To download the Infection Monkey, please submit the form at right. We will provide you with the files and an installation guide.

Continuously test your network security and use the insights to make informed security decisions based on real data, not speculations.
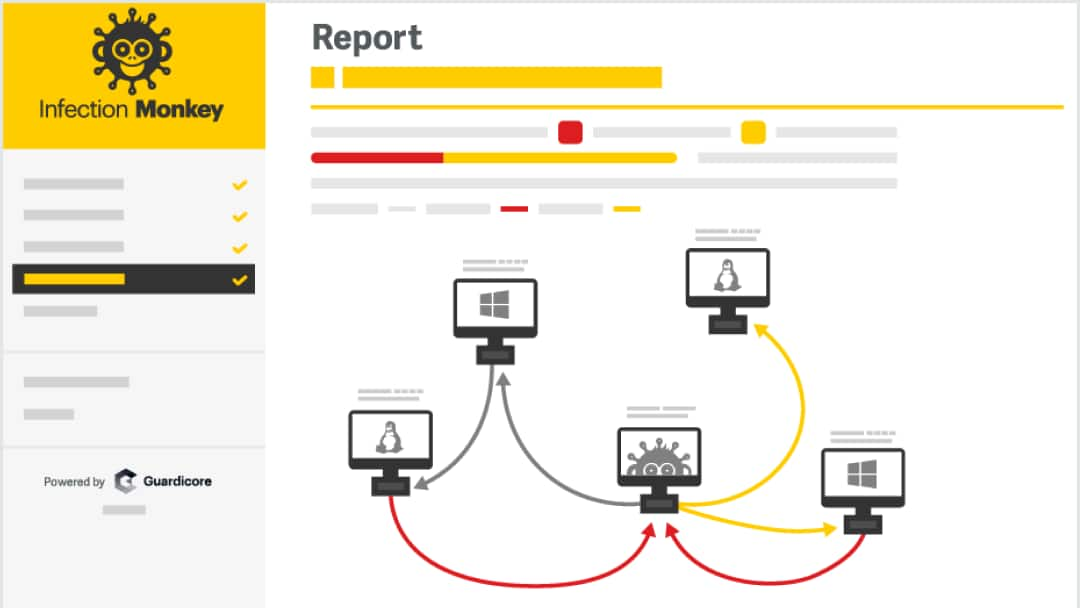
The Infection Monkey is an open-source breach and attack simulation (BAS) platform that helps you validate existing controls and identify how attackers might exploit your current network security gaps.
The Monkey is used in some of the largest enterprises down to the smallest organizations, and it was tested by more than 100 companies with 5,000+ servers.
Security testing at no additional cost
Developed under the GPL v3 open source license
Ongoing networkwide security testing
Simulates post -breach lateral movement
Test your new POC by running Monkey prior to your purchase
Network map from the attacker’s point of view
Supports containers, public and private clouds
Ready-made installer for every environment
Automatically handles network regardless of size
To download the Infection Monkey, please submit the form at right. We will provide you with the files and an installation guide.