
Security Solutions
Embed strong security everywhere your business meets the world

Get the Lowdown on the Latest Cyberattacks
In this unique monthly webcast series, the Akamai Security Intelligence Group (SIG) will go over the most notable threats and the coolest security research that has hit our radar in the past 30 days.
Keep pace with threats as your attack surface grows
Increasing security attacks, whether cloud-based or on premises, mean you need to build security into everything you create — anywhere you build it and everywhere you deliver it. Our solutions leverage our global security platform to protect your unique environment and all of its critical applications, so you can confidently innovate and expand your business, without creating new vulnerabilities.
Strengthen your security posture
Innovate faster while lowering security risk, knowing your protection is evolving faster than threats — or your competition.
Free up your security team to focus on business
Focus human efforts on top workflows, knowing our solutions help you plan for and respond to zero-day events.
Gain insight on emerging threats
Leverage our visibility into global attacks to prepare for threats that may affect your business.
Security Products
- Secure Apps and APIs
- Enable Zero Trust
- Stop DDoS and DNS Attacks
- Prevent Abuse and Fraud
- Get Active 24/7 Support
Secure Apps and APIs
Protect applications with strong security
Enable Zero Trust
Prevent breaches and spread of malware
Stop DDoS and DNS Attacks
Protect your sites and customer experience
Prevent Abuse and Fraud
Maintain your brand reputation
Get Active 24/7 Support
Add a fully managed service
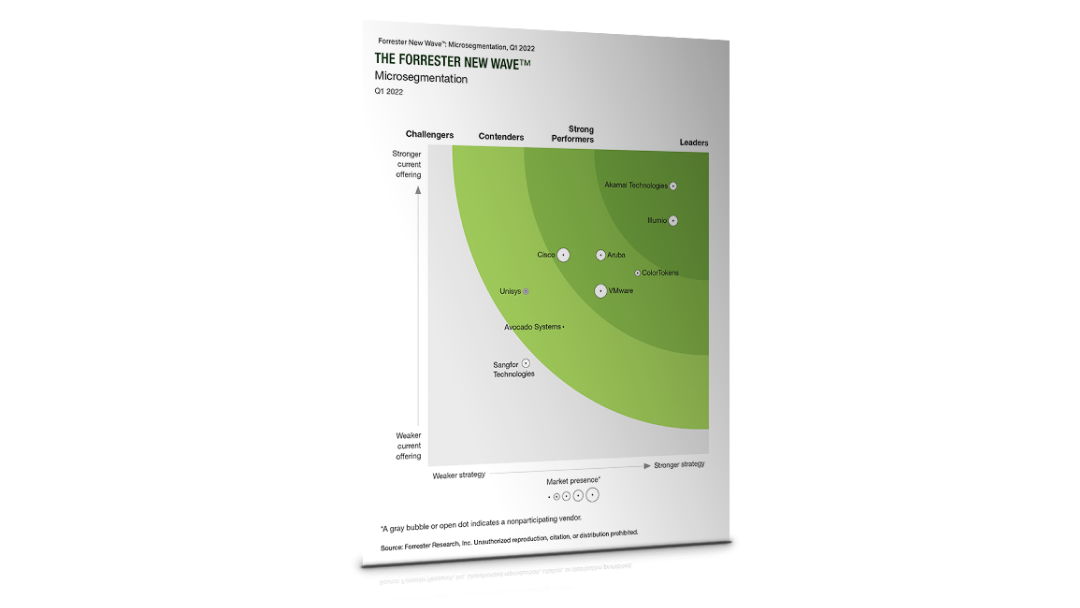
Learn why Forrester named Akamai Guardicore Segmentation a Leader
Gain insight on the latest attack vectors with Akamai Security Research
Timely analysis of global threat data, with actionable guidance to help you spotlight security risks and strengthen your posture

