Akamai powers and protects life online. Leading companies worldwide choose Akamai to build, deliver, and secure their digital experiences — helping billions of people live, work, and play every day. Akamai Connected Cloud, a massively distributed edge and cloud platform, puts apps and experiences closer to users and keeps threats farther away.
The dangers of a zero-day attack
A zero-day attack is a particularly dangerous attack vector that targets a software vulnerability that a developer is not aware of. This means the developer has not yet had time to address the weakness or create a security patch for it. As a result, when the attack occurs, the developer has “zero days” to develop a fix for the vulnerability.
To help organizations combat zero-day attacks, Akamai offers a broad suite of end-to-end cybersecurity solutions that take a holistic approach to defending websites, applications, APIs, and network infrastructure from a broad range of risks and security threats. Implementing these protections in an always-on posture and having virtual patching capabilities allows organizations to reduce their attack surface, and quickly mitigate zero-day attacks.
How a zero-day attack works
Even though software developers are constantly checking their products for flaws and providing software updates, many applications are released with vulnerabilities that, when found, can be exploited by attackers to steal data or money, cause business disruption, or launch more sophisticated and devastating attacks. Before a vulnerability is discovered by a software vendor like Microsoft or Apple, attackers may spend days or months taking advantage of this weakness for their own gain. Malicious hackers may even sell information or functionality about zero-day vulnerable systems on the dark web to other cybercriminals.
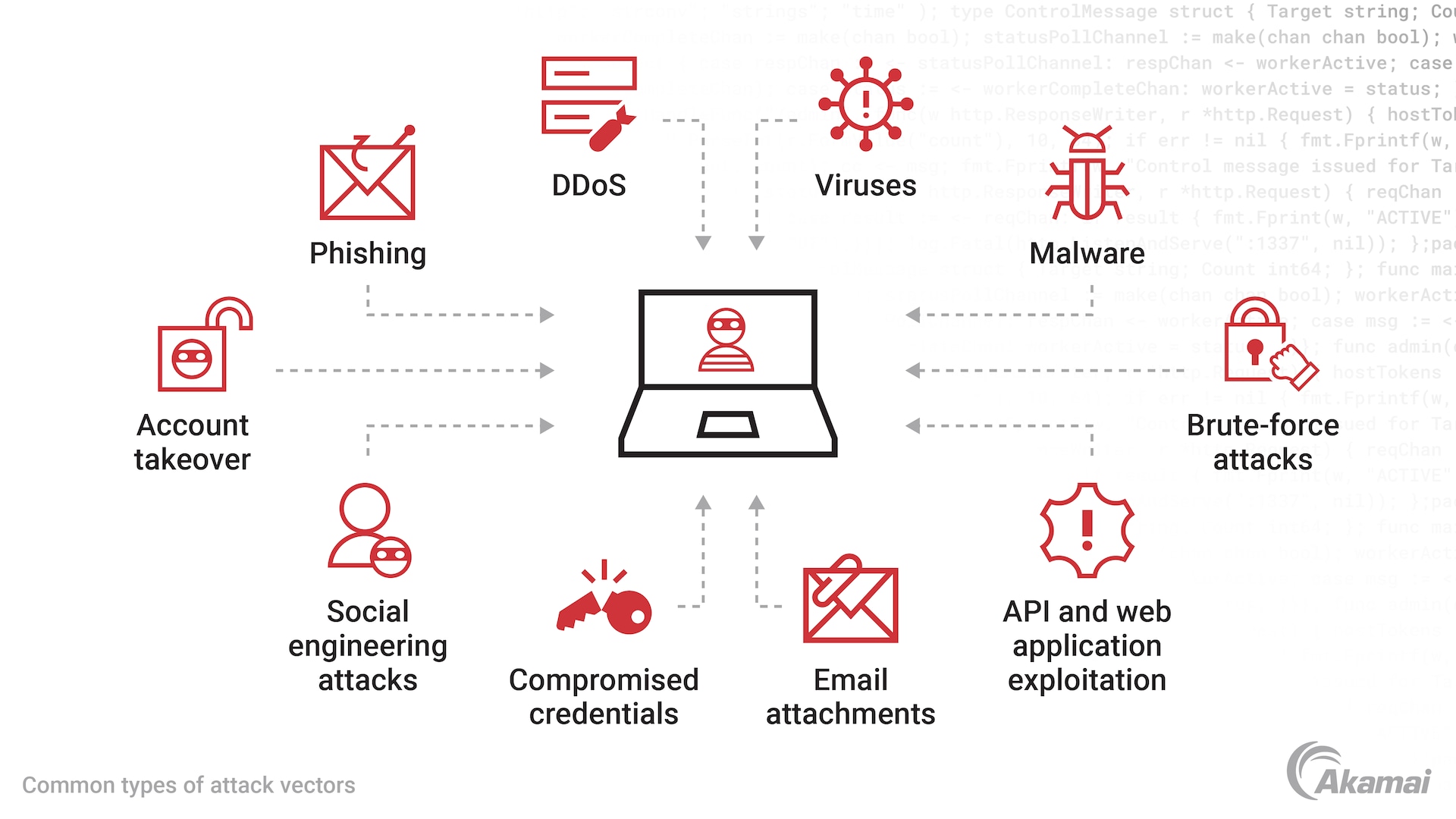
Zero-day attacks can take advantage of many types of vulnerabilities — including buffer overflows, broken algorithms, URL redirects, SQL injection, and password security issues. With a zero-day exploit, threat actors may access a machine to steal money or sensitive data, disrupt operations, or hijack the machine as part of a botnet designed to launch distributed denial-of-service (DDoS) attacks.
Because a DDoS attack based on zero-day vulnerabilities exploits weaknesses that are unknown to a software manufacturer and its customers, it is very difficult to defend against. The best strategy is to adopt a multilayered defense that protects against the various methods malicious actors may use to exploit a zero-day vulnerability in cybercrime. These include defenses against ransomware, malware, viruses, botnets, API-based attacks, SQL injection, and other common yet dangerous attack vectors.
Defend your environment with Akamai
Akamai defends against zero-day attacks, DDoS attacks, and other threats with a collection of industry-leading security solutions powered by deep visibility into evolving threats. Our solutions act as a first line of defense, providing protection with dedicated edge, distributed DNS, and cloud mitigation strategies that stop attacks before they reach applications, data centers, and infrastructure.
Akamai App & API Protector is one of our most powerful solutions for defending against zero-day attacks. App & API Protector defends entire web and API estates with a holistic set of powerful protections purposely built with customer-focused automation and simplicity. Designed with some of the most advanced security automation available today, this Akamai solution combines industry-leading technologies in web application firewall, DDoS and DoS protection, bot mitigation, and API security in a single solution that is easy to use.
Features of App & API Protector
Advanced API capabilities. Automatically discover a full range of known, unknown, and changing APIs across your web traffic, enabling you to protect against hidden cyberattacks, find errors, and reveal unexpected changes. All API requests are automatically inspected for malicious code and zero-day malware.
Bot visibility and mitigation. Monitor and mitigate bot attacks with real-time visibility into bot traffic and access to a directory of more than 1,500 known bots.
DevOps integration. Akamai APIs provide the ability to manage App & API Protector via code, enabling rapid onboarding, uniform management of security policies, and centralized enforcement across cloud infrastructures.
Seamless scalability. App & API Protector seamlessly scales to match traffic demands over time, distributing CPU and memory resources as required to deliver cached content from the edge and provide continuous protection without interruption.
Automatic updates. Akamai security researchers analyze more than 300 TB of daily attack data to identify new vectors or permutations of existing ones. The adaptive security engine that powers App & API Protector is automatically updated with threat insights, minimizing administrative overhead and operational friction.
DoS/DDoS protection. Network-layer DDoS and DoS attacks — including ICMP flood, UDP flood, and SYN flood attacks — are instantly dropped at the edge. Application-layer attacks are quickly mitigated within seconds.
Network lists. Use network lists to block or allow traffic coming from a specific IP, subnet, or geographic area.
Custom rules. Create custom rules using an easy-to-use rule builder to manage unique scenarios not covered by standard protections.
Dashboards, learning, and reporting tools. Access detailed attack telemetry and analysis of security events. Create real-time email alerts using static filters and thresholds. Leverage reporting tools to continually monitor and assess effectiveness.
Additional Akamai security solutions for mitigating zero-day threats include:
Prolexic
Akamai Prolexic is purpose-built to stop DDoS attacks in the cloud, before they reach data centers, applications, and internet-facing infrastructure. With Prolexic, network traffic is directed to one of 20+ global high-capacity scrubbing centers where the Akamai Security Operations Command Center (SOCC) deploys proactive and/or custom mitigation controls to stop cyberattacks instantly.
Edge DNS
Akamai Edge DNS is a cloud-based solution that delivers 24/7 DNS availability while improving DNS responsiveness and delivering the resilience required to defend against the largest DDoS attacks. Edge DNS leverages Akamai Connected Cloud, with thousands of DNS servers in more than 1,000 points of presence worldwide providing a high level of DNS service availability.
Benefits of Akamai security solutions
When implementing Akamai security solutions for mitigating zero-day threats, you can count on:
Broad protections from a single platform. In addition to Akamai App & API Protector, Akamai offers additional security solutions such as Prolexic, a cloud scrubbing service; Edge DNS, a cloud-based solution that improves DNS responsiveness and resiliency; Akamai MFA, a multifactor authentication solution; and Bot Manager, a solution that detects and mitigates bots where they make initial contact.
Proactive mitigation controls. Akamai reduces attack services and stops the largest attacks without compromising quality of mitigation.
Frictionless maintenance. Automatic updates help IT teams maintain strong security while automatic self-tuning alleviates alert fatigue, allowing teams to investigate real attacks rather than chasing false alerts.
Reduced risk. Proactive mitigation controls stop more than 80% of attacks with a zero-second SLA.
- Resilient DNS services. Enjoy faster, more reliable DNS resolution with guaranteed 24/7 availability.
Frequently Asked Questions (FAQ)
A zero-day attack is when malicious actors gain access to a system or network by exploiting a security vulnerability or weakness in a software program that the software manufacturer does not know about, leaving them “zero days” to fix the problem.
DDoS attacks are distributed denial-of-service attacks that use a network of infected computers (called a botnet) to target a system, network, or server in an effort to render it unavailable to legitimate requests or users. A DDoS attack may be referred to as a zero-day attack when malicious actors use new methods that have not previously been seen by security teams and analysts. Zero-day attacks can also help attackers to hijack the computers that will become part of a botnet.