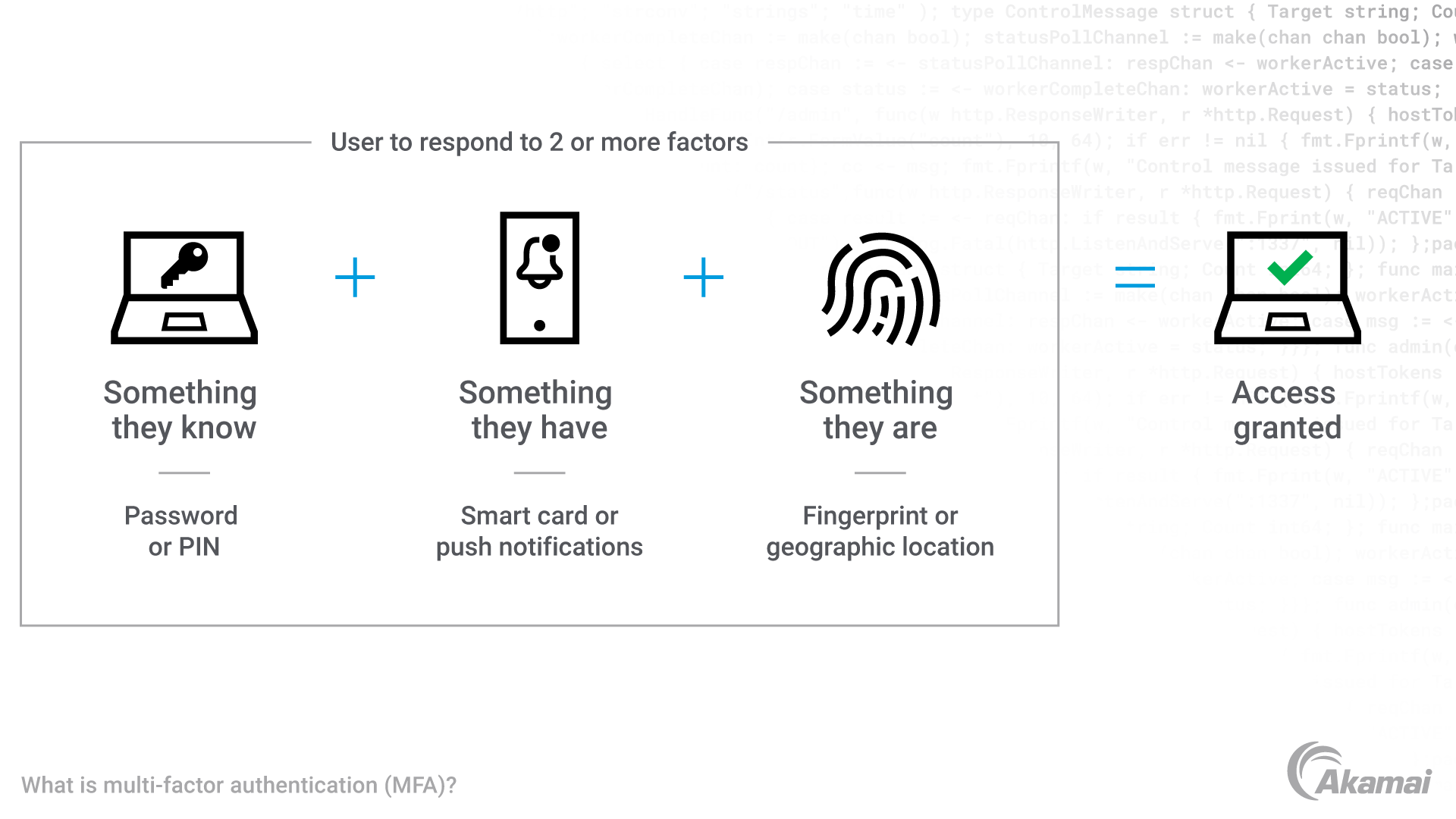
Adding MFA technology to an authentication security stack can immediately improve security and reduce risk. These technologies require users to authenticate on two separate types of factors. The first is typically a password or passcode. The second (or potentially third) factor could be something the user knows, like a PIN or security question; something the user has, like a hardware token or a one-time verification code or push notification; or something the user is, which may involve biometrics like fingerprint scans or facial ID. While it dramatically reduces risk, two-factor authentication is still vulnerable to multiple techniques for bypassing authentication security. These include authentication code interception via email or SMS text messages, use of transparent proxies (machine-in-the-middle attacks), SIM swapping, and social engineering.
FIDO2-based two-factor authentication
Authentication solutions based on the FIDO2 standard, the strongest authentication method in the industry, solve for the security vulnerabilities of traditional two-factor authentication technologies. Using cryptographic login credentials that never leave the user’s trusted device and are never stored on a server, FIDO2 solutions eliminate the risks of phishing, replay attacks, identity theft, and machine-in-the-middle attacks. While these authentication technologies represent the most secure standard, they can be costly and complex to implement. IT teams must invest in the purchase and maintenance of keys for each user, and the complexity of distributing and managing keys can consume a considerable amount of time. Additionally, because users must plug a physical key into their device for every login, this technology inevitably involves a cumbersome user experience.
Two-factor authentication with Akamai MFA
Built on the FIDO2 standard, Akamai MFA is a multi-factor authentication service that delivers the strongest possible security while streamlining management and providing a frictionless end-user experience with a mobile push on the smartphone. This Akamai security system delivers all the benefits of FIDO2-based MFA, but without the costs and complexities of managing physical security keys. Most importantly, Akamai MFA is a phish-proof solution that removes the risk of employees responding to fraudulent push notifications. Security is delivered through end-to-end cryptography and a sealed challenge/response flow.
Features of Akamai’s two-factor authentication technology include:
- Phish-proof authentication, delivering unrivaled FIDO2 security via a frictionless push notification.
- Easy integration with market-leading IdP and identity solutions to provide a seamless MFA service.
- Authentication event reporting through a set of rich reporting features that enable administrative teams to stay on top of authentication events.
- A choice of multiple authentication factors to support specific use cases, including phish-proof push, standard push, TOTP, and SMS.
- User enrollment options that reduce the burden on administrators and providers by allowing users to enroll and register new devices via several low-friction, self-service methods.
- Automated user provisioning workflows using SCIM to ensure that changes in the directory are reflected immediately.
Benefits of Akamai MFA
Akamai MFA enables users to authenticate quickly and easily using a mobile app on their smartphone. When a user provides their username and password to a primary authenticator such as Microsoft Azure AD, the Microsoft authenticator validates the credentials and connects to Akamai MFA to generate a second factor. Akamai renders a page that allows the user to select an authentication factor and sends a phish-proof push to the user’s mobile device. Once the user responds, Akamai MFA returns control to the primary authenticator, which grants the user permission to access the requested applications or services.
With Akamai MFA, businesses can:
- Reduce risk by deploying authentication technologies based on the strongest security standards available
- Lower total cost of ownership (TCO) by authenticating through existing smartphones and web browsers, with no need to purchase, replace, and maintain additional hardware
- Ensure a frictionless user experience that allows users to authenticate with familiar push notifications
- Implement two-factor authentication quickly and easily using the time-based Akamai MFA authenticator app on existing smartphones
- Support the organization’s move to Zero Trust networking and SASE security frameworks