Zero Trust Security
One platform for comprehensive coverage, deep visibility, and granular control
Why Zero Trust security?
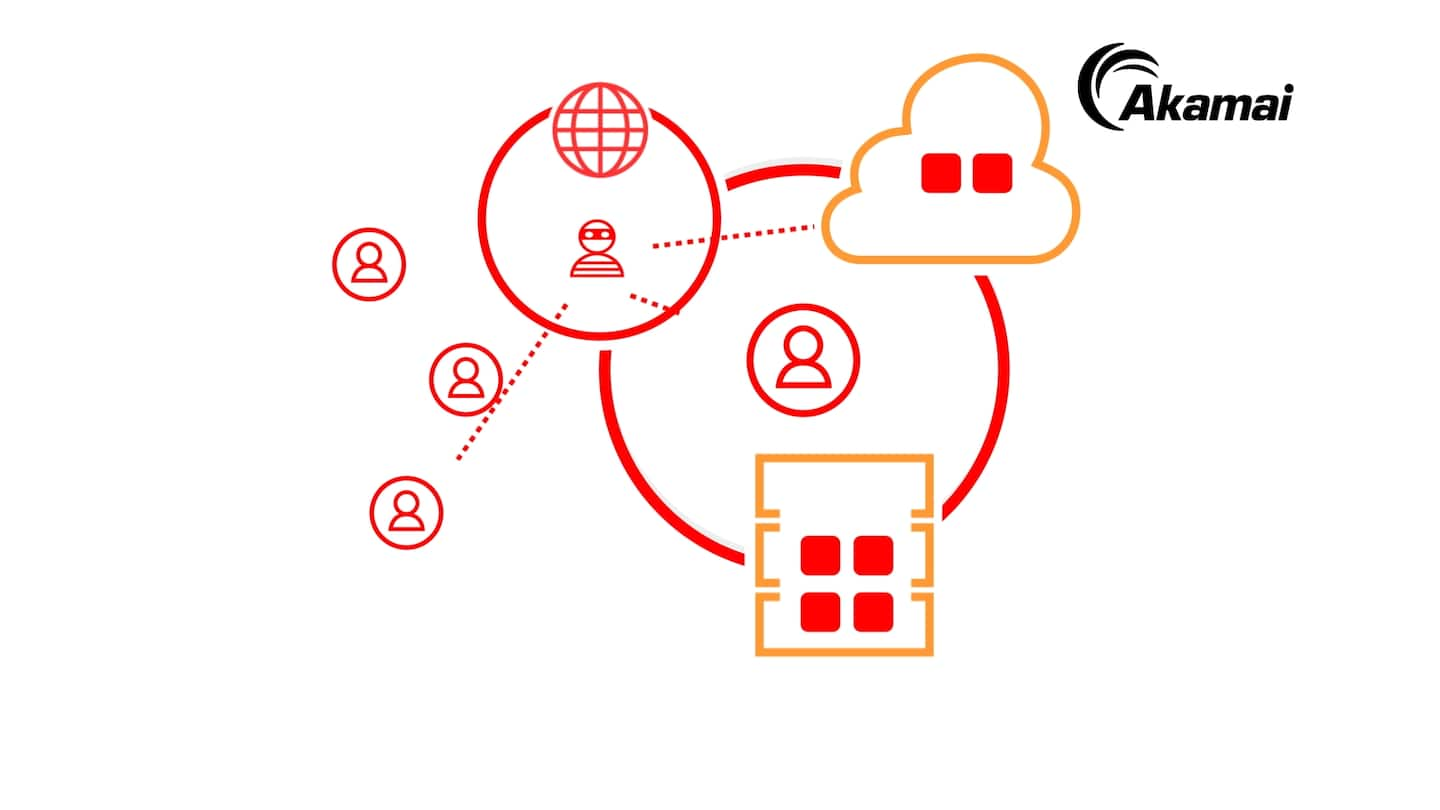
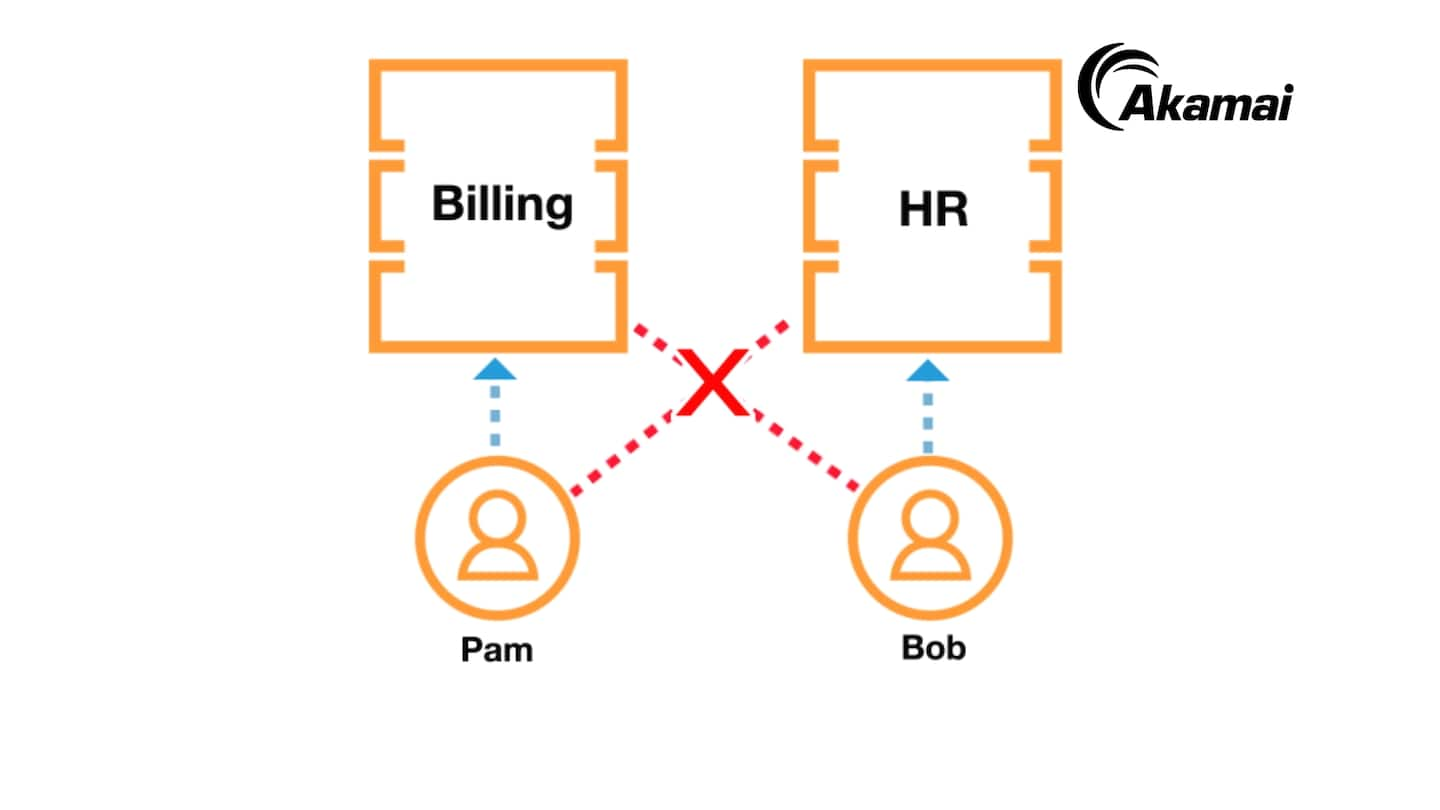
End your dependence on firewalls and VPNs for network security. Akamai’s Zero Trust solutions secure your entire IT environment, whether it’s on-premises or cloud; your apps, whether they’re legacy or SaaS; and your employees, whether they’re on-site or remote.
Akamai’s visibility into your assets, access, and network flows provides a foundation for your Zero Trust security strategy. And our global expertise can help you hunt down the most evasive threats and limit lateral movement in the event of a breach.
How Zero Trust works
Address your pressing security challenges with Zero Trust

2023 Gartner® Market Guide for Microsegmentation
See how Gartner® views the latest trends, use cases, and market direction
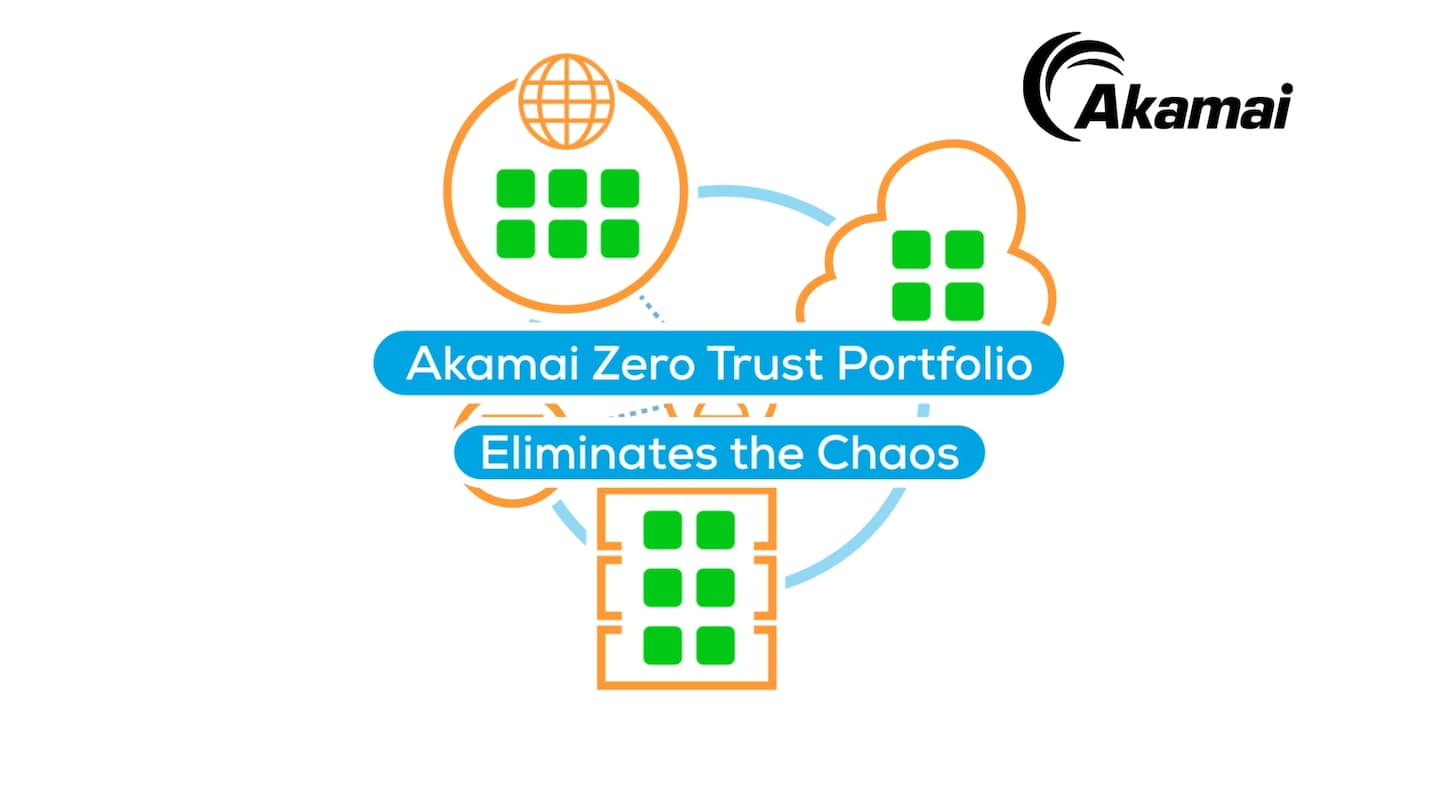
Get started with Zero Trust security
Simplify and secure your enterprise with these Akamai products